3. Security Token Service - STS
sts:AssumeRole
- Similar to access keys - they expire and don't belong to the identity
- Limited Access
- Used to access AWS resource
- Requested by an identity (AWS or External)
Trust Policy
Wall around the role
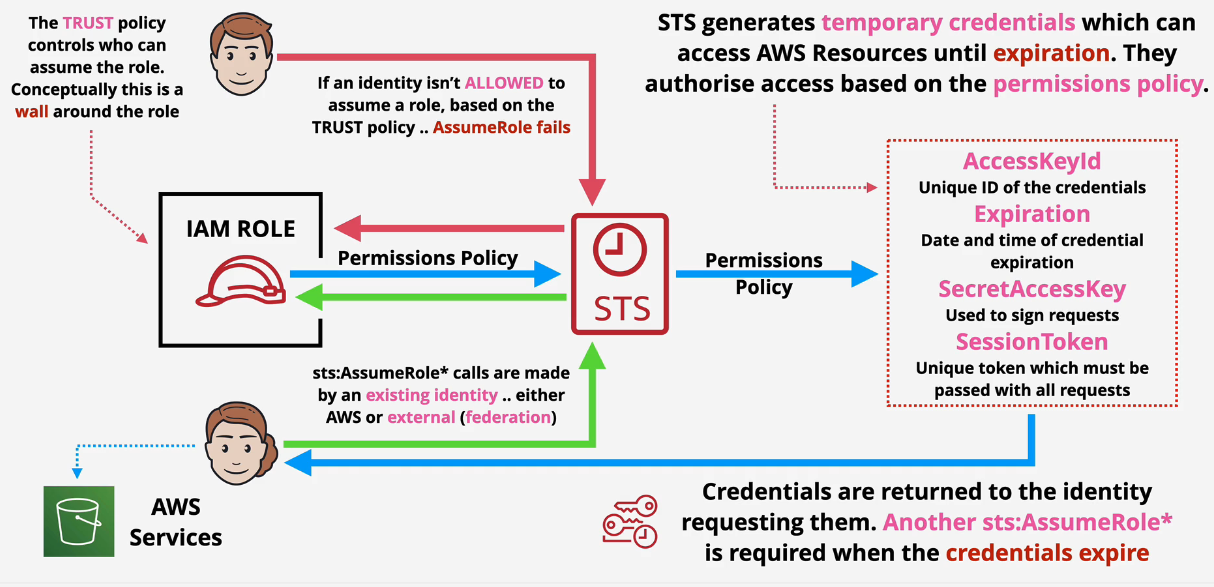
Roles pretty much uses STS :)
Revoking IAM Role Temporary Credentials
Roles can be assumed by many identities NOTE: Temporary credentials cannot be cancelled. What happens if these credentials are leaked?
- Changing the trust policy has no impact on existing credentials.
- Changing the permissions policy impacts ALL credentials
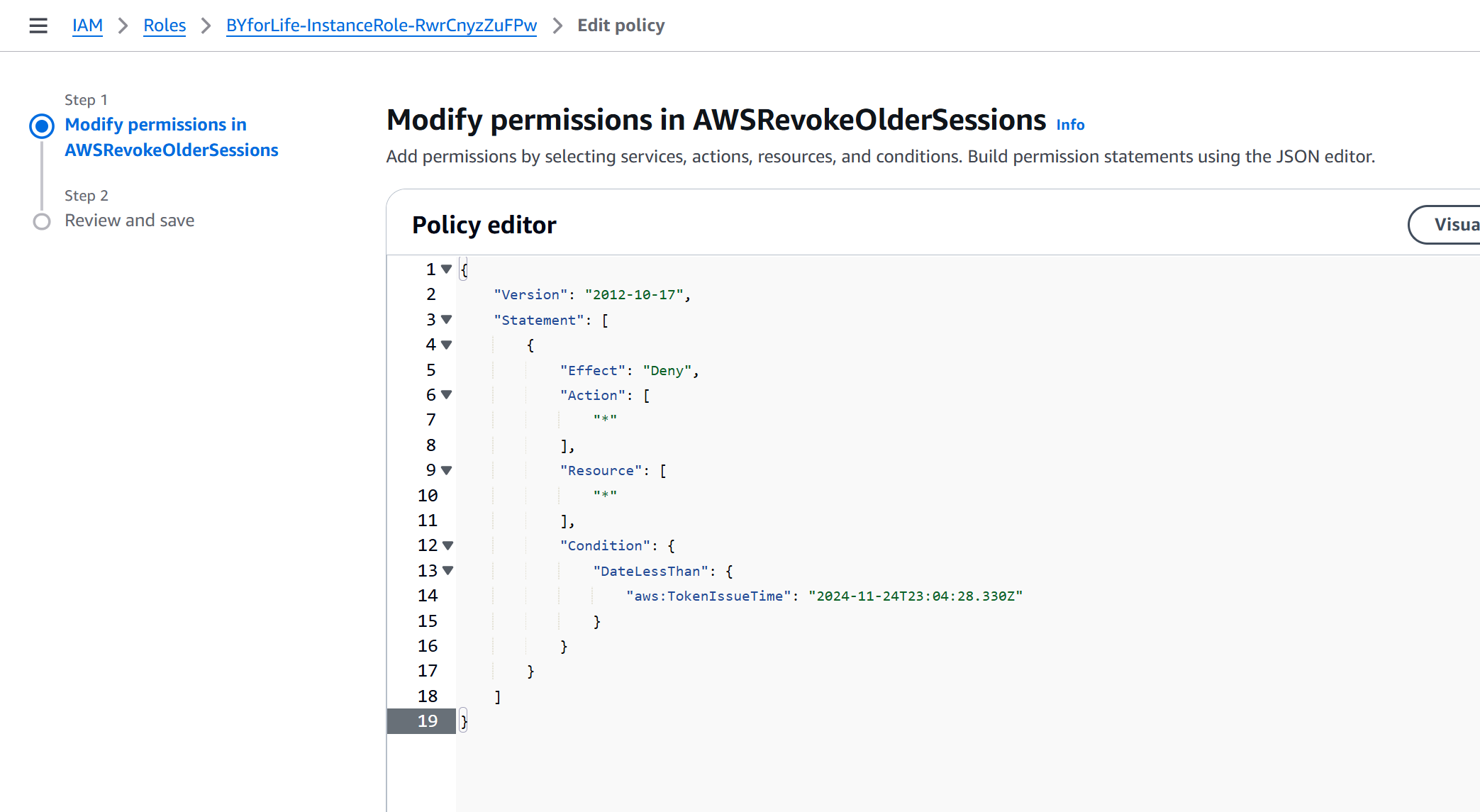
FIX: Update your permissions policy with an AWSRevokeOlderSessions inline deny for any sessions older than right meow. Note: Explicit Deny always overrules Allows
Demo: Revoking IAM Role Temporary Credentials
- Log into the Management account and create this stack: https://console.aws.amazon.com/cloudformation/home?region=us-east-1#/stacks/create/review?templateURL=https://learn-cantrill-labs.s3.amazonaws.com/awscoursedemos/0038-aws-pro-revoking-temporary-credentials/A4LHostingInc.yaml&stackName=A4L
- Gather the IP addresses of the two EC2 instances that have been created.
- Open the IP addresses in a new browser tab
- Connect to instance A and run
curl http://169.254.169.254/latest/meta-data/iam/security-credentials/
- Run this command to grab the security credentials (simulating a bad actor) that basically is the name of your role at the end of it
curl http://169.254.169.254/latest/meta-data/iam/security-credentials/BYforLife-InstanceRole-RwrCsdfhsdjh
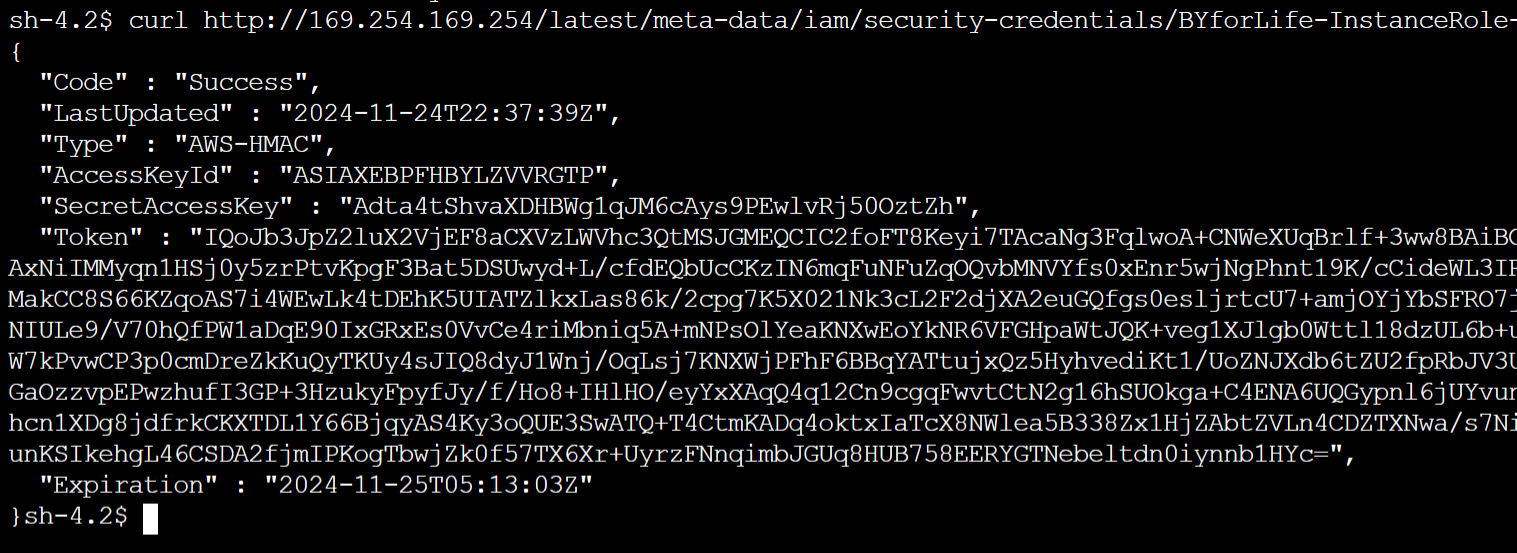 6. Replace the values in this script below
6. Replace the values in this script below
SET AWS_ACCESS_KEY_ID=AKID
SET AWS_SECRET_ACCESS_KEY=SAK
SET AWS_SESSION_TOKEN=TOKEN
- Run the following commands after setting the variables
aws s3 ls
aws ec2 describe-instances --region us-east-1
Now you can interact with S3 as well as EC2. Remember, you cannot invalidate these credentials
Invalidate the credentials
You could delete the entire BYforLife-Instance Role, but that will affect ALL of the services using that role.
- Go to IAM, click on Roles, then click on the Role.
- Click on the Revoke Sessions tab
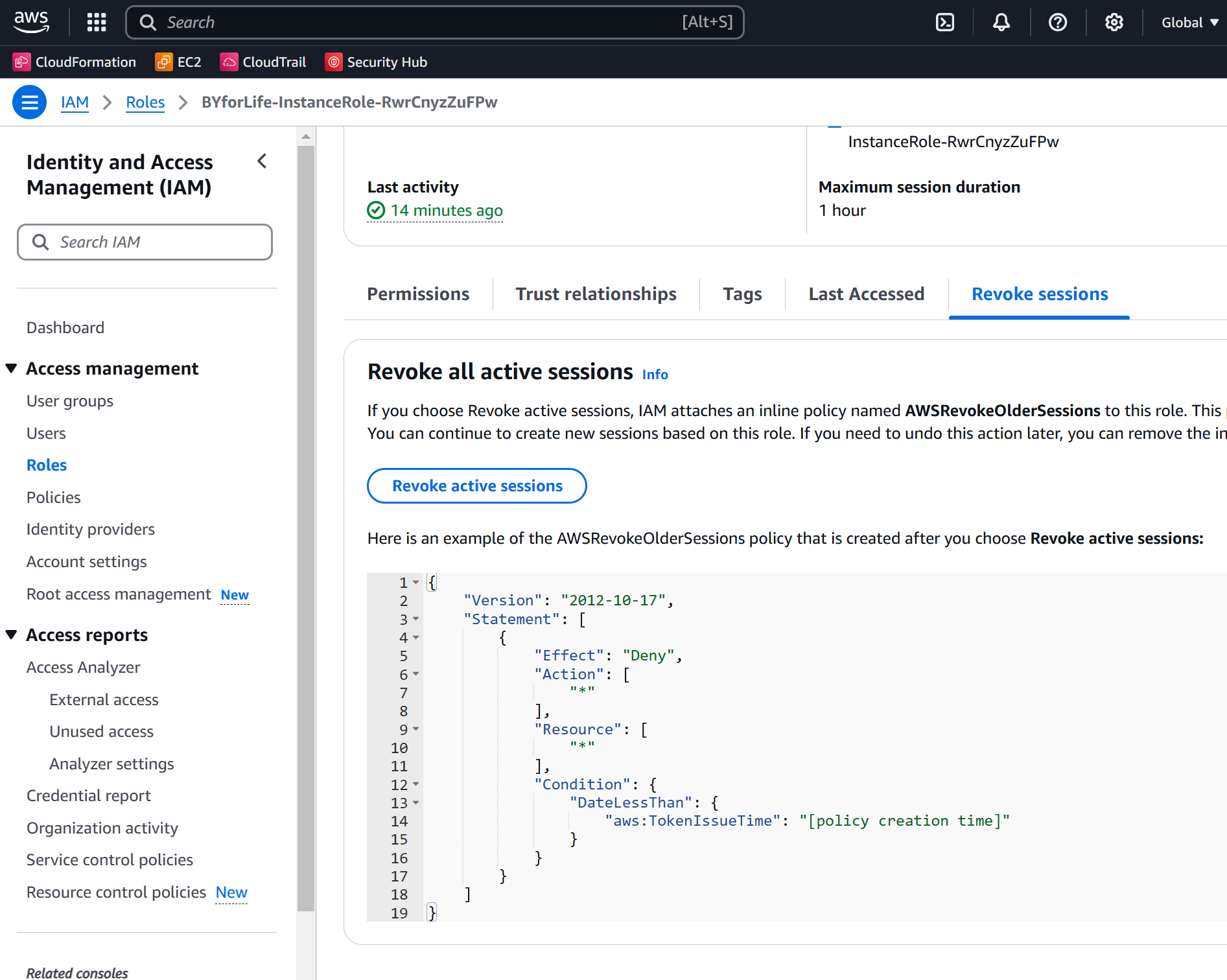
- Click Revoke Active Sessions and click through that.
- Note there is a new inline policy:
- Try to interact with the terminal again and grab the
aws s3 lscommands and you will find that you cannot use them any more - Delete the Customer inline policy that was created, then try to use the
aws s3 lscommand again and find that it works. - You won't be able to access the EC2 instances via Session Manager until you restart the instances - the instances will assume the role again with a NEWER credentials that do not fall under the AWSRevokeOlderSessions policy.
Clean up
Delete the Role (it is tainted with the revoke) Delete the Stack