Overview
https://learn.microsoft.com/en-us/training/modules/storage-security/
- Define data sovereignty and how that is achieved in Azure
- Configure Azure Storage access in a secure and managed way
- Encrypt your data while it is at rest and in transit
- Apply rules for data retention
Define Data Sovereignty
Data sovereignty is the idea that the digital data is still bound by the laws of the land in which it exists.
Each region is paired with another region making "paired regions"
Benefits of paired regions:
- physical isolation - each datacenter is 300 miles from the nearest.
- platform provided replication
- region recovery priority - one of the paired regions has a higher priority than the other so that region specific recovery can be restored quicker.
- Data residency
- Sequential updates
Configure Azure Storage Access
- Entra ID authentication - use this whenever possible. MS recommended authentication
- Shared Key
- Shared access signatures (SAS)
- Anonymous and public access to the blobs.
Deploy Shared Access Signatures
- Service Level
- Account Level
Architecture usually looks like this:
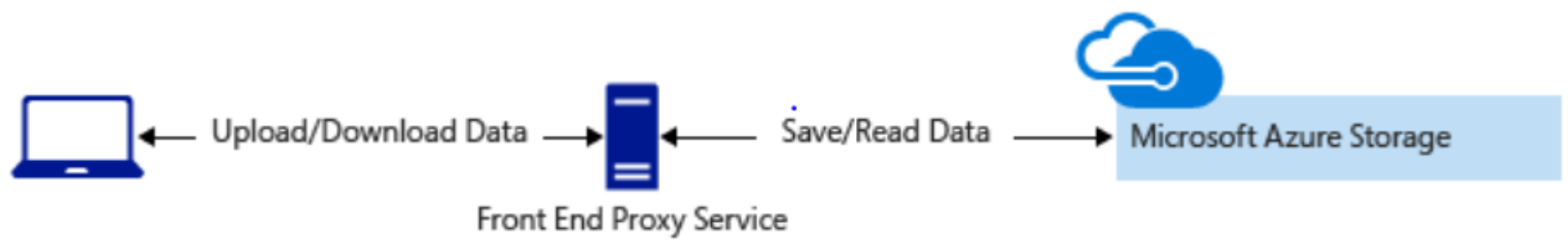
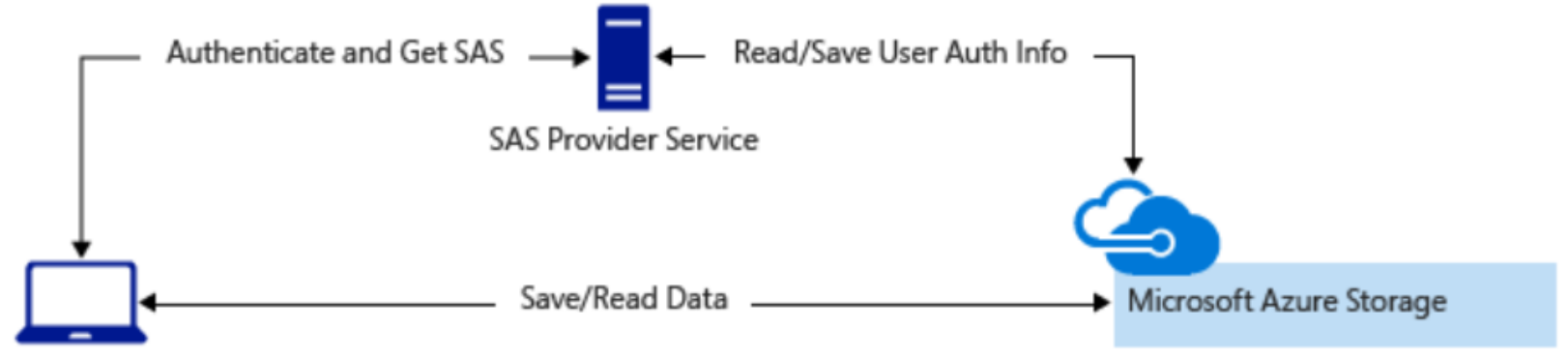
And if you don't want to route through the front end proxy:
Manage Microsoft Entra storage authentication
Storage Blob Reader
Implement Storage service encryption
All data automatically encrypted using SSE Azure Disk Encryption Data in transit encrypted using HTTPS or Client Side Encryption
Azure Storage Encryption is used by default when the data is at rest. It cannot be turned off.
Microsoft Managed Keys - MMKs Customer Managed Keys - CMKs
Blob data retention policies
Immutable storage can be enabled on Azure Blob storage. WORM policies (Write once, read many) can be on all tiers. Users can place data in the respective tier and the data can remain immutable.
- Time based
- Legal Hold
Container level configuration Auditing and logging.
Note: Containers can have both a time based AND legal hold policies enabled on them at the same time.
Configure Azure files authentication
SMB shares retain the ACLS from the Windows share.
Identity based authentication - AD DS via Microsoft Entra ID authentication
Enable Secure transfer
You can block any transfer of data to the Azure Files unless it is secure over HTTPS or SMB 3.0 with encryption.