Overview
https://learn.microsoft.com/en-us/training/modules/sql-database-security/
- Configure which users and applications have access to your SQL databases
- Block access to your servers using firewalls
- Discover, classify, and audit the use of your data
- Encrypt and protect your data while is it stored in the database.
Enable SQL database authentication
Authentication is when you prove that the identity signing in is the actual identity. Authorization is what that proven identity is allowed to do.
SQL Database Authentication - accounts that are on the SQL database itself Microsoft Entra ID - Using MS AAD to authenticate to the database.
Configure SQL database firewalls
By default, all access is blocked by the SQL database firewall.
You have server level firewalls and database level firewalls. Server level allow access to the entire SQL server, while database level firewalls allow access to only the SQL databases.
Best practice is to use Database level firewalls and reserve the usage of server level firewalls to administrators.
SQL Database Auditing
Server Level or Database Level Retain logs Store them in LA or another storage account Audit those logs Alerts
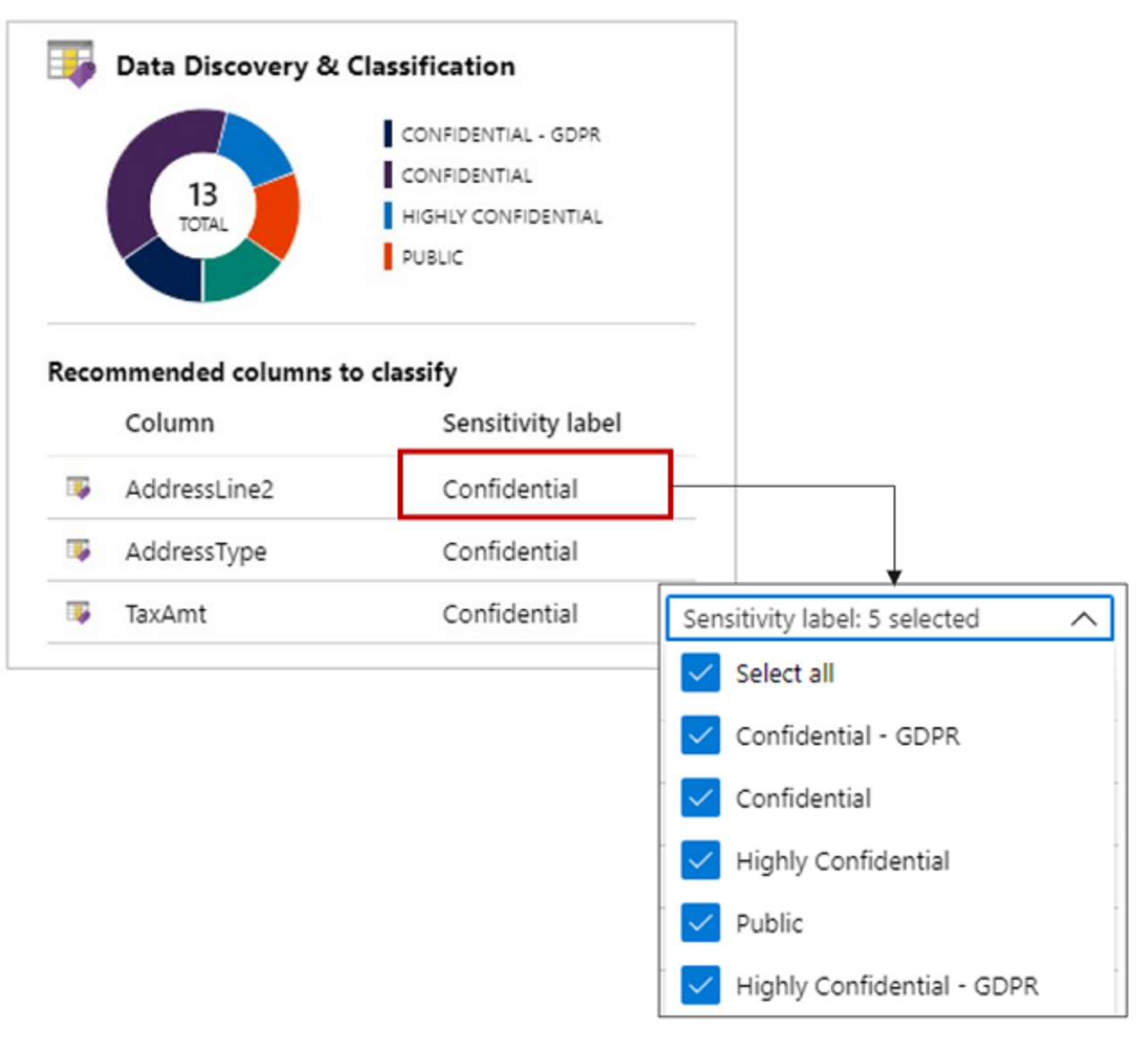
Implement data discovery and classification
Azure looks through all the data (when enabled) and classifies each piece of data according to what it believes it is.
Unstructured data vs structured data.
Azure Data Encryption for data at rest. SSL/TLS encryption for data in transit.
- Discovery and recommendations - identifies and recommends changes to your data.
- Labeling - properly setting column labels to your data
- Query Result Set Sensitivity - calculated in real time to provide accurate auditing.
- Visibility -
Customization of your data discovery policy is set at the Tenant level of your hierarchy in your Microsoft Defender for Cloud. Enable this policy and then fine tune at the database level.
Microsoft Defender for SQL
- Vulnerability Assessment - It highlights deviations from best practices, such as misconfigurations, excessive permissions, and unprotected sensitive data.
- Advanced Threat Protection - Detect and respond to threats in real time to your database architecture.
Explore detection of a suspicious event
So what happens when you do get an alert for a suspicious event? It will give you details about the security alert, as well as remediation steps tailored to that specific alert.
Vulnerability Assessment Express and Standard configuration
Express - without a dependency on a storage account Standard - with a dependency on a storage account
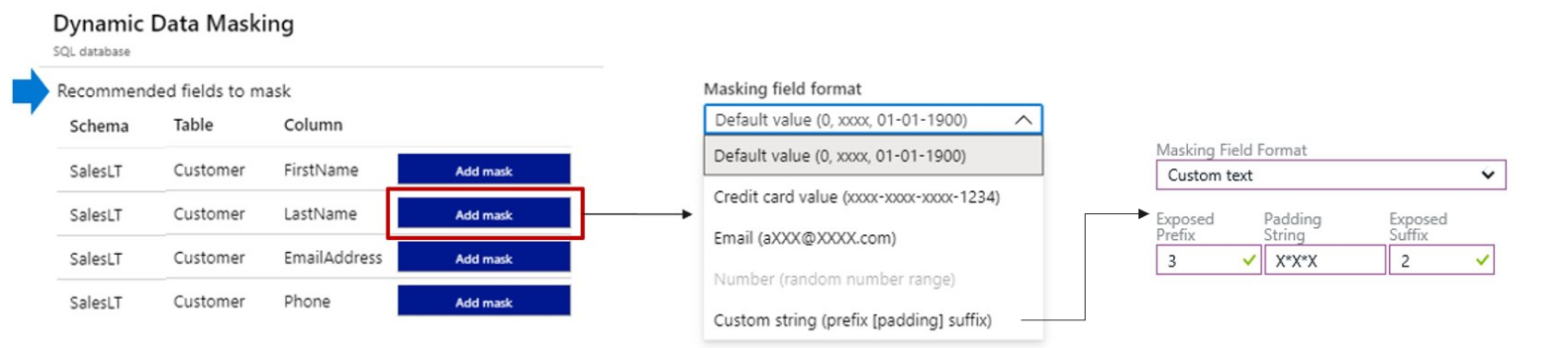
Dynamic Data Masking
Dynamically mask certain fields on the fly, leaving administrators access to unmasked data.
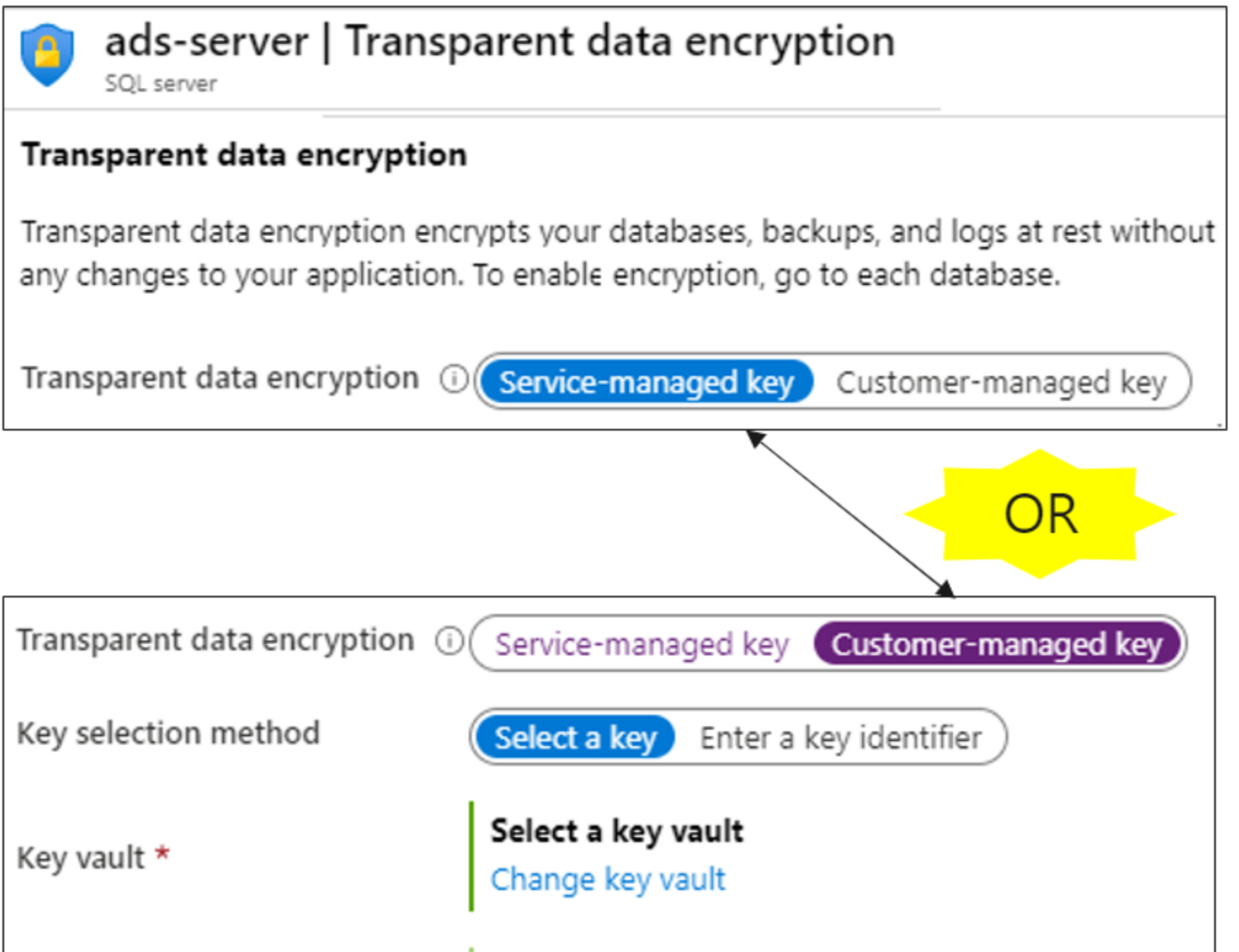
Implement transparent data encryption
TDE is enabled by default for all newly deployed SQL databases.
- Service Managed
- BYOK for TDE Encryption.
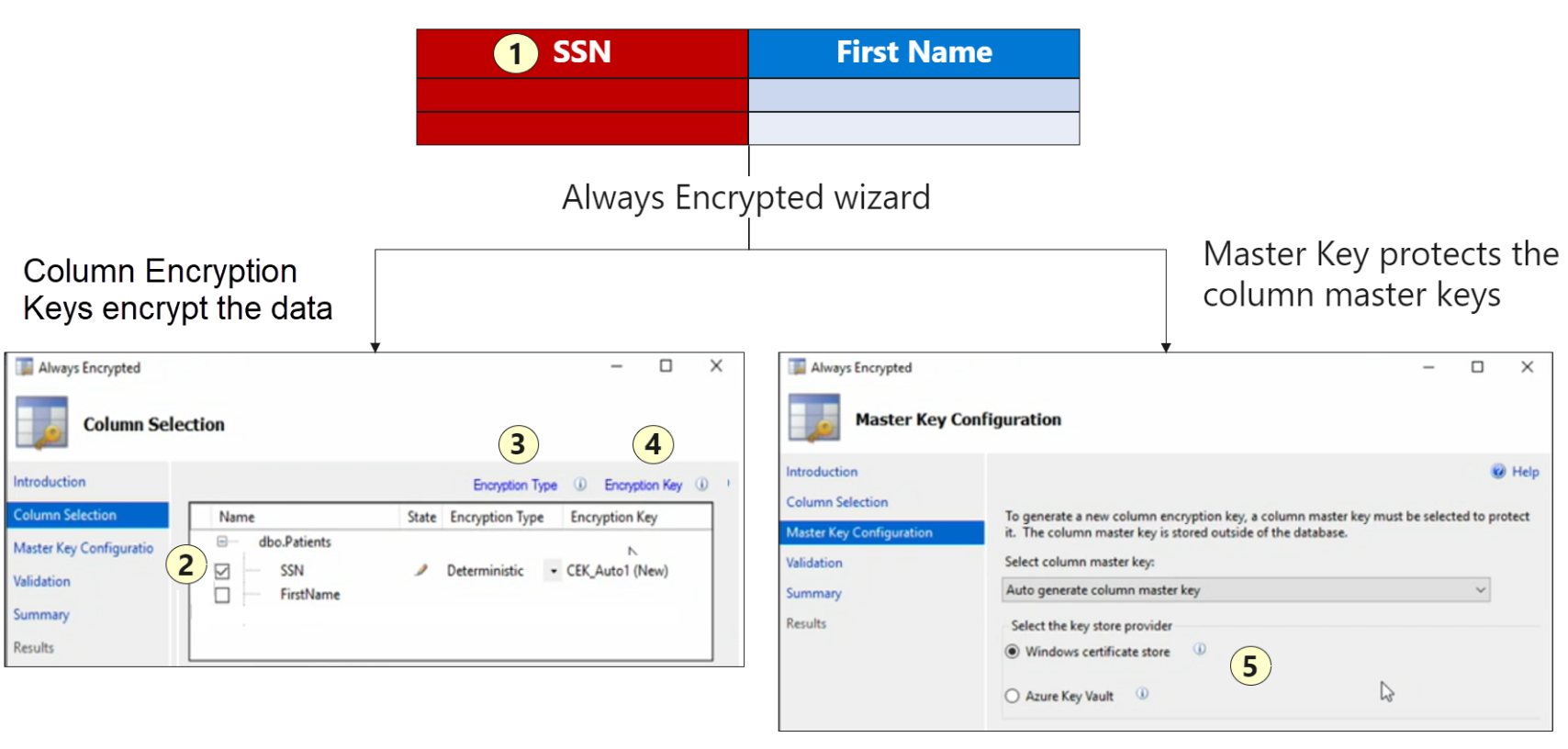
Deploy always encrypted features
This allows the client application to use encrypted data outside of the SQL database. This is the safest approach, never allowing the data to be decrypted outside of the application.
- Deterministic Encryption - specific encryption for specific data.
- Randomized Encryption - Less predictable