2. Using Service Control Policies
Service Control Policies are JSON documents that can be attached to an organization, to individual OUs or to individual accounts. Where the SCP is attached affects all of the accounts below.
You cannot restrict the management account with a SCP.
SCPs are:
- Account Permissions Boundaries
- They limit what the account AND the root user can do.
- not granting any permissions.
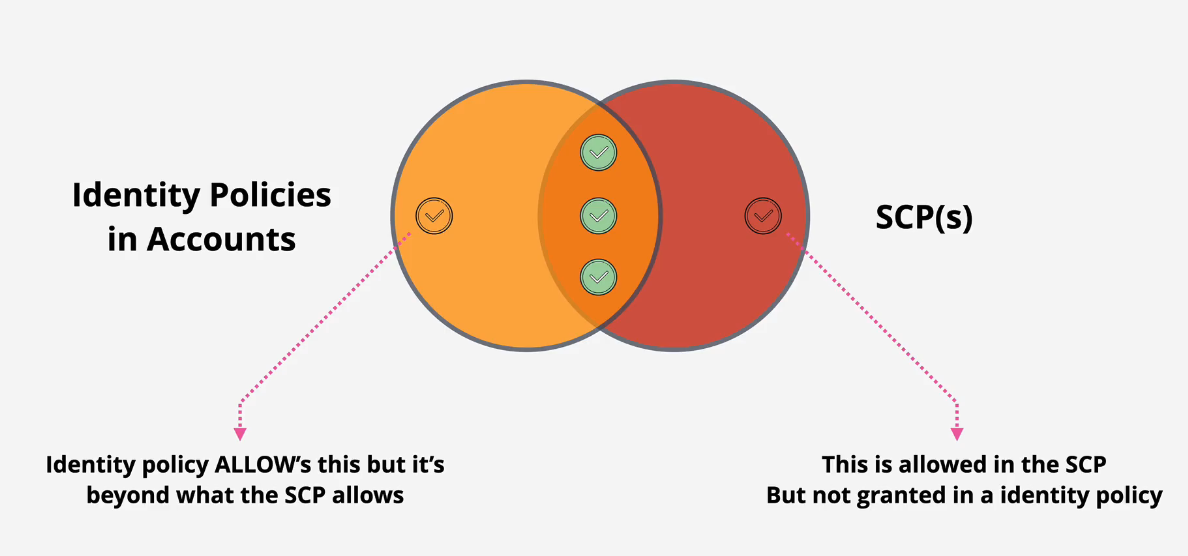
Allow vs Deny list - to use FullAWSAccess or not...
- You can deny certain permissions, so full access but deny S3 or EC2.
Allow list: Remove the FullAWSAccess and then only allow those services you want to allow, like S3, EC2.
Demo: Create AWS Organizations Organizational Units
Setup Account
- Log into your AWS Management account as the IAMAdmin user
- Navigate to the AWS Organization console
- Check the box next to the root container, then click on Actions -> Create New
- Create a Development and a Production OU
- Click on the development account and then click Actions -> Move and then click on the development OU.
- Click on the production account and then click Actions -> Move and then click on the Production OU.
Note: I also created other accounts, but this is unnecessary.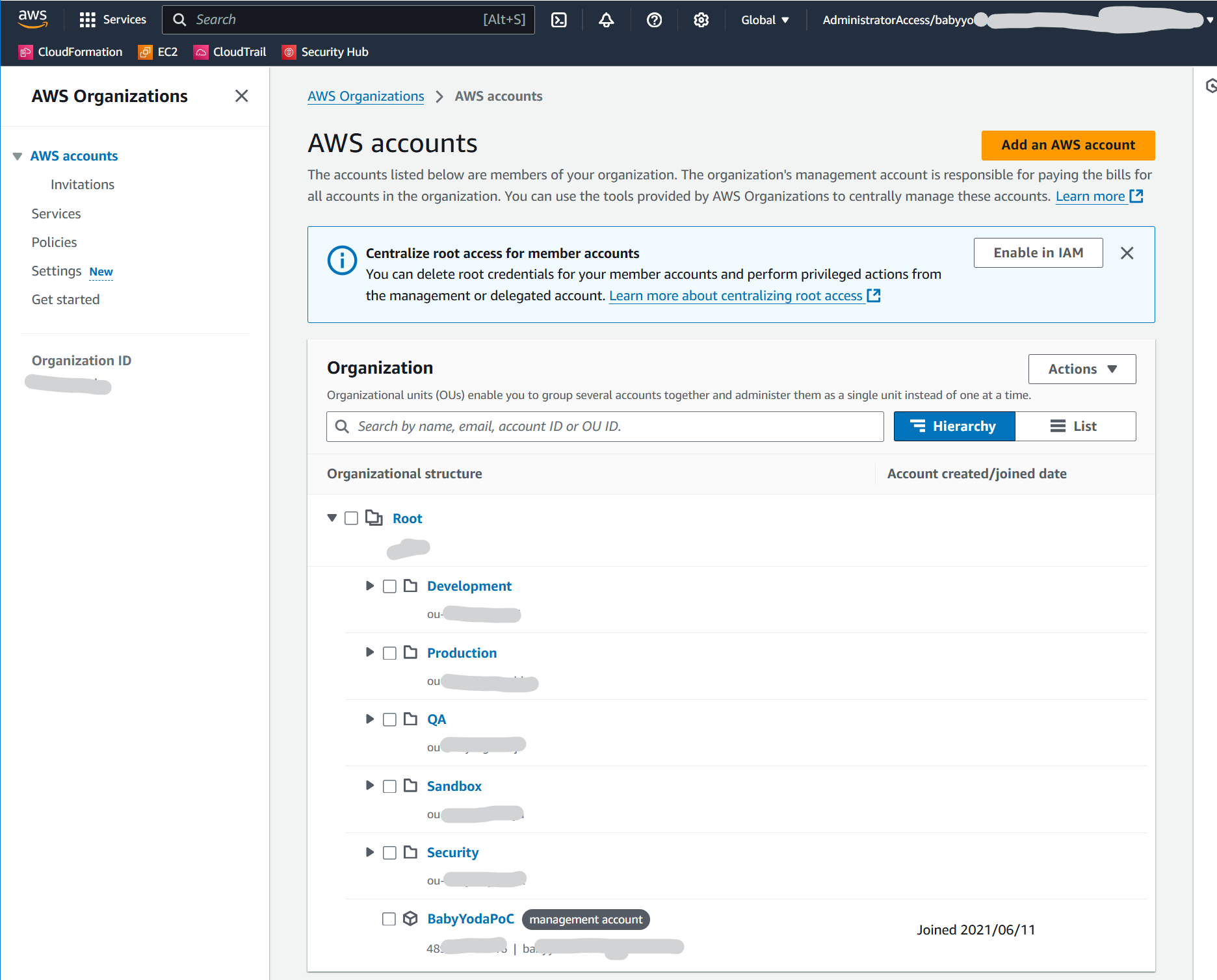
Create S3 Bucket in Production Account
- Switch over to the production role (remember to click the dropdown and select production)
- Navigate to the S3 console and create a bucket
- Name the bucket scptest1234567, select US-East-1 and scroll all the way to the bottom and click Create.
- Upload a picture of your choice to the bucket.
- You should be able to open this picture after it has been uploaded to the S3 bucket
Enable Service Control Policy
- Switch back to the management account by clicking on the dropdown and selecting Back to IAMAdmin.
- Navigate to AWS Organizations and select Policies from the left.
- Click on Service Control Policies and then click Enable Service Control Policies.
- What this did was create a FullAWSAccess policy across the entire organization.
- View the policy and it should have this JSON:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "*",
"Resource": "*"
}
]
}
- This enables a global policy with global allow across the entire company.
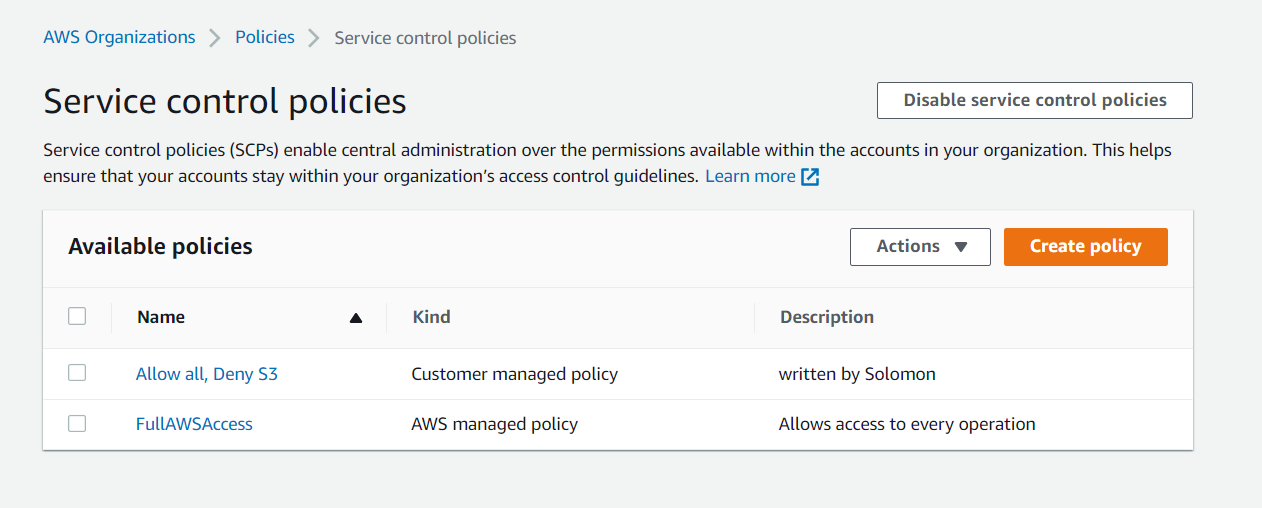
Create Allow all, Deny S3 Service Control Policy
- Navigate back to service Control Policies and select Create Policy.
- Name the policy "Allow all except S3"
- Copy this JSON in, noting that we're adding an explicit deny on all of the S3 for the entire organization.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "*",
"Resource": "*"
},
{
"Effect": "Deny",
"Action": "s3:*",
"Resource": "*"
}
]
}
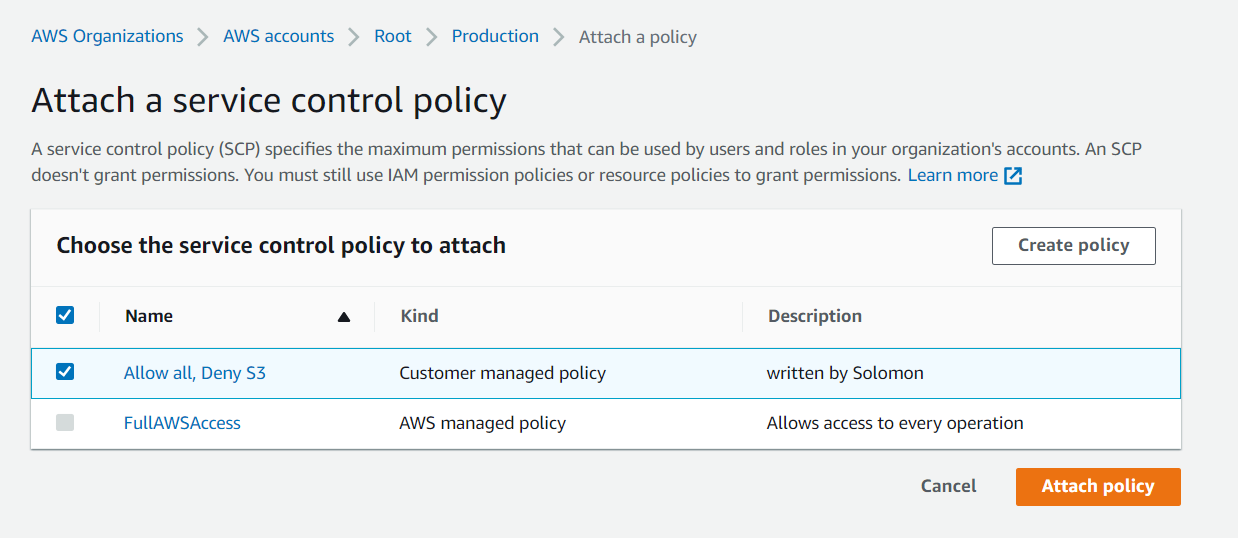
Apply Service Control Policy
- Navigate back to the AWS Organizations console in the management account.
- Click on the Production OU and then click the Policies tab.
- Click attach and then select the Allow all, Deny S3 policy
- Detach the FullAWSAccess policy that is attached directly to the Production OU.
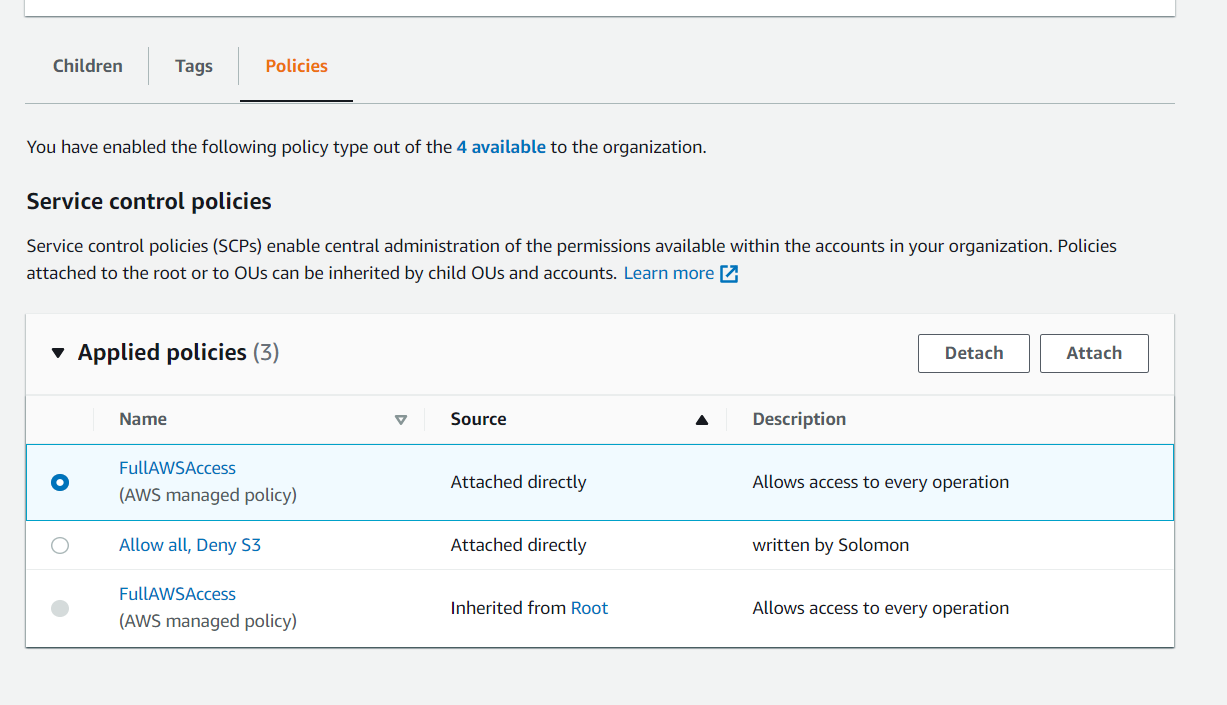
- Navigate back into the production account and go to the S3 console
- Notice you now don't have the permissions to interact with S3
- Click on EC2 and notice you can go to EC2 and do whatever you need to do.
Detach the Service Control policy
- Go back into the management console, detach the custom service control policy
- Navigate back to the Production account and verify that you can access S3.
- Notice that you didn't attach the FullAWSAccess policy and the permissions are handled inherited by the OU and the root.
Clean up
- Empty the S3 bucket
- Delete the S3 bucket
- Delete the Policy you created in AWS Organizations
Demo: Creating an Organizational Trail
- Log into the management account
- Navigate to the CloudTrail Console
- Click on Trails
- Click on Create Trail
- Check the box that says Enable for all accounts in my organization
- Create a new S3 bucket and name it cloudtrail-organizationname-random number if needed because it needs to be unique
- Enable Log file encryption
- Check the Enable CloudWatch Logs box
- Leave the default name or name it what you'd like, you will use this when viewing the logs via Cloudwatch. I named mine
aws-cloudtrail-logs-489725180016-ceacfd18or left the default, I can't remember. - Create a new IAM role
- Name this role. I named mine
CloudTrailRoleForCloudWatchLogs_BabyYodaPoC-Organization - View the policy document
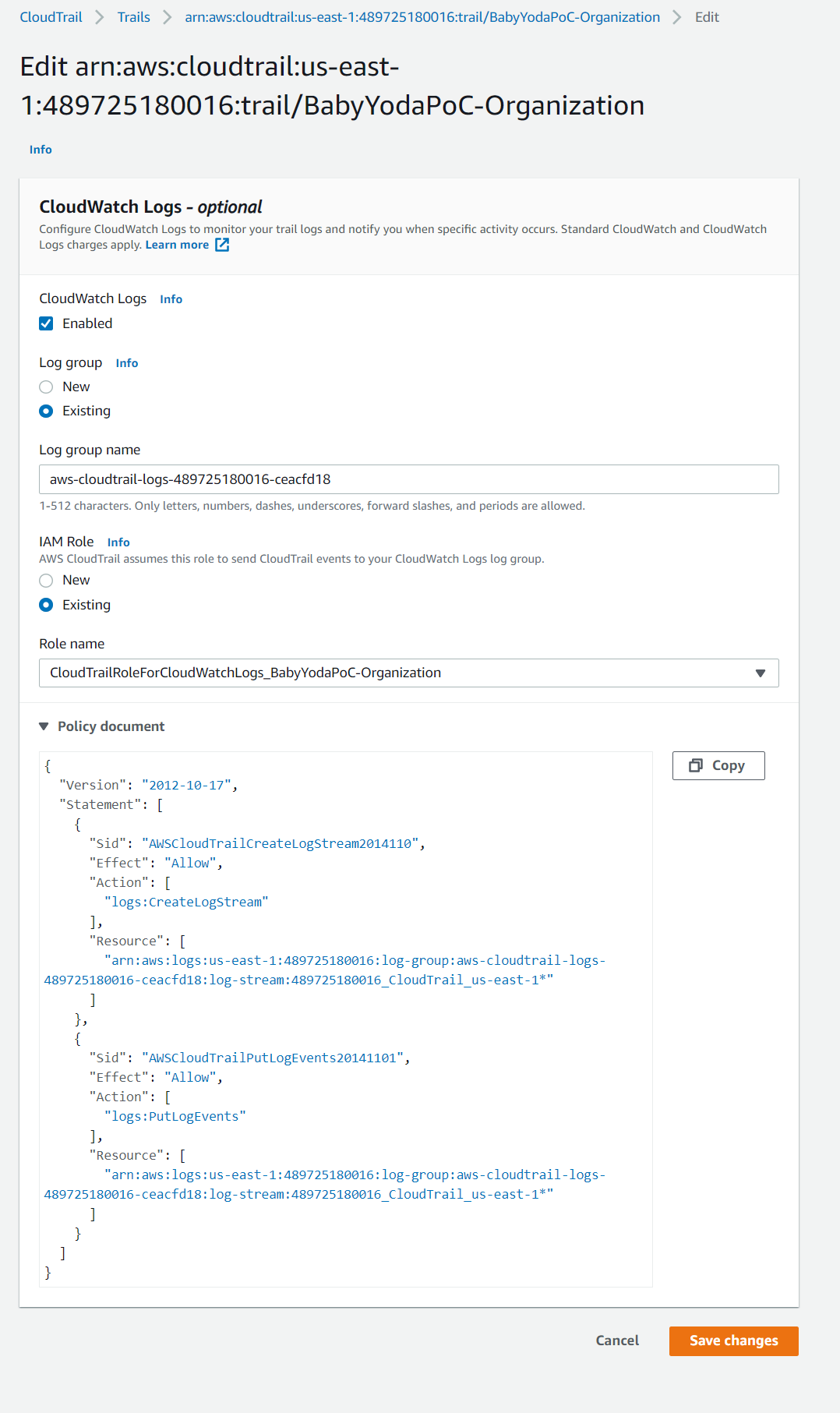
- Click next
- Select the type of events that the Trail logs. Management is default, Data costs extra.
- Make sure Read and Write are checked under Management events and click Next.
Viewing the Logs in S3
- Click on the S3 bucket
- Navigate through the folder structure. Notice that there are more regions than you have resources in.
- Click through to one of the JSON files.
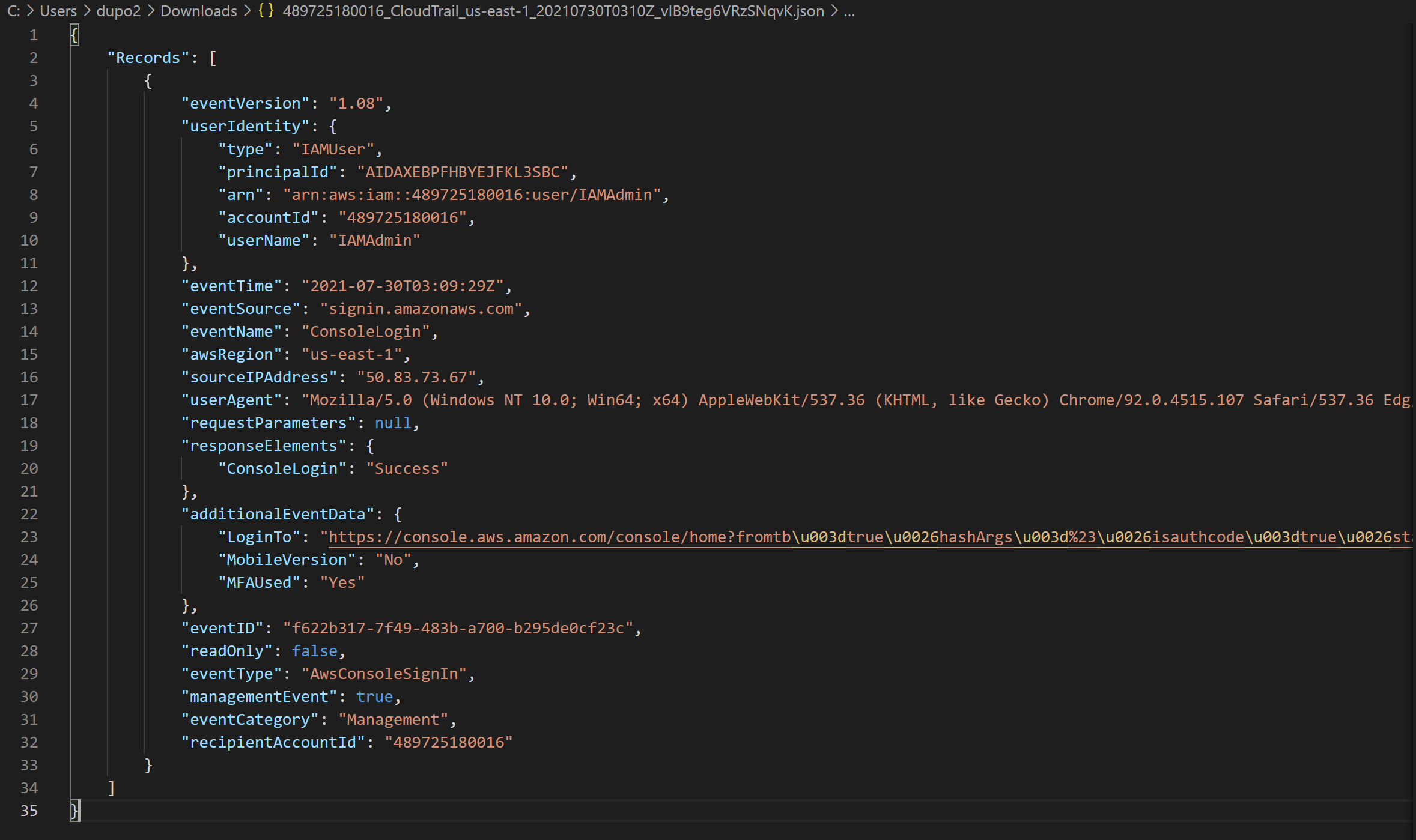
Viewing the Logs in CloudWatch.
- Navigate to the CloudWatch console.
- Click on Logs to expand and then click on Log Groups.
- Click on the log group that you named above.
- Click on the log stream that corresponds to the data you are gathering.
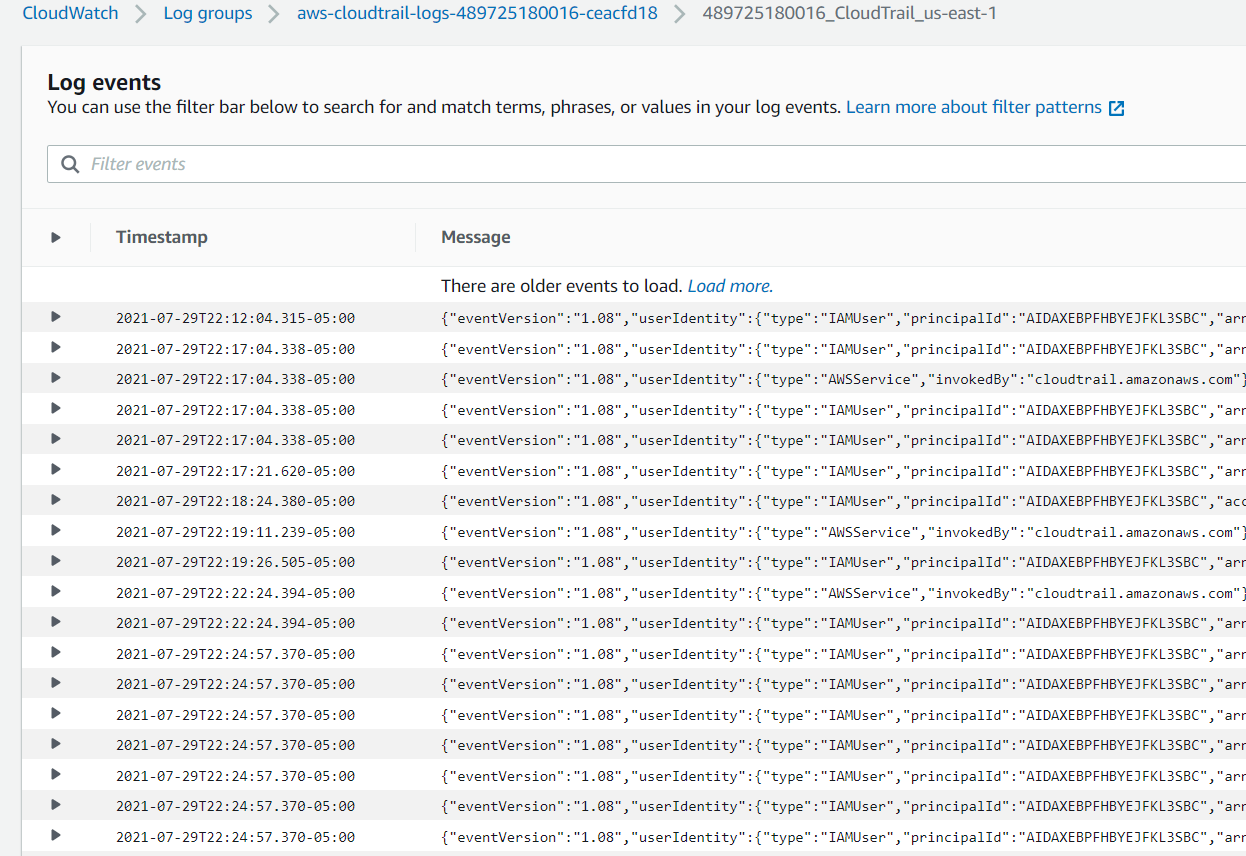
- Expand an entry to view the log.
- While you're in this console, click on event history to view the last 90 days of logs.
Finished Trail:
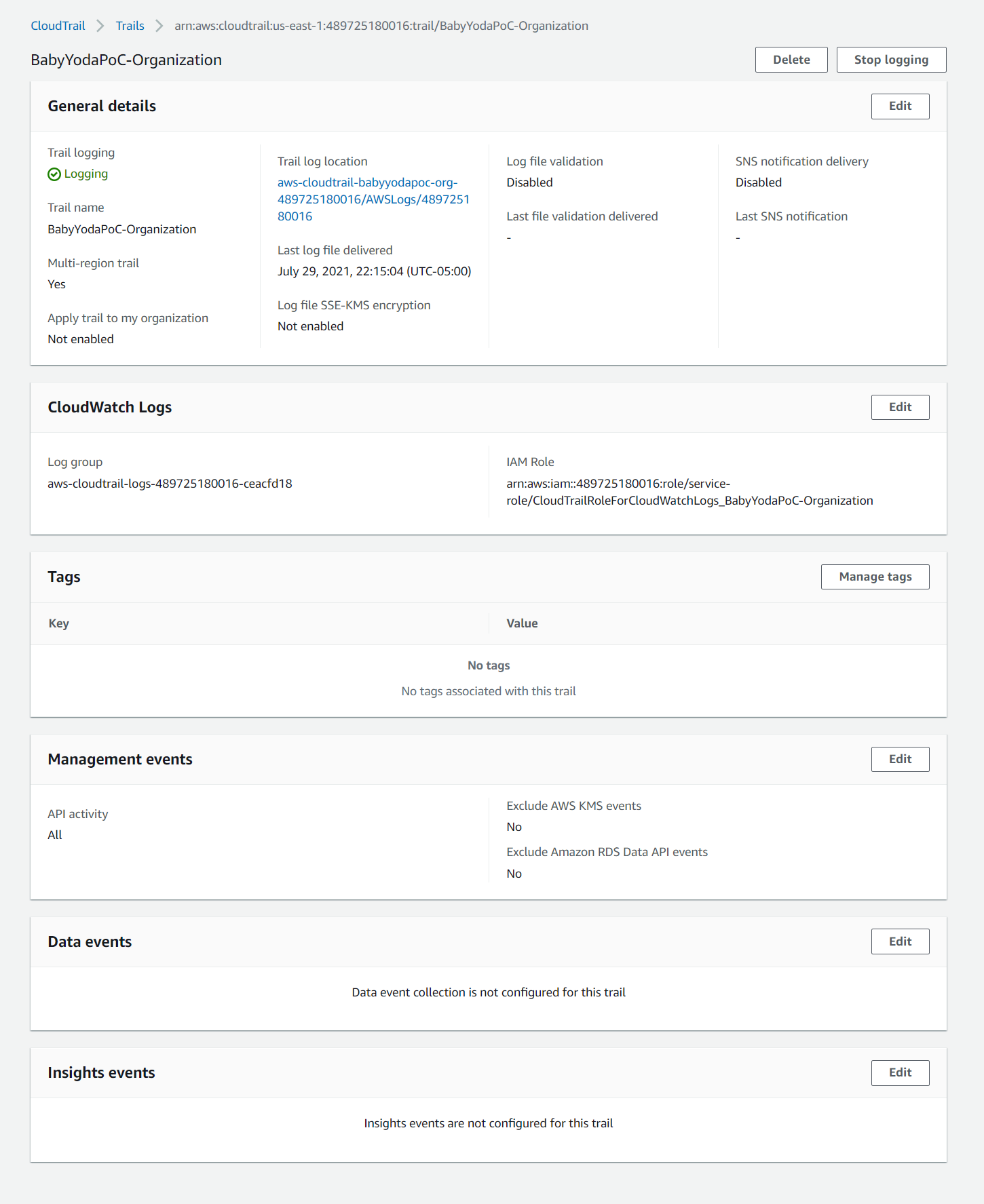
Clean Up
- Delete the trail or click the stop logging button. This doesn't cost too terribly much, maybe a few cents here and there per month if you're not actively using the account.