Part 1: Manage Identity and Access
Entra ID and such
Secure Azure Solutions with Entra ID
Manage Users with Entra Groups
Two group types: Security and M365 Three types:
- Assigned - manually assigned users.
- Dynamic User - based on user rules - all users with Location Chicago.
- Dynamic Device - based on device rules - all Win 10 VMs for instance
Important: You can create a dynamic group for either devices or users but not for both. You can't create a device group based on the device owners' attributes. Device membership rules can only reference device attributions.
Configure Entra administrative units
Administrative unit is an Entra resource that is a container for other Entra resources. You can assign a role to the unit and then add groups to this unit.
Implement Passwordless Authentication
Replaces passwords with something you are or something you know.
- Authenticator
- Windows Hello
- FIDO2 Keys
Quick Demonstration
https://learn.microsoft.com/en-us/training/modules/azure-active-directory/13-demonstrations
Summary
Microsoft Entra ID helps you give access to your organization's resources by providing access rights to a single user, to an entire Microsoft Entra group, or to specific administrative units.
You should now be able to:
- Compare and contrast Microsoft Entra ID versus on-premises directory services with Microsoft Entra Domain Services.
- Configure and deploy users, groups, and administrative units to securely access resources in your tenant.
- Deploy a passwordless login solution for your Azure users and resources.
Implement Hybrid Identity
https://learn.microsoft.com/en-us/training/modules/hybrid-identity/
Objectives:
In this module, you will:
- Configure and deploy Microsoft Entra Connect.
- Configure password hash synchronization.
- Implement pass-through authentication.
- Select and configure the optimal authentication method based on your security posture.
- Deploy password writeback.
Deploy Entra Connect
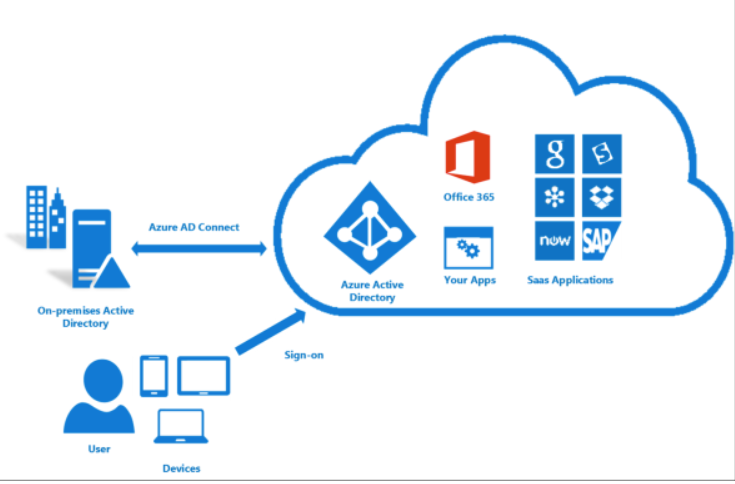 Microsoft Entra Connect provides the following features:
Microsoft Entra Connect provides the following features:
- Password hash synchronization. A sign-in method that synchronizes a hash of a users on-premises AD password with Microsoft Entra ID.
- Pass-through authentication. A sign-in method that allows users to use the same password on-premises and in the cloud, but doesn't require the additional infrastructure of a federated environment.
- Federation integration. Federation is an optional part of Microsoft Entra Connect and can be used to configure a hybrid environment using an on-premises AD FS infrastructure. It also provides AD FS management capabilities such as certificate renewal and additional AD FS server deployments.
- Synchronization. Responsible for creating users, groups, and other objects. As well as, making sure identity information for your on-premises users and groups is matching the cloud. This synchronization also includes password hashes.
- Health Monitoring. Microsoft Entra Connect Health can provide robust monitoring and provide a central location in the Azure portal to view this activity.
You install an agent on a couple sync servers in your on prem environment and have to maintain the connection.
Explore authentication options
Methods:
- password hash synchronization - uses same ID and password in the cloud as on prem.
- pass through authentication - provides a simple password validation by using a software agent that runs on one or more on-premises servers. The servers validate users directly with on prem AD, so the validation doesn't happen inside of the cloud. Companies with security standards that require on prem password policies might choose this.
Federated authentication - Hands off authentication to a third party such as ADFS.
Configure Password Hash Synchronization (PHS)
PHS syncs the same password for your on prem AD to Azure AD services in a secure, encrypted manner. This is SAME- Sign in, not single sign in.
Implement Pass Through Authentication
This is a hybrid approach that validates Entra ID by using the passwords directly against the on prem AD.
Federation with Entra ID
This uses a third party organization that is trusted by your organization. Set up password hash synchronization as a backup.
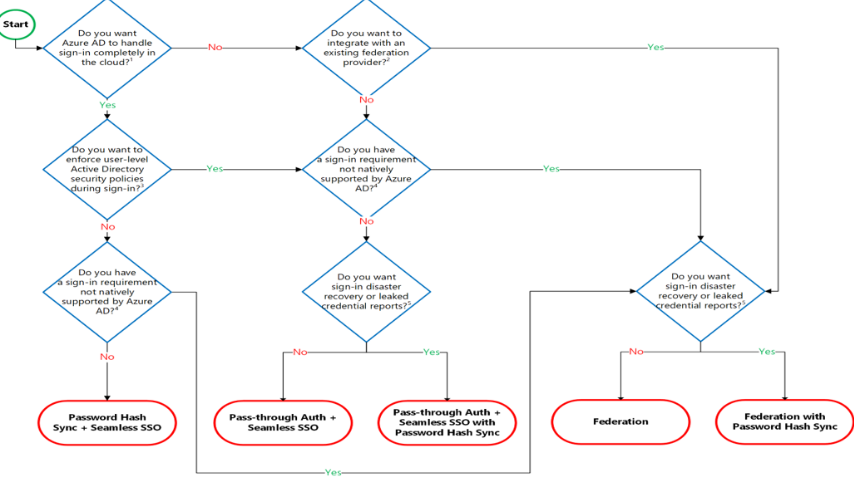
Authentication decision tree
- Cloud Authentication
- Federated Authentication
Configure Password Writelock
Allows Entra ID to write passwords back to AD
Deploy Microsoft Entra ID Protection
In this module, you will:
- Deploy and configure Identity Protection
- Configure multi-factor authentication for users, groups, and applications
- Create Conditional Access policies to ensure your security
- Create and follow an access review process
Explore Microsoft Entra ID Protection
Allows for 3 key tasks
- Automate the detection and remediation of identity based risks
- investigate risks
- export risk detection data to third party utilities.
Three default policies
- MFA registration - requires all users to enroll in MFA in order to access any resources
- User Risk remediation policy - forces password changes if the risky users is triggered.
- sign in risk remediation policy - calculates a risk score based on the probability that the sign in wasn't the user. If a user signs in with one IP for a long time and then some random IP from another location pops up, this will flag that.
From MS documentation:
- User risk policy - Identifies and responds to user accounts that may have compromised credentials. Can prompt the user to create a new password.
- Sign-in risk policy - Identifies and responds to suspicious sign-in attempts. Can prompt the user to provide additional forms of verification using Microsoft Entra multifactor authentication.
- MFA registration policy - Makes sure users are registered for Microsoft Entra multifactor authentication. If a sign-in risk policy prompts for MFA, the user must already be registered for Microsoft Entra multifactor authentication.
Configure Risk Event detections
Triggered by:
- users with leaked creds
- impossible travel to locations - Washington DC at 8 am, London at 8:15 AM
- infected devices
- known malicious IP ranges
- anonymous IP addresses
Implement User Risk Policy
This allows Microsoft to assess and assign a risk score based on known sign in trends across all of Azure. This allows your security team to view these trends and to automate the actions for the end user, such as resetting the password, confirm that it was a valid attempt, block the user.
Implement Sign In Risk Policy
Sign in risk is the probability that the authentication request is not authorized by the person. Sign in risk can be evaluated as part of a conditional access policy.
Location: you can include or exclude certain locations
Client apps: You can include or exclude certain apps. If you want everyone to be able to access Exchange, but not Teams, you can write conditional access policies that apply to one app vs another.
Risky sign ins - up to 30 days
Able to find:
- Which sign-ins are classified as at risk, confirmed compromised, confirmed safe, dismissed, or remediated.
- Real-time and aggregate risk levels associated with sign-in attempts.
- Detection types triggered
- Conditional Access policies applied
- MFA details
- Device information
- Application information
- Location information
Administrators can then choose to take action on these events. Administrators can choose to:
- Confirm sign-in compromise
- Confirm sign-in safe
Deploy MFA in Azure
MFA makes it challenging to authenticate by splitting up the methods. If a hacker gets your username and password, it is useless unless they also get the MFA device
- Something you know - a password
- something you have - a device
- something you are - biometrics
MFA has the ability for monitoring, real time threat mitigation,, use with Microsoft 365 (teams, exchange, etc), additional protection for admin accounts
Methods:
- Call to phone
- text message to phone
- notification to mobile app
- verification code from mobile app
Features:
- account lockout
- auto block users when devices are stolen or lost
- fraud alerts - block user when they report the fraud attempts
- code they can enter to report fraud
Notifications - emails admins when fraud reports are generated.
Trusted IPs - only works from within the company's intranet.
Enable MFA
To enable MFA, go to user properties in Entra ID and set for users. Options can be disabled, enforced or enabled. Disabled - No MFA Enabled - the users are able to add MFA Enforced - the users have turned on MFA
Enable Entra Conditional Access
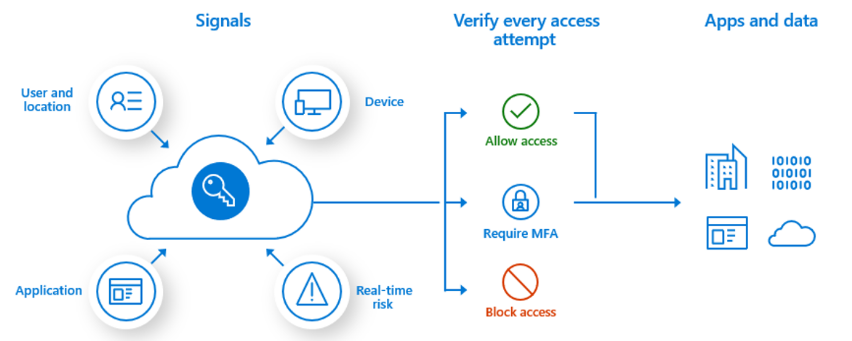 Conditional access is the heart of the identity driven control plane. It is the next gen technology policy built for the cloud.
Conditional access is the heart of the identity driven control plane. It is the next gen technology policy built for the cloud.
Identity as a service. Protects the organizations assets while empowering the user's do be productive.
Configure Conditional Access conditions
Users and groups are mandatory - you can include them all and exclude or exclude them all except for a couple or mix and match.
Block or Grant access after the conditional access policies are triggered.
Access Reviews
You can use these to review whether or not a user needs the roles they have. Group owners to verify membership, set up recurring reviews based on stats such as last sign in
Try these examples:
https://learn.microsoft.com/en-us/training/modules/azure-ad-identity-protection/12-demonstrations
Configure Microsoft Entra Privileged Identity Management
By the end of this module, you'll be able to:
- Describe Zero Trust and how it impacts security
- Configure and deploy roles using Privileged Identity Management (PIM)
- Evaluate the usefulness of each PIM setting as it relates to your security goals
Explore the zero trust model
Never Trust, Always Verify
Ideal utopia:
- Strong identity authentication everywhere (user verification via authentication)
- Devices are enrolled in device management, and their health is validated
- Least-privilege user rights (access is limited to only what is needed)
- The health of services is verified (future goal)
Guiding principles:
Verify explicitly - always authenticate based on all available data points
Use Least Privilege access - limit user access with just in time and just enough access and data protection.
Assume a breach - minimize blast radius and segment access - verify encryption and use analytics to improve the defense.
NIST 800-207 is a reference to zero trust architecture.
Review the evolution of identity management
Microsoft identity Manager - MIM helps organizations manage users, creds and access within their organizations on prem AD. Entra Connect can then make the AD users and groups sync with Azure. Today, your digital identity is the security boundary and your access is limitless to what your identity is allowed to do with it. Credentials + privileges = digital identity.
Traditional - on prem, no single sign on Advanced - conditional access Optimal - passwordless, behavior analyzed in real time - continuous protection
Steps for a passwordless world:
- enforce MFA
- reduce legacy authentication workflows
- remove passwords
Deploy Entra Privileged Identity Management
PIM is used to enable and manage access to important resources in your organization Requires a P2 license
Key Features:
- Provide just-in-time privileged access to Microsoft Entra ID and Azure resources
- Assign time-bound access to resources using start and end dates
- Require approval to activate privileged roles
- Enforce multi-factor authentication to activate any role
- Use justification to understand why users activate
- Get notifications when privileged roles are activated
- Conduct access reviews to ensure users still need roles
- Download audit history for internal or external audit
- Prevents removal of the last active Global Administrator and Privileged Role Administrator role assignments
Configure privileged identity management scope
You assign roles to users based on necessity and then those users are able to then elevate their permissions within the PIM interface. If an approver is needed, they can then approve or deny the request if they are unsure of the reasons why. These accesses are logged and audited.
Extend or Renew access assignments when they expire
- Privileged Role Administrator permissions
- Approver Permissions
- Eligible role user permissions
Implement privileged identity management onboarding
P2 License required
First GA to use PIM is automatically assigned the Security Admin and Privileged Role Administrator role in Azure No other users get access by default past the first Global Admin - the Global Admin can then assign other users in PIM.
Important: Set up redundancy with your Privileged Role Administrators
- Activation settings: duration, MFA, justification, approval
- allow permanent assignment either active or eligible
Implement a privileged identity workflow
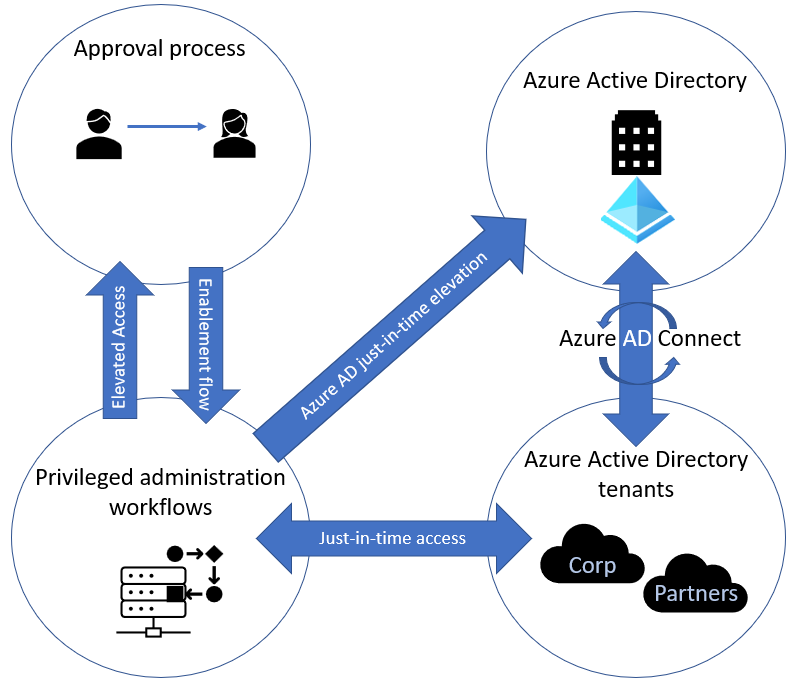
Implement JIT access and elevated access. We can audit new requests to elevate permissions within Azure.
Set up a dashboard to monitor alerts, users assigned to each role, access reviews and the number of eligible and permanent admins.
Exercises
Design an enterprise Governance Strategy
- Explain the shared responsibility model and how it impacts your security configuration
- Create Azure policies to protect your solutions
- Configure and deploy access to services using RBAC
Shared Responsibility model
Microsoft is responsible for the security of the cloud, you are responsible for what is IN the cloud. You always retain responsibility for:
- Data
- Endpoints
- Accounts
- Access Management
Azure Cloud Security Advantages
Basically taking some of those things that you are responsible for on prem and moving them to the cloud provider's responsibility.
Review Hierarchy of systems
Azure Resource Manager is the deployment and management service for Azure. It has a CRUD API that you can use to deploy everything.
Scope:
- Management group
- Subscription
- Resource Group
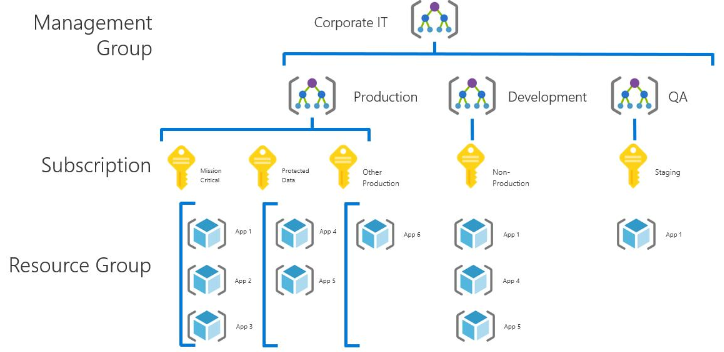
Resource Groups:
- All the resources in your group should share the same lifecycle. You deploy, update, and delete them together. If one resource, such as a database server, needs to exist on a different deployment cycle it should be in another resource group.
- Each resource can only exist in one resource group.
- You can add or remove a resource to a resource group at any time.
- You can move a resource from one resource group to another group.
- A resource group can contain resources that are located in different regions.
- A resource group can be used to scope access control for administrative actions.
- A resource can interact with resources in other resource groups. This interaction is common when the two resources are related but don't share the same lifecycle (for example, web apps connecting to a database).
Management Groups: Allow subscriptions to be grouped together. RBAC permissions can then be assigned to the Management Group that will affect all of the subscriptions in that group.
- Group your subscriptions
- mirror your organizations structure
- apply policies to the management group and will affect all subscriptions inherently.
Configure Azure Policies
3 Pillars of Azure Policy:
- Enforcement and compliance - blocks creation of resources, reports on the existing compliance of the resources
- Apply policies at scale - you can apply one policy to the management group that trickles down to all of the re
- Remediation - flagged resources won't be automatically changed because they could impact the environment. You create a remediation task to bring resources into compliance.
Custom policies vs built in policies - you can customize policies to your own liking
Initiatives are grouped policies that share common goals.
Enable Azure RBAC
- Ensures that when people leave the organization, they lose access to resources in the cloud
- Balances autonomy and central governance.
When you disable an AD account (from on prem even) the access to Azure is disabled as well. Synched passwords offered some resiliency - one environment was hacked, but the other was able to be logged into.
Each subscription is associated with one Entra directory. A resource can only be in one resource group. One resource group is associated with one subscription.
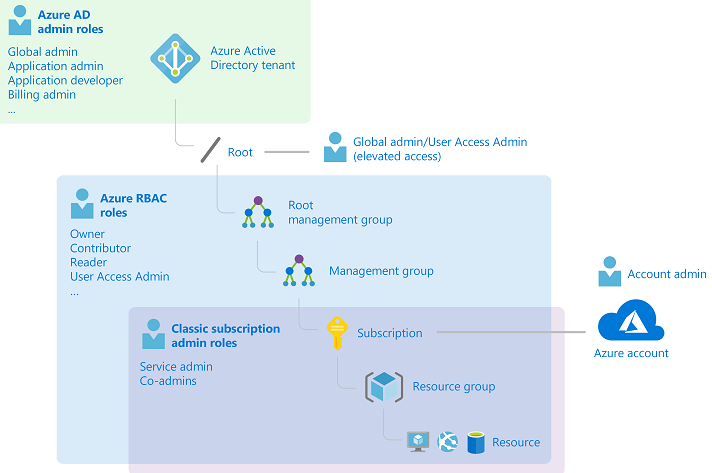
Compare and contrast Azure RBAC vs Azure Policies
Policy = resource actions RBAC = user actions
a deployIfNotExists or modify policy assignment needs permissions to create or update targeted resources
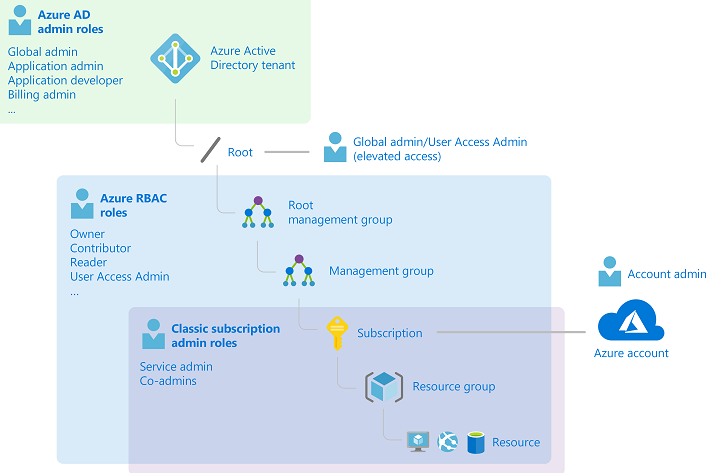
Configure built in roles
- Contributor
- Owner
- Reader
- User Access Administrator
Limit of 5000 custom roles per directory. Germany and China can have up to 2000 roles You cannot set AssignableScopes to the root scope You can only define one manaagement group in AssignableScopes
Resource Locks
CanNotDelete means users can still read and modify the resource but not delete ReadOnly means that you cannot delete the resource - remove the lock and then delete.
Azure Blueprints
Orchestrates deployment of various resource templates such as
- Role Assignments
- Policy Assignments
- ARM templates
- RGs
Blueprints are backended by the Cosmos DB service
how is it different than ARM templates?
ARM templates might not bring together an entire environment - role assignments, policy, etc.
How is it different from Azure Policy?
Azure Policy is an explicit allow and deny system. Blueprints deploy policies and then build resources that conform to those policies.
Blueprint definition
Blueprints are composed of the artifacts listed above.
- Role Assignments
- Policy Assignments
- ARM templates
- RGs
You define where the blueprint is saved - management group or subscription You can also pass in parameters to the blueprint - or use predefined values.
Design a subscription management plan
- environment type
- ownership and governance model
- organizational structure
- application portfolios
NOTE: Subscriptions contain limits and you want to plan around these limits.
Subscriptions:
- serve as boundaries for Azure Policy Assignments.
- secure and separate workloads
- management labs
- separate out platform subscriptions for billing/monitoring/identity/DNS where required.
Quotas and subscription limits
Consider limits Consider availability of SKUs in certain regions Quotas aren't capacity guarantees Reuse decommed subscriptions.
Cost management
Chargeback models
- shutdown schedules
- Azure Advisor
- policy to prevent deployments
- regular schedule and cadenced review of costs
Organization and governance recommendations
Treat subscriptions as a unit of management aligned with your business needs
- Make subscription owners aware of their roles and responsibilities.
- Quarterly review of PIM
- target network topology
- group subscriptions under management groups
- dedicated subscripts for billing/monitoring/identity/DNS
- Connect the subscriptions by ExpressRoute
- Dashboards and alerting on quota limits
Automate subscription creation via a request flow.
Configure the following settings to prevent users from transferring Azure subscriptions to or from your Microsoft Entra tenant:
- Set Subscription leaving Microsoft Entra directory to Permit no one.
- Set Subscription entering Microsoft Entra directory to Permit no one.
Configure a limited list of exempted users.
- Include members from an Azure PlatformOps (platform operations) team.
- Include break-glass accounts in the list of exempted users.