Part 2: Implement Platform Protection
https://learn.microsoft.com/en-us/training/paths/implement-platform-protection/?source=docs
Implement Perimeter Security
- Define defense in depth
- Protect your environment from denial-of-service attacks
- Secure your solutions using firewalls and VPNs
- Explore your end-to-end perimeter security configuration based on your security posture
Defense in depth
Layers of control at each of these levels:
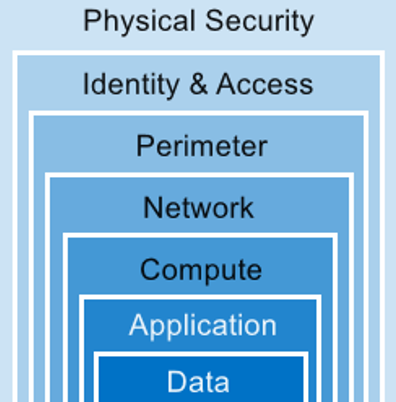
Software defined networking and software defined data center (SDDC) technologies are important.
Network Microsegmentation
Creating secure zones in data centers and Azure deployments that allow you to isolate workloads Zero Trust is best practice.
- NSGs - layer 3 and 4 connectivity
- ASGs - define fine grained policies based on workloads centered around applications.
- WAF and Firewall can be used for advanced network access that requires application layer support.
- LAPS for admin passwords and JIT access to them.
Explore VNet security
Azure networking components:
- VNET
- Subnets
- IP Addresses
Supports WAN link connectivity to your on prem network and Azure via ExpressRoute
Vnets
- are made up of subnets - each subnet can be in a different availability zone.
- subnets contain a range of IP's that correspond to your network
- Azure provided DNS resolution
IP addresses
Private and public VMs can have more than one network adapter
Enable DDOS protection
One location = DOS Multiple locations = DDOS
- coordinated effort to disrupt a target
- many systems sending traffic
- might not even disrupt services, but could scale up your resources dramatically to handle the load.
Best Practice # 1: ensure that security is a priority through the entire lifecycle of the application. Focus on the 5 pillars of software quality:
- Scalability
- Availability
- Resiliency
- Management
- Security
Best practice # 2: Design your application to meet the demands of an amplified load - a single instance creates a single point of failure
Best Practice # 3: Layer security defenses in an application to reduce the chance of a successful attack.
Configure a DDOS implementation protection
Basic is always enabled as part of the Azure platform on IPv4 and IPv6 addressing Standard provides additional mitigation capabilities tuned to the VNet resources. It reacts by redirecting traffic to the target resource AND then checks the packet to see if it is valid. if it is valid, it rate limits the traffic, if it is not valid, it drops the packet.
Standard can mitigate the following attacks:
- Volumetric - UDP Floods, spoofed floods
- Protocol - SYN floods on the Layer 3 and 4 stack
- Resource Layer attacks - HTTP protocol violations, SQL injection, Cross Site Scripting and other Layer 7 attacks
DDOS protection can protect Layer 3-7.
Azure Firewall Features
- built in HA
- unrestricted cloud scalability
- FQDN filtering rules
- Network traffic filtering rules - fully stateful
- qualified domain tags - Lets say you want to allow Facebook into your network
- OSNAT support
- DNAT support
- Azure Monitor Logging
3 rule types:
- NAT, Network and application with a deny by default.
Azure Storage
Storage has a layered security model, which allows you to secure your storage accounts to a set of supported networks. Set to Allow all networks by default, must be then locked down Authorization is supported by Entra credentials, account key or SAS token Granting access from specific Vnets is supported by service endpoints
Deploy Azure Firewall Implementation
You can control outbound access with application and network rules that filter destination traffic. All traffic is denied by default.
FQDN tags such as Windows Update services can be used to allow the required outbound traffic
Infrastructure qualified domain names - compute, managed disks, Azure Diagnostics and logging
Metrics and logs are near real time for fast issue detection.
Threat intelligence based filtering can be used to alert and deny traffic from known malicious domains. This is sourced from the Microsoft Threat Intelligence feed.
Rule processing logic can be used to configure a range of rules from 100-65000. Lower the value, the more important it is. Deny all is at the very bottom of this logic.
Service Tags represent a group of IP addresses. These are preconfigured by MS.
Remote Work
WFH policies have been the norm as of late. VDI infrastructure in the Azure cloud needs to have protection inbound and outbound from that VDI instance. Azure Virtual Desktop is a Citrix like SaaS platform.
VPN Forced Tunnelling
You are forcing your traffic through a VPN inbound and outbound to your on prem network rather than through the public Internet.
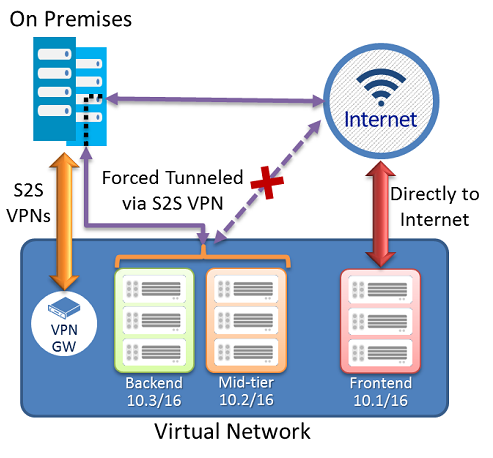
You can then use user defined routes to specify direct paths of traffic flow.
User defined routes
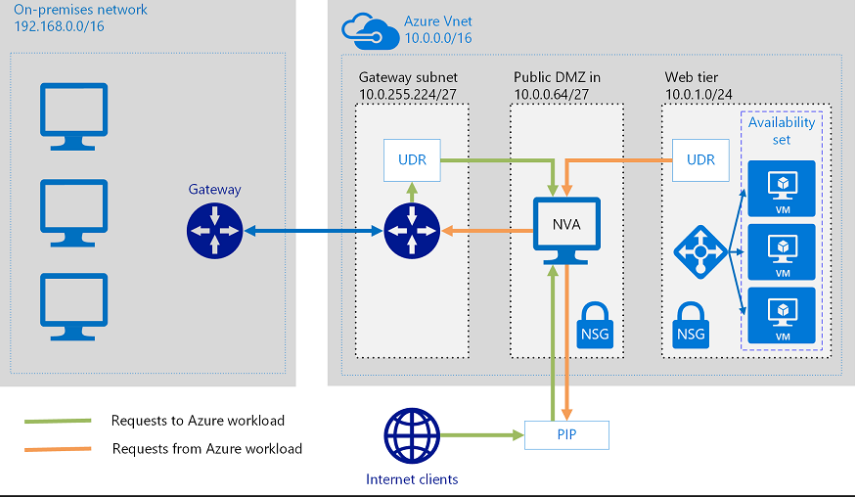
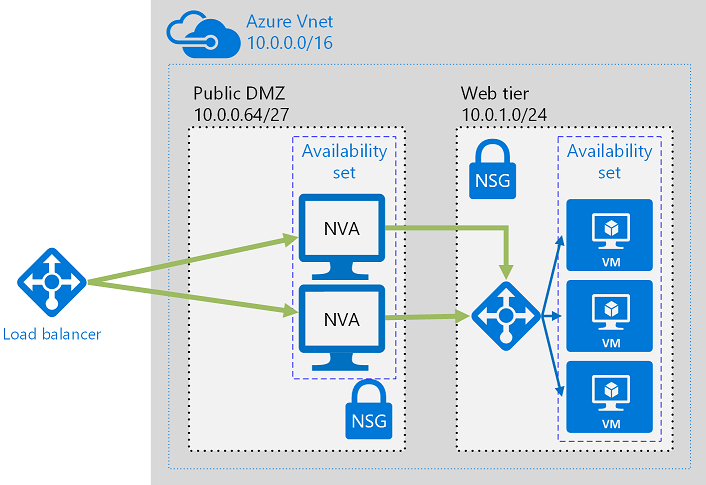
Network Virtual Appliances
NVAs check inbound and outbound traffic. These might live in the public subnet or the public DMZ.
Hub and Spoke Topology
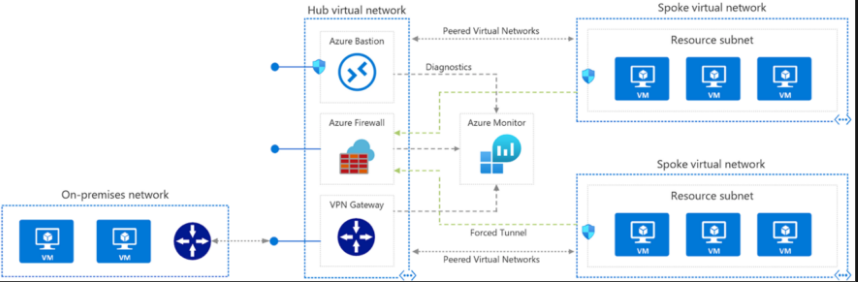
Traffic flows through the on prem network via ExpressRoute to Azure's main VNet, which then has multiple other VNets attached (peered) to it. The ExpressRoute connection is not set up for direct connections to the spoke networks.
Exercises
https://learn.microsoft.com/en-us/training/modules/perimeter-security/11-demonstration
Configure Network Security
- Deploy and configure network security groups to protect your Azure solutions
- Configure and lockdown service endpoints and private links
- Secure your applications with Application Gateway, Web App Firewall, and Front Door
- Configure ExpressRoute to help protect your network traffic
Explore Network Security Groups
NSGs provide security for the VMs that you create via the Classic model or the Resource Manager. Each NSG needs:
- Name -
- Direction - inbound or outbound
- Priority - rules with higher priority apply
- Access - whether the traffic is allowed or denied
- Source IP and Port
- Destination IP and port.
- Protocol - TCP UDP or both
Default rules can be overridden because they are the lowest priority. You can define tags such as Internet, VNET, Load Balancer to them.
Planning NSGs
You can assign them to either subnets or directly to the NICs. You can create isolated subnets with these NSGs
Deploy a NSG implementation
- You can apply 100 NSGs per region per subscription unless you reach out to support for an increase.
- you can apply one NSG to a VM, subnet or NIC
- you can have 200 rules per NSG, raised by Azure support to 500.
- you can apply a NSG to multiple resources
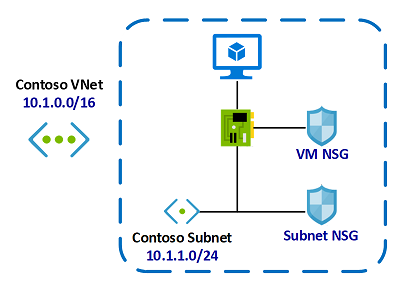 In this example, the subnet NSG is evaluated first and whatever traffic is allowed through will then hit the NSG on the VM. The opposite occurs for outbound traffic.
In this example, the subnet NSG is evaluated first and whatever traffic is allowed through will then hit the NSG on the VM. The opposite occurs for outbound traffic.
How traffic is evaluated
Inbound traffic hits the widest NSG first. If there is no NSG, then the traffic is allowed through unless blocked otherwise by a firewall.
Outbound is the reverse.
Notes: It is recommended to either assign an NSG to a subnet (preferred) or a VM but not both.
If you apply rules to the subnet, it affects the resources inside of the subnet. if you deny all inbound and outbound traffic thinking you can keep two vm's talking to each other inside the subnet, you are wrong. you'd have to write in rules for this.
Application Security Groups
Built on NSGs, you can use application security groups to extend security to an application.
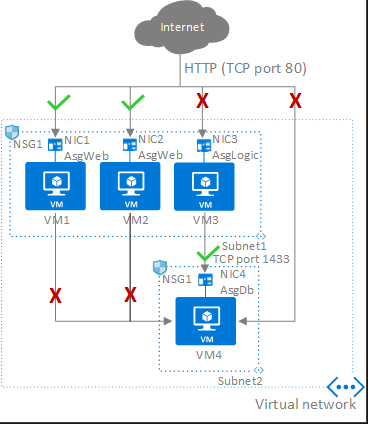
ASGs must:
- exist in the same VNet that the network interfaces that it is assigned to.
Service Endpoints
Sets an IP address in your VNet for a service you are trying to access.
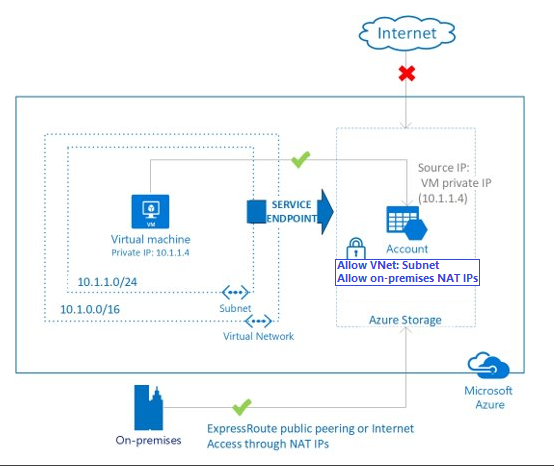
Reasons to use:
- Improved Security
- Optimal Routing
- Endpoints take services from the VNet on the Azure Backbone without traversing the public Internet.
- simple to set up with less overhead. No NAT or gateway devices needed
Watch for Azure Firewall changes when switching from a public IP to a private IP. Traffic won't hit the firewall on service endpoints.
Configure Service Endpoint scenarios
Peered, connected or multiple VNets - You can enable service endpoints on each of the subnets independently and secure Azure services to the subnets.
Filtering outbound traffic from Vnet to Azure Services: Create a Network appliance and redirect the traffic to the endpoint through that appliance
Securing Azure resources to services deployed directly into VNets.
Disk traffic from an Azure Virtual machine
Deploy Private Links
Private Link allows service providers to manage the private endpoint connection on their resources
-
Automatic: If they do have RBAC permissions, this connection becomes automatic.
-
Manual: If they don't have RBAC permissions, this connection needs to be manually configured.
Implementing an Azure Application Gateway
You can use an App gateway to route certain traffic to certain server pools or Azure resources.
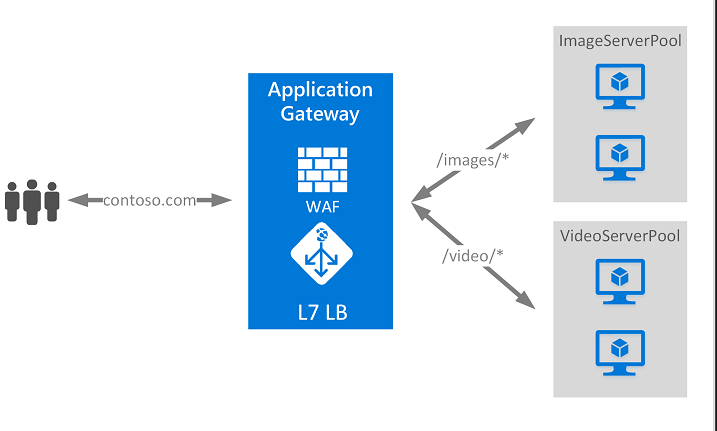
Application Gateway includes the following features:
- Secure Sockets Layer (SSL/TLS) termination - Application gateway supports SSL/TLS termination at the gateway, after which traffic typically flows unencrypted to the backend servers. This feature allows web servers to be unburdened from costly encryption and decryption overhead.
- Autoscaling - Application Gateway Standard_v2 supports autoscaling and can scale up or down based on changing traffic load patterns. Autoscaling also removes the requirement to choose a deployment size or instance count during provisioning.
- Zone redundancy - A Standard_v2 Application Gateway can span multiple Availability Zones, offering better fault resiliency and removing the need to provision separate Application Gateways in each zone.
- Static VIP - The application gateway Standard_v2 SKU supports static VIP type exclusively. This ensures that the VIP associated with application gateway doesn't change even over the lifetime of the Application Gateway.
- Web Application Firewall - Web Application Firewall (WAF) is a service that provides centralized protection of your web applications from common exploits and vulnerabilities. WAF is based on rules from the OWASP (Open Web Application Security Project) core rule sets 3.1 (WAF_v2 only), 3.0, and 2.2.9.
- Ingress Controller for AKS - Application Gateway Ingress Controller (AGIC) allows you to use Application Gateway as the ingress for an Azure Kubernetes Service (AKS) cluster.
- URL-based routing - URL Path Based Routing allows you to route traffic to back-end server pools based on URL Paths of the request. One of the scenarios is to route requests for different content types to different pool.
- Multiple-site hosting - Multiple-site hosting enables you to configure more than one web site on the same application gateway instance. This feature allows you to configure a more efficient topology for your deployments by adding up to 100 web sites to one Application Gateway (for optimal performance).
- Redirection - A common scenario for many web applications is to support automatic HTTP to HTTPS redirection to ensure all communication between an application and its users occurs over an encrypted path.
- Session affinity - The cookie-based session affinity feature is useful when you want to keep a user session on the same server.
- Websocket and HTTP/2 traffic - Application Gateway provides native support for the WebSocket and HTTP/2 protocols. There's no user-configurable setting to selectively enable or disable WebSocket support.
- Connection draining - Connection draining helps you achieve graceful removal of backend pool members during planned service updates.
- Custom error pages - Application Gateway allows you to create custom error pages instead of displaying default error pages. You can use your own branding and layout using a custom error page.
- Rewrite HTTP headers - HTTP headers allow the client and server to pass additional information with the request or the response.
- Sizing - Application Gateway Standard_v2 can be configured for autoscaling or fixed size deployments. This SKU doesn't offer different instance sizes.
Deploying a Web Application Firewall (WAF)
A simple to deploy firewall that protects your web applications from common exploits and vulnerabilities.
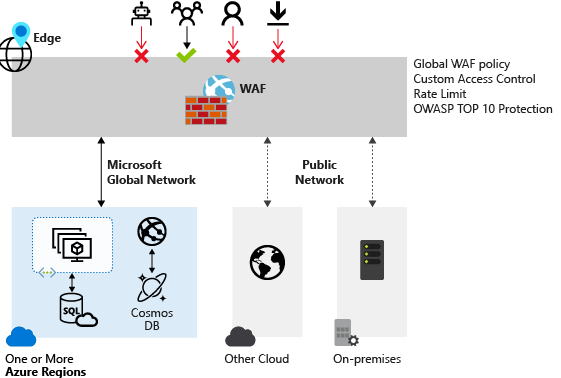
Can be deployed with App Gateway, Front Door, and CDN from Microsoft.
Configure Azure Front Door
Enables you to define, manage and monitor the global routing for your web traffic. Works at layer 7 Allows your users to connect to Front Door points of presence. Once on the backbone, it then redirects the traffic to the best region available to the user.
Resilient to failures of an entire region. The following features are included with Front Door:
- Accelerate application performance - Using split TCP-based anycast protocol, Front Door ensures that your end users promptly connect to the nearest Front Door POP (Point of Presence).
- Increase application availability with smart health probes - Front Door delivers high availability for your critical applications using its smart health probes, monitoring your backends for both latency and availability and providing instant automatic failover when a backend goes down.
- URL-based routing - URL Path Based Routing allows you to route traffic to backend pools based on URL paths of the request. One of the scenarios is to route requests for different content types to different backend pools.
- Multiple-site hosting - Multiple-site hosting enables you to configure more than one web site on the same Front Door configuration.
- Session affinity - The cookie-based session affinity feature is useful when you want to keep a user session on the same application backend.
- TLS termination - Front Door supports TLS termination at the edge that is, individual users can set up a TLS connection with Front Door environments instead of establishing it over long haul connections with the application backend.
- Custom domains and certificate management - When you use Front Door to deliver content, a custom domain is necessary if you would like your own domain name to be visible in your Front Door URL.
- Application layer security - Azure Front Door allows you to author custom Web Application Firewall (WAF) rules for access control to protect your HTTP/HTTPS workload from exploitation based on client IP addresses, country code, and http parameters.
- URL redirection - With the strong industry push on supporting only secure communication, web applications are expected to automatically redirect any HTTP traffic to HTTPS.
- URL rewrite - Front Door supports URL rewrite by allowing you to configure an optional Custom Forwarding Path to use when constructing the request to forward to the backend.
- Protocol support - IPv6 and HTTP/2 traffic - Azure Front Door natively supports end-to-end IPv6 connectivity and HTTP/2 protocol.
Organizes traffic based on rings. Primary and failover.
ExpressRoute
ExpressRoute is a private connection from your WAN directly to the Azure Backbone. It is compared to a physical VPN connection. You can configure Site-To-Site VPNs as a backup or failover for the ExpressRoute.
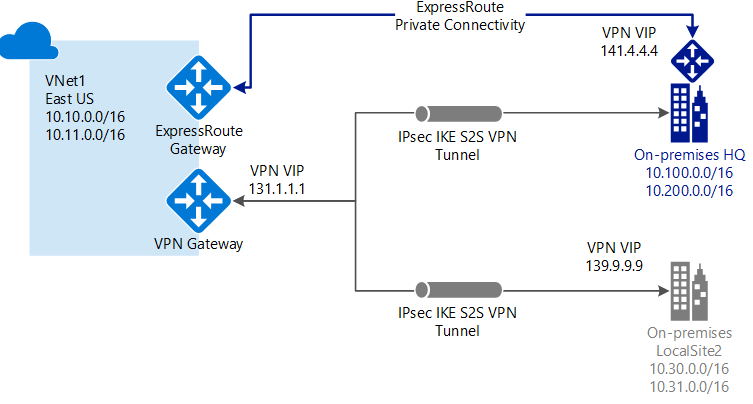
Encrypted traffic by IPSEC/IKE and MACsec
Exercises
https://learn.microsoft.com/en-us/training/modules/network-security/12-demonstration
Configure and manage host security
https://learn.microsoft.com/en-us/training/modules/host-security/ In this module, you will:
Configure and deploy Endpoint Protection Deploy a privileged access strategy for devices and privileged workstations Secure your virtual machines and access to them Deploy Windows Defender Practice layered security by reviewing and implementing Security Center and Security Benchmarks
Enable endpoint protection
Microsoft Defender for Endpoint is an enterprise endpoint security platform designed to help enterprise networks prevent detect, investigate and respond to advanced threats.
- Behavioral sensors embedded in windows 10 send data to your private isolated instance of Defender
- Cloud Security analytics take those signals and analyze them.
- Threat intelligence can then be used to identify attacks.
- Secure scores
- Threat experts with optional Threat Hunting service
- Attach surface reduction
Defender for Endpoint directly integrates with various Microsoft solutions, including:
- Microsoft Defender for Cloud
- Microsoft Sentinel
- Intune
- Microsoft Defender for Cloud Apps
- Microsoft Defender for Identity
- Microsoft Defender for Office
- Skype for Business
Define a privileged access device strategy
Devices must have hardware that supports MS Autopilot.
To have a secured workstation you need to make sure the following security technologies are included on the device:
- Trusted Platform Module (TPM) 2.0
- BitLocker Drive Encryption
- UEFI Secure Boot
- Drivers and Firmware Distributed through Windows Update
- Virtualization and HVCI Enabled
- Drivers and Apps HVCI-Ready
- Windows Hello
- DMA I/O Protection
- System Guard
- Modern Standby
Levels of security controls:
- Enterprise
- Specialized
- Privileged
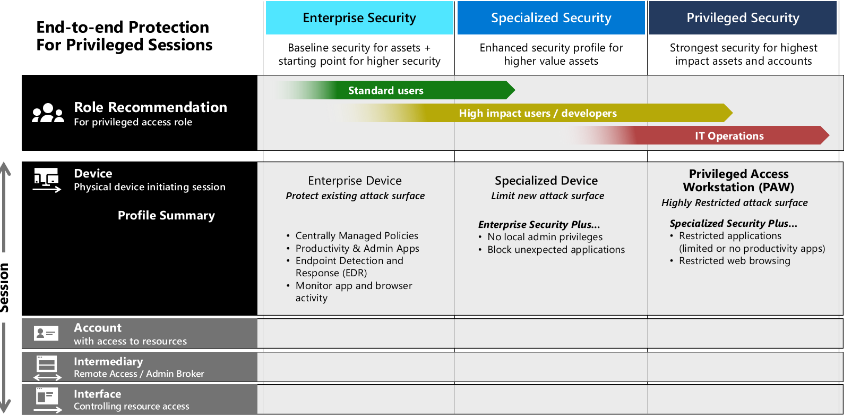
Deploy Privileged Access Workstations - PAWs
At the highest level of security, these workstations must be locked down and run the latest and most up to date operating systems. Administrative privilege
- High Sensitivity information
Jump box architecture - this PAW might not have any sensitive data on it, but it may be a workstation that can access infrastructure within the environment.
Create virtual machine templates
Need to understand Azure Resource Manager - it is an API that handles requests from the Azure Portal, CLI, Powershell, etc.
- Resource Provider- microsoft.storage
- resource manager template - JSON file that defines the resources
- Declarative syntax - I want a VM with 2cpu and 8gb rams
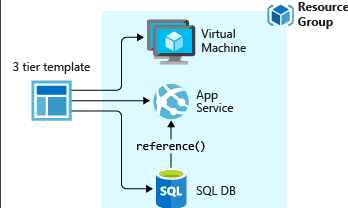 OR....
OR....
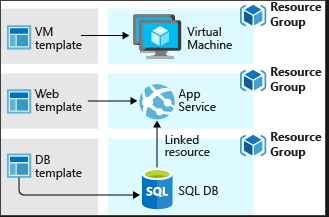
Resource Manager basically just converts JSON into API operations.
Enable and secure remote access management
Windows - RDP Linux - SSH usually with PuTTY client.
Azure Bastion is a secure alternative to opening up these ports to the public Internet
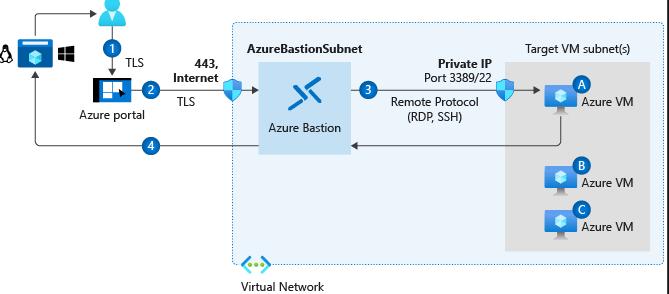
Key Features:
- RDP and SSH directly in Azure Portal
- Remote Session over TLS
- No public IPs needed on the VM
- No NSG hassle
- Protection against port scanning
- protection against zero-day exploits.
Configuration of update management
You can manage your windows and Linux updates from a single location in Azure for both your on prem and Azure environments.
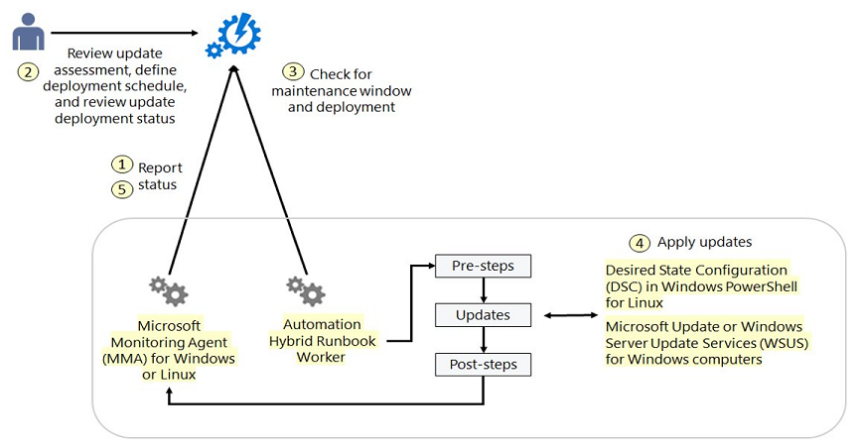
Deploy updates based on maintenance windows
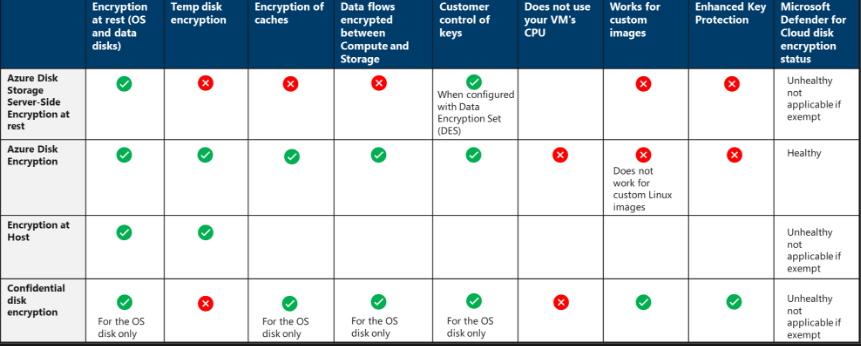
Disk encryption
Uses the BitLocker feature of windows and is integrated with Azure Key Vault.
MS Defender will flag and alert all VMs that aren't encrypted.
Supported VMs - Windows and Windows server.
Linux is also supported with ADE for Linux VMs
Server side encryption, encryption at the host and confidential disk encryption.
Deploy and configure Windows Defender
Windows Defender Credential Guard
- hardware security enhancement like Secure Boot and Virtualization
- NTLM and Kerberos derived credentials that are in a protected environment away from the operating system.
- better protection against persistent threats
Windows Defender Application Control - applications must gain trust to run.
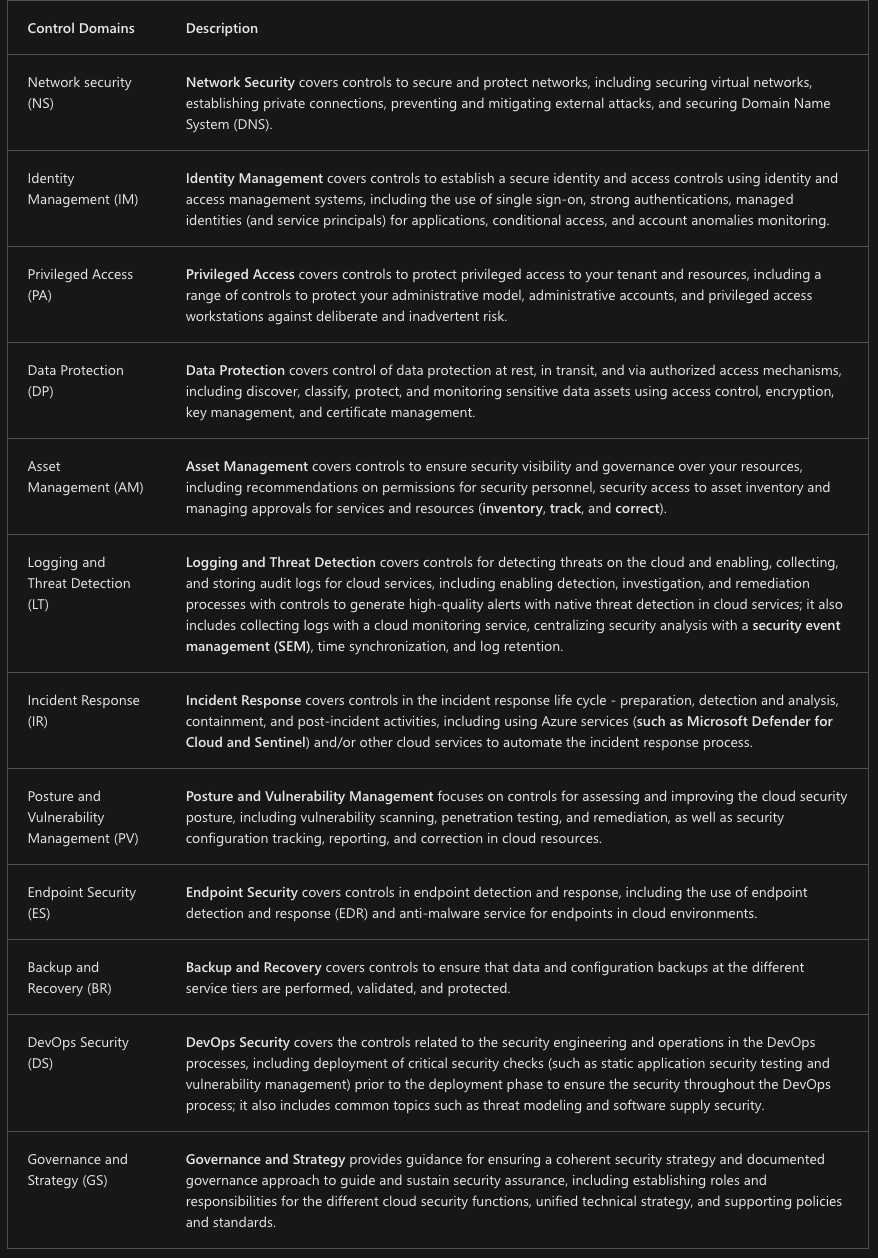
Microsoft Cloud Security Benchmark in Defender for Cloud.
- Cloud Adoption Framework - guadance on security, best practices and reference implementation
- Azure Well-Architected framework
- CISO workshop to accelerate modern security using Zero Trust principles
- other Cloud controls and standards, NIST, AWS, CIS, PCI-DSS
Works with a lot of control domains
- Network Security
- Identity management
- Privileged access, etc.
Security recommendations
based on the initiatives, it measures compliance of your resources to that policy and then recommendations are given by Defender.
- You have a policy for secured storage accounts
- The policy detects a storage account that is not secure.
- Defender analyzes the storage account and recommends a fix.
So, (1) an initiative includes (2) policies that generate (3) environment-specific recommendations.
Exercises
https://learn.microsoft.com/en-us/training/modules/host-security/13-demonstration
Enable Containers security
What is a container?
Azure Container Instance will need to pull an image from a container registry and then scan and monitor those images for vulnerabilities
Azure Container Registry is a preferred place to store Docker images. Protect your credentials Use vulnerability management Ensure only approved images are used in your environment
Log all container administrative user access for auditing Maintain an accurate audit trail of administrative access to your container ecosystem, including your Kubernetes cluster, container registry, and container images. These logs might be necessary for auditing purposes and will be useful as forensic evidence after any security incident. Azure solutions include:
- Integration of Azure Kubernetes Service with Microsoft Defender for Cloud to monitor the security configuration of the cluster environment and generate security recommendations
- Azure Container Monitoring solution
- Resource logs for Azure Container Instances and Azure Container Registry
Azure Container Instances
They are an alternative to VMs that can start up containers. This is not K8s where there is orchestration involved.
You can use Azure Log Analytics to:
- view detailed audit information
- troubleshoot container logs
- find noisy containers
- view performance information about the container
Container Registry authentication
- Entra ID identities
- Individual AD identity
- Admin user
- service principal
Kubernetes and AKS
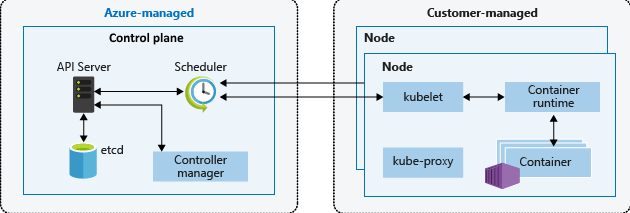
Features of Azure Kubernetes Service
- Fully managed
- Public IP and FQDN (Private IP option)
- Accessed with RBAC or Microsoft Entra ID
- Deployment of containers
- Dynamic scale containers
- Automation of rolling updates and rollbacks of containers
- Management of storage, network traffic, and sensitive information
Cluster Master
Node and Node Pools
Pods
Node Security
Networking Security
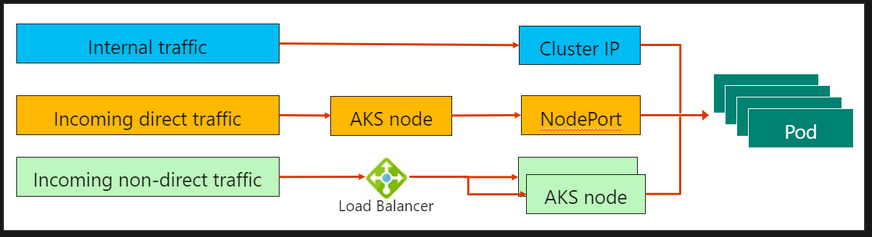
Services are logically grouped set of pods that share network connectivity.
- Cluster IP - internal IP address for use within the cluster
- NodePort - creates a port mapping for the node.
- Load balancer - allows the application to hit a single IP address and balances between pods
- ExternalName - Creates a specific DNS entry for easier application access
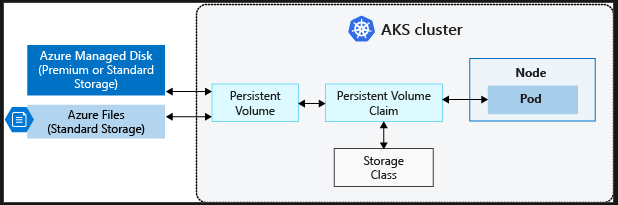
Deploy AKS Storage
Ephemeral temporary storage vs persistent storage Volumes are a way to store, retrieve and persist data across pods and through the application lifecycle These are backed by Azure Storage and these can use: Azure Disks - only available to one pod at a time Azure Files - can be used to mound an SMB 3.0 share backed by an Azure Storage account - use this if you need to mount storage to multiple pods.
Persistent volumes
A persistent volume is one that can exist beyond the lifetime of an individual pod. Can be used with Azure Disk or Azure Files Kubernetes then attaches pods to this volume using a StorageClass
Storage Classes
Used to define different tiers of storage such as premium and Standard. This also defines the reclaimPolicy - controls the Azure Storage resource when the pod is deleted
- default - uses standard storage to create a managed disk
- managed premium - uses premium storage to create a managed disk
Persistent Volume Claims
1:1 mapping of persistent volumes to claims
Secure authentication to AKS with Entra ID
Service account exists and is maintained by the kubernetes API OpenID and Oauth 2.0
AKS RBAC
Roles are for individual pods or namespaces or more granular permissions ClusterRoles are for the entire cluster
You assign these roles using RoleBindings. ClusterRoleBindings are for the entire clusterrole in the cluster.
Kubernetes Secrets are used for pod secrets They are held in the tmpfs and not on disk, and should never be commited to source control.
On Windows containers, the secrets are written to the volume which means they need to be protected by some form of encryption, like bitlocker.