2. Route 53 Fundamentals
Route 53 based notes
Route 53
Route 53 is a global service and is resilient between regions. Globally scalable and globally resilient.
- Register Domains
- Host Zones - managed nameservers
- Global Service - single database
- Globally Resilient
Register Domains
- You can buy domains via R53 and set up zones via Hosted Zones
- The Zones are on 4 major nameservers.
- Those nameservers become authoritative for that zone.
Hosted Zones
- Hosted Zones are zone files within AWS.
- Can be public or private (Linked to VPCs)
Registering a Domain via Route 53
- Navigate to the Route 53 console
- Click on Register domain
- Search for a domain
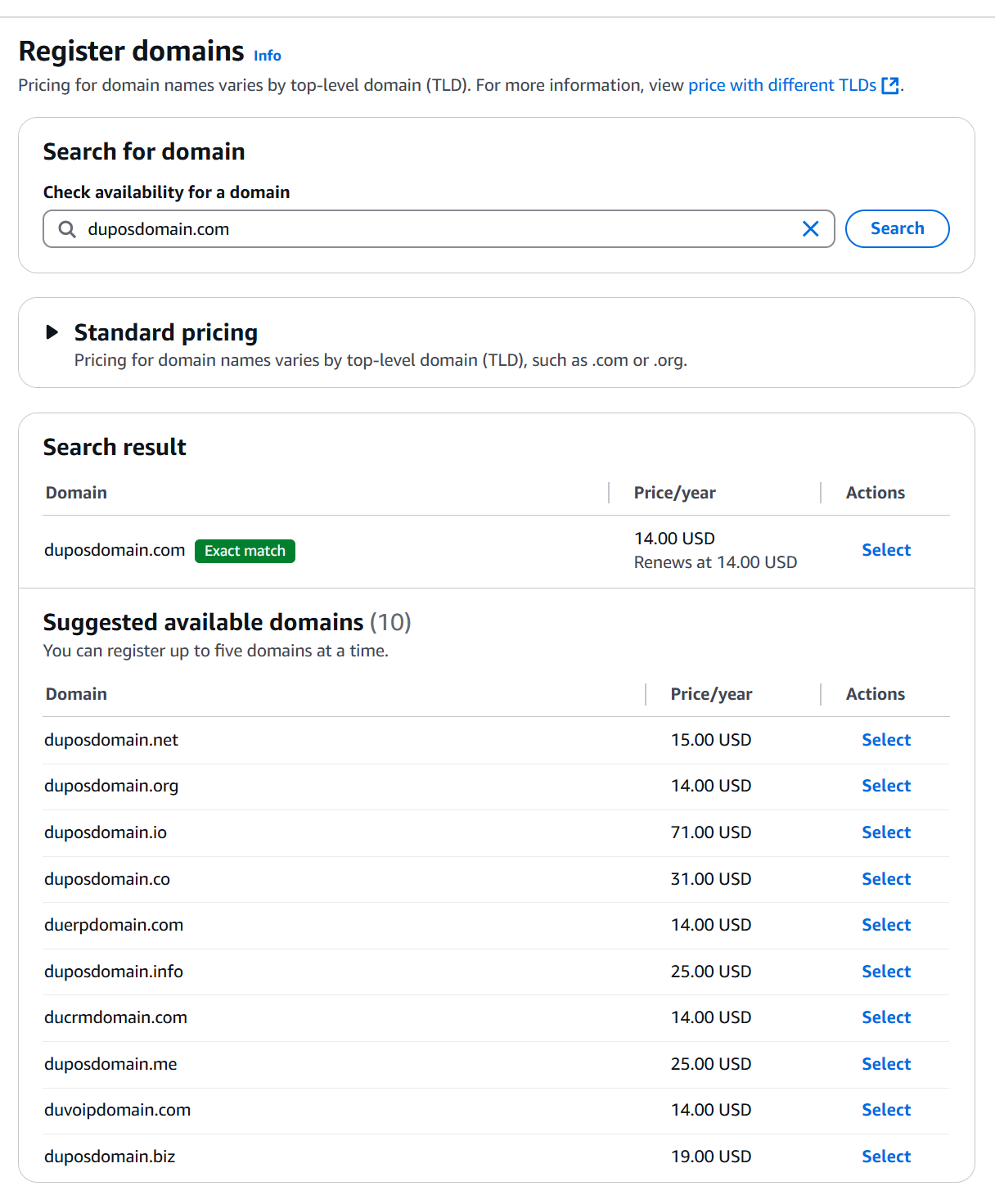
- Pay for it
- Follow the steps to verify the domain
Looking around
- Look for the nameservers
- Look for the hosted zone
DNS 101:
4.3 billion IPv4 Addresses. There are a LOT more IPv6 addresses.
- Most people think this is how it works: www.google.com -> webserver
- How it really works: www.google.com -> IP address -> Zone File - > Name Server -> Webserver
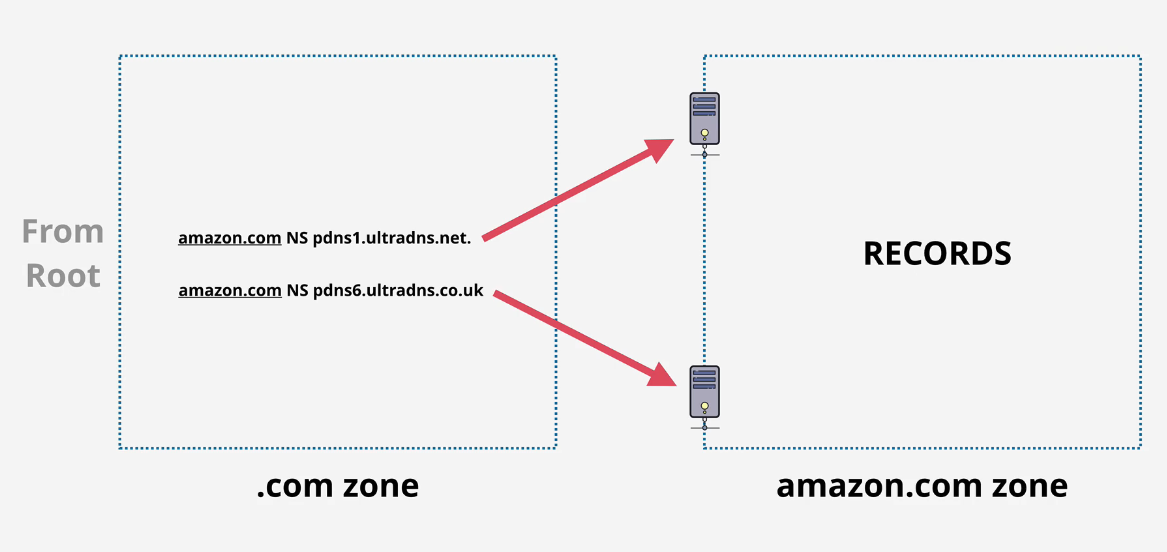
13 DNS Root servers managed by IANA but not hosted by IANA.
Root hints are pointers to those root servers. the .com's and .orgs are top level domain extensions.
So, think of this like an upside down tree. . - IANA .com - IANA but delegated to the companies that hos the gTLDs. duposdomain.com - these nameservers are managed by Dupo mail.duposdomain.com - subdomain that is managed by Dupo.
Terms
DNS Client - Your device (phone, laptop, PC) Resolver - software on your device or a server that queries DNS on your behalf. Zone - dupo.com - a part of this DNS Database Zonefile - physical portion of the zone. Nameserver - the servers where the zonefiles are located. Authoritative - when one thing trusts another in DNS. Root Hints - config that points to the root servers IP's and addresses Root Server - Hosts the DNS Root Zone Root Zone - Points at the TLD authoritative servers gTLD - generic Top level Domain - .com .org .net ccTLD - country code top level domain: .us. uk .eu .au
DNS Record Types
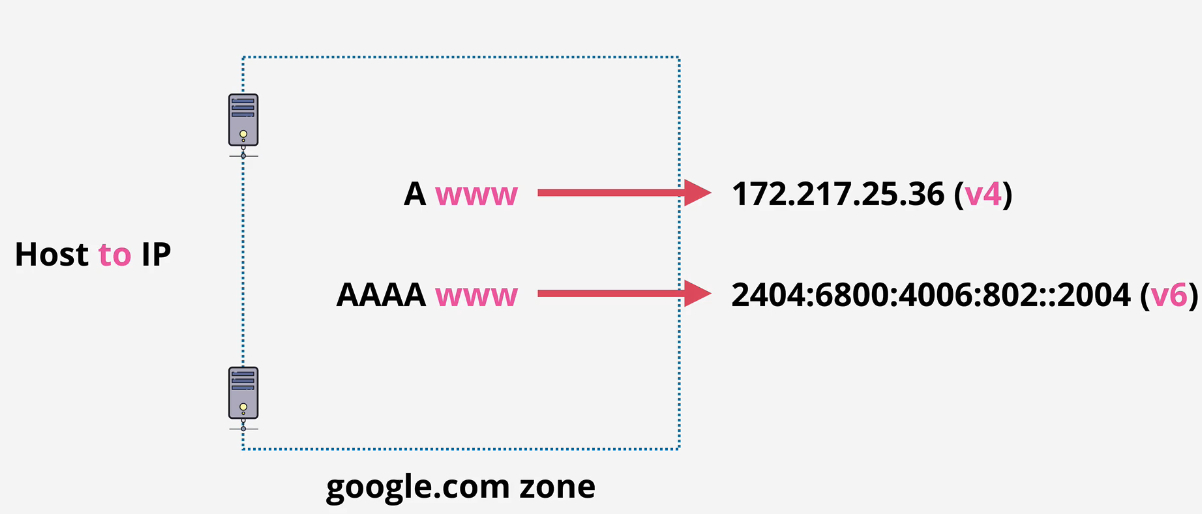
NS - Nameserver records
A- IPv4 address
AAAA - IPv6 address
 CNAME - Canonical Name
CNAME - Canonical Name
- points to another name
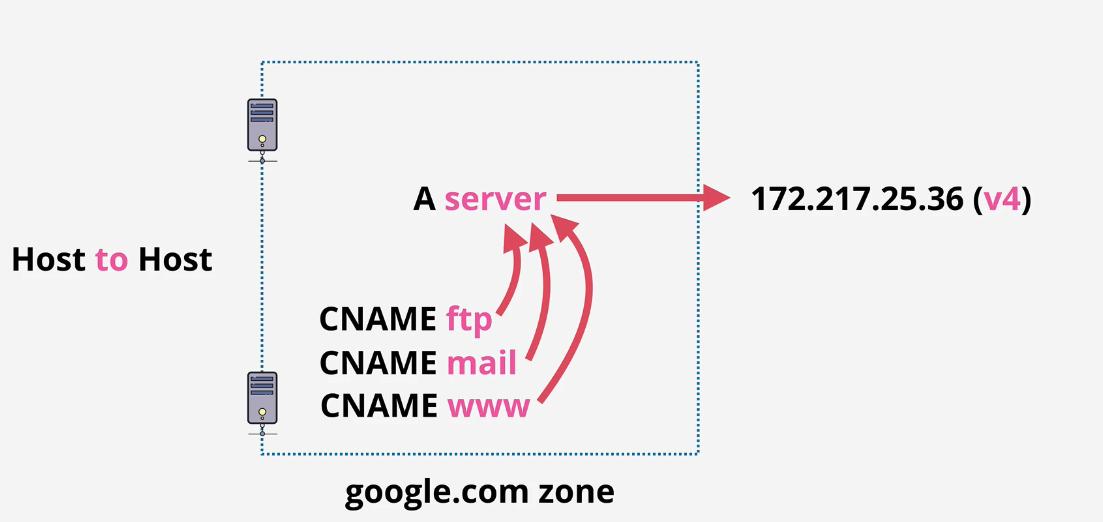
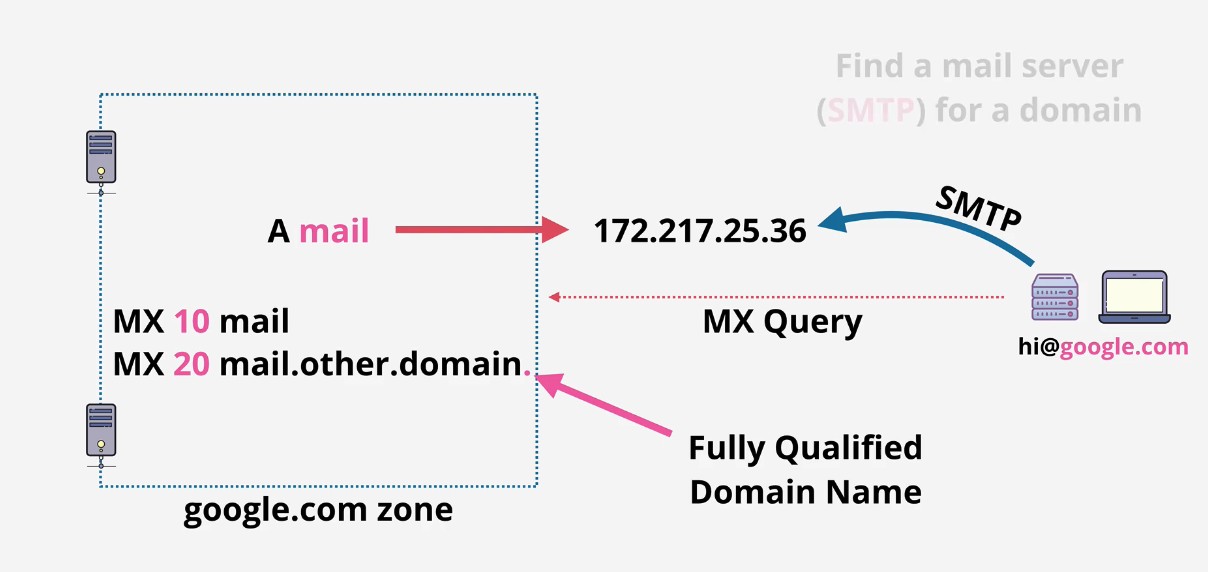
MX - mail record
- has priority values - lower is higher priority.
TXT - prove domain ownership
- you add some text to the record and some service will query and find that text data to confirm ownership.
TTL
TTL isn't a record type, but it's a time to live attribute that is appended to these records. It takes time to "walk the tree" so it sets a time that that resolution is trusted.
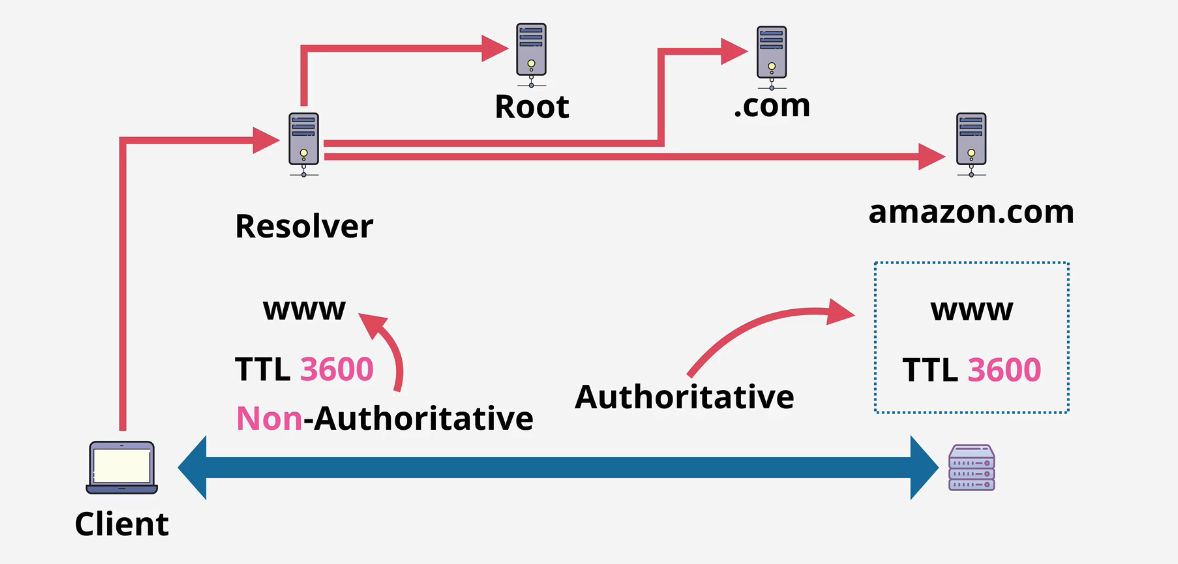
Non-authoritative are quicker due to when they are cached If something is changed, then someone will need to hit the new record and create a new authorative TTL which will cache into a non-authoritative TTL
- Lower the TTLs when you change DNS in advance.
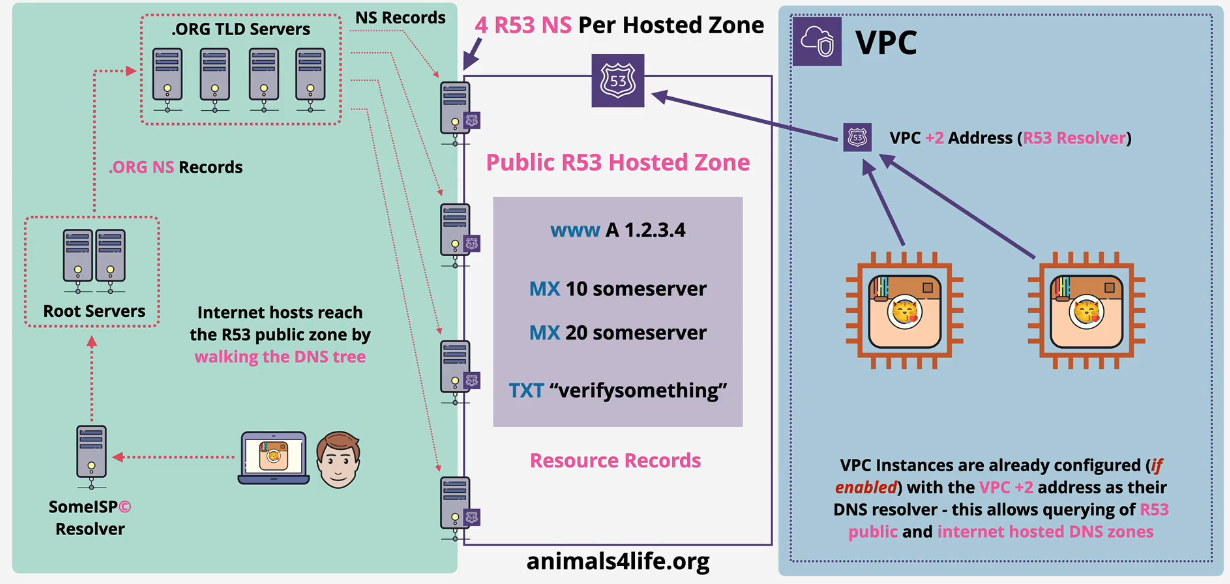
Route53 Public Hosted Zones
Globally resilient zone. Automatically created with domain registration in R53.
These hosted zones will hold the DNS Records (A, AAAA, CNAME, etc)
These are authoritative for the domain that you host.
- You can purchase a domain using another registrar and point them to AWS Route 53's nameservers for a hosted zone.
While in a VPC, you can use the VPC+2 address (which is the Route 53 Resolver) to talk to the Public Route 53 Hosted Zone.
Walking the tree
This is when you try to resolve something from within DNS
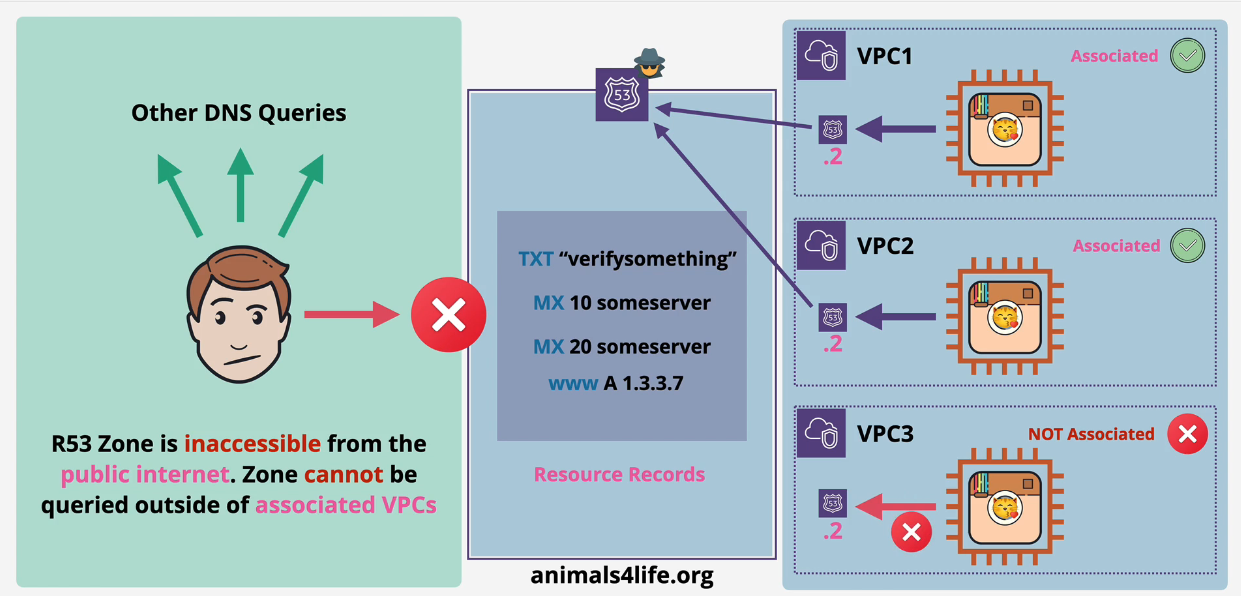
Route53 Private Hosted Zones
Used for communication between VPCs
- only accessible in those VPCs
- can be used across accounts via CLI or API
- Can use Split DNS which is Public and Internal use with the same domain name.
- VPC's will use the VPC+2 - x.x.x.2 IP address with R53.
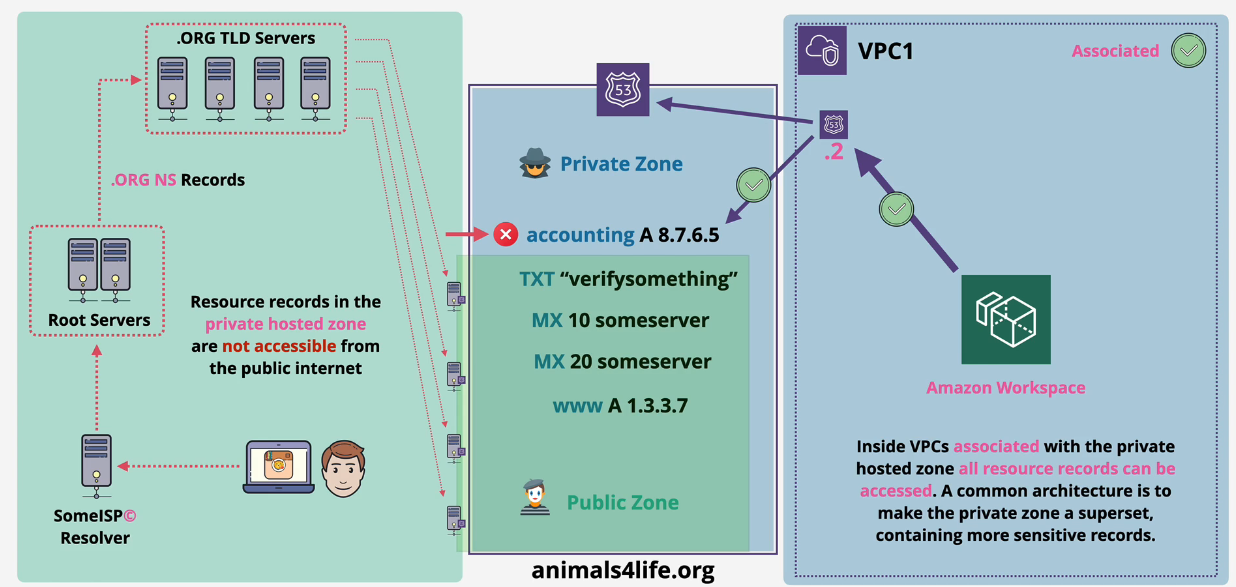
Split Horizon DNS
Companies can use a split DNS on duposdomain.com where the public and private zones share the same domain name.
This overlapping allows for deeper configuration whether you are on the private network or out in the public network.
CNAME vs Alias
There's a difference between these two.
-
A record maps a name to an address - google.com is mapped to 8.8.8.8
-
CNAME record maps a name to another name - www.google.com to google.com But... you can't map the naked (apex of the) domain google.com to anything (load balancer for example) using a CNAME You can map www.google.com to the LB but not google.com
-
ALIAS maps a NAME to an AWS Resource
The solution is to use an alias record.
Important:
- There is no charge to use an ALIAS request that points at an AWS resource.
- Should be the same "Type" as what the record is pointing at.
- For AWS Services, default to using ALIAS
- Can be used for naked/apex and normal records
What is the difference between a CNAME and an Alias? CNAME on steroids that can point to the naked apex domain - .google.com
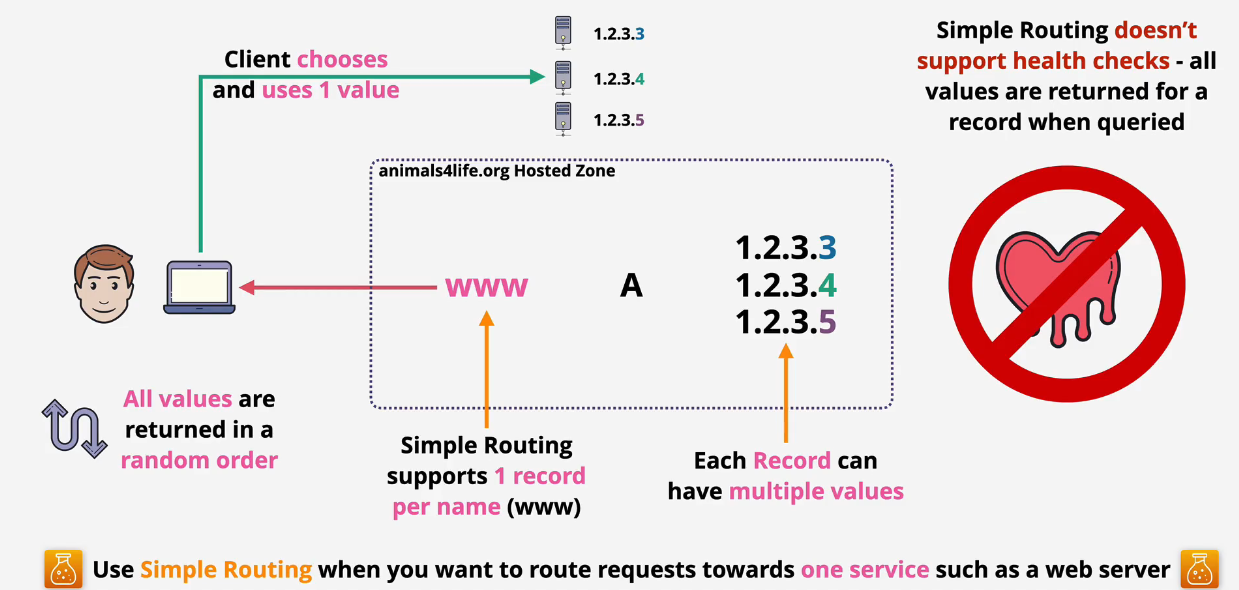
Route 53 Simple Routing
Simple routing is used when you want to route to one single service such as a web server.
- Does not support health checks
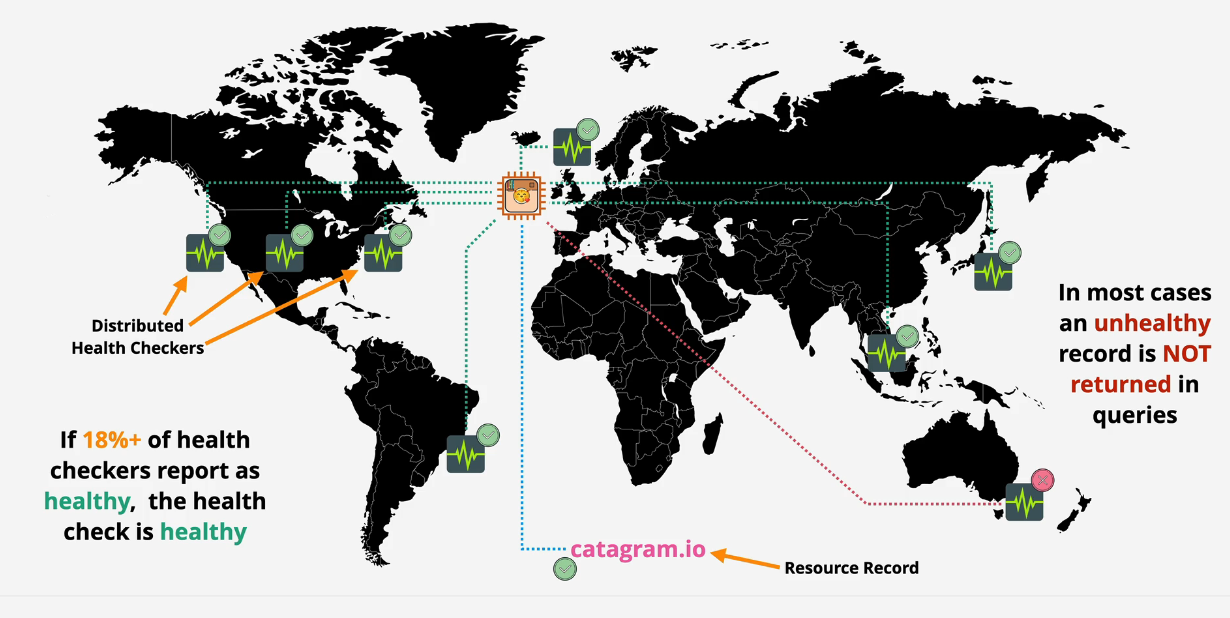
Route 53 Health Checks
Health checks are separate from, but are used by records
- located globally
- Check every 30 seconds - every 10 seconds on top of that costs $
- These are either Healthy or Unhealthy
- Endpoint, CloudWatch Alarm, Checks of Checks (calculated checks) TCP, HTTP/HTTPS or HTTP/HTTPS with String Matching
You can attach a health check and global distributed checkers can check this health check
- if 18%+ of those distributed health checkers report healthy, then it's healthy.
- Go to the Route 53 console
- Click Health Checks
- Create Health Check
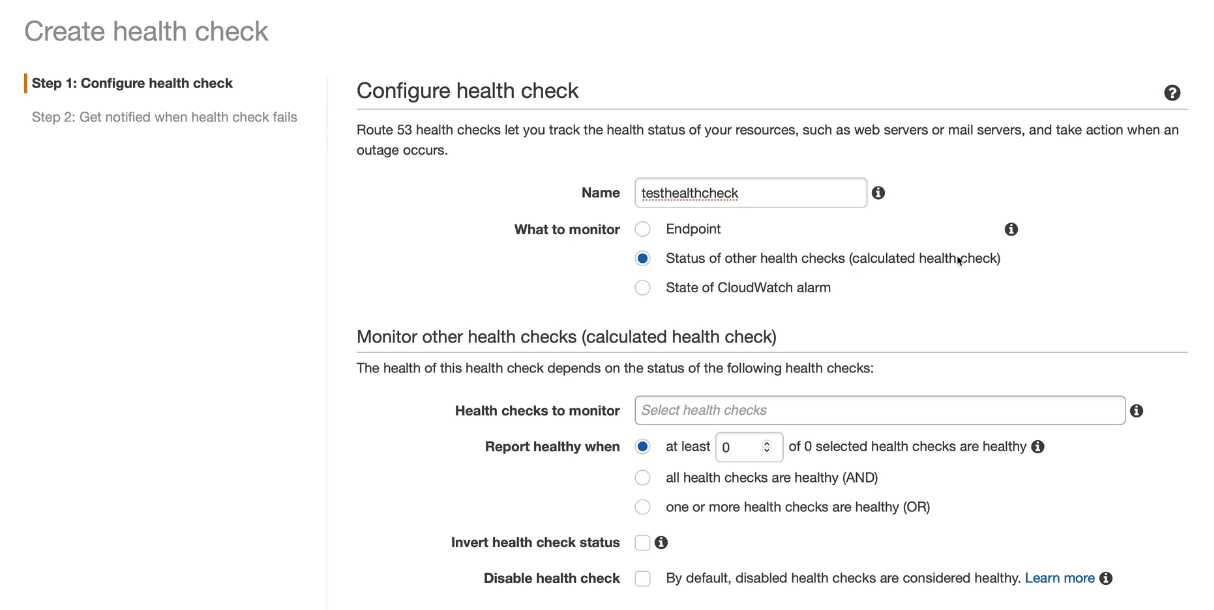
- Select Endpoints and host names and the rest of the info
- Create Health Check.
- Test
Can invert the healthcheck too
Can disable the check
Can specify regions
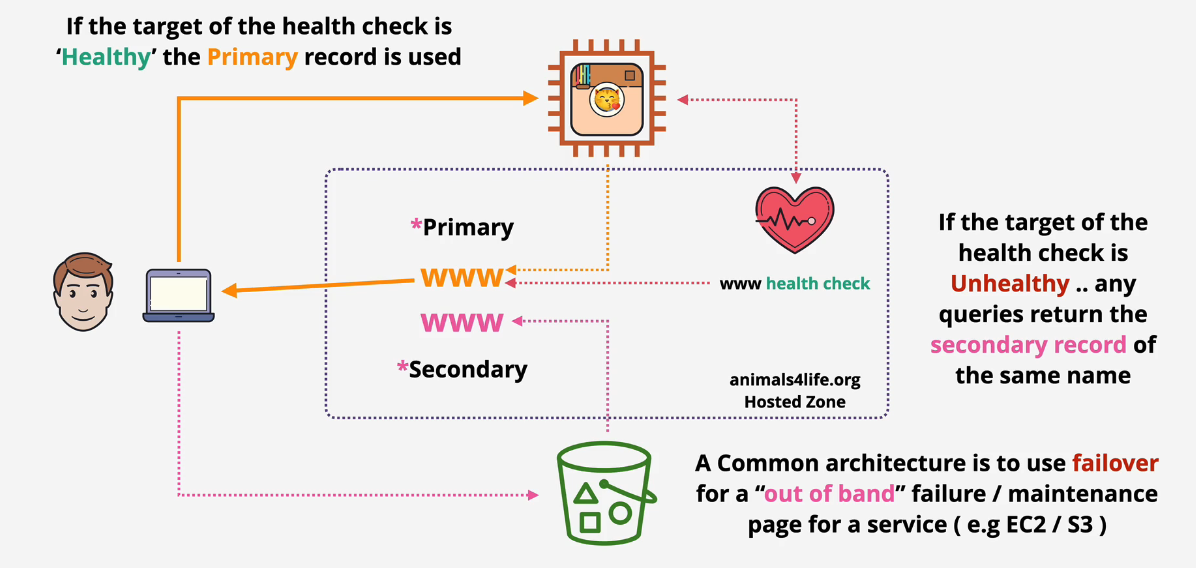
Route 53 Failover Routing
Allows health checks to check against the primary resource/record and then redirect to a secondary if the health checks fail. You can use this in an active/passive failover.
Active Passive Failover
Redirect to an S3 static page when the primary health checks fail.
- Maintenance page
Demo: Route 53 Failover Routing
You will need a domain name within AWS and a Hosted Zone set up.
- Deploy the stack: https://console.aws.amazon.com/cloudformation/home?region=us-east-1#/stacks/create/review?templateURL=https://learn-cantrill-labs.s3.amazonaws.com/awscoursedemos/0027-aws-associate-dns-failover-and-private-zones/A4L_VPC_PUBLICINSTANCE.yaml&stackName=DNSANDFAILOVERDEMO
- Find the Web EC2 instance, open up the public IPv4 address in a browser
- Associate a new Elastic IP address to the Web EC2 instance
- Create a new S3 bucket and set it up as a static bucket - make sure the name of the bucket is the same as your domain name: www.duposdomain.com
- Upload your index.html maintenance page to this S3 bucket
- Set the bucket policy to public.
- Verify that you can reach the static page via URL
- Navigate to Route 53 and create a new Health Check
- Add the IP address to the health check and validate that it is healthy.
- No alarm is created unless you want to create it.
- Create a failover record on your domain
- Define your main failover record - the EC2 instance
- Define your S3 Failover record - for the S3 bucket
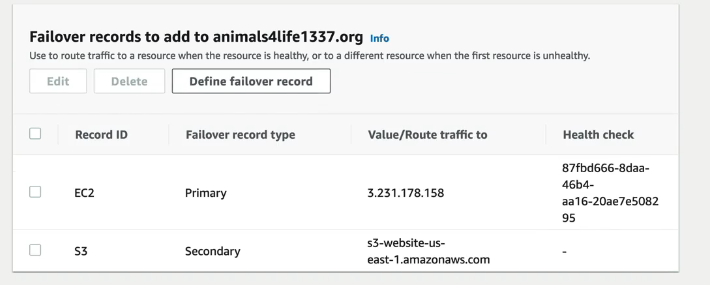
- The domain should direct to the website on the EC2 instance
- Stop the instance ( do not terminate)
- Notice that the health check will start to failure and move into an unhealthy state
- Wait for the DNS Cache to clear out if needed, and you will then find your index.html on your S3 Bucket when hitting the www.duposdomain.com URL.
- Restart the EC2 instance and you will find that the health check will become healthy and start routing traffic back to the EC2 instance.
Private hosting zone
- Create a private hosted zone (you don't need to own the domain)
- Select the default VPC
- Create a new record - A, www. and a random IP address, TTL 60 seconds
- Connect to the EC2 instance and try to ping the www.madeupdomain.com and it will fail.
- Add the other VPC to the record - wait and you will be able to ping that IP address.
Clean up
Remove Private Hosted Zone Remove the Health Check Remove the Elastic IP Delete S3 Bucket Remove the stack.
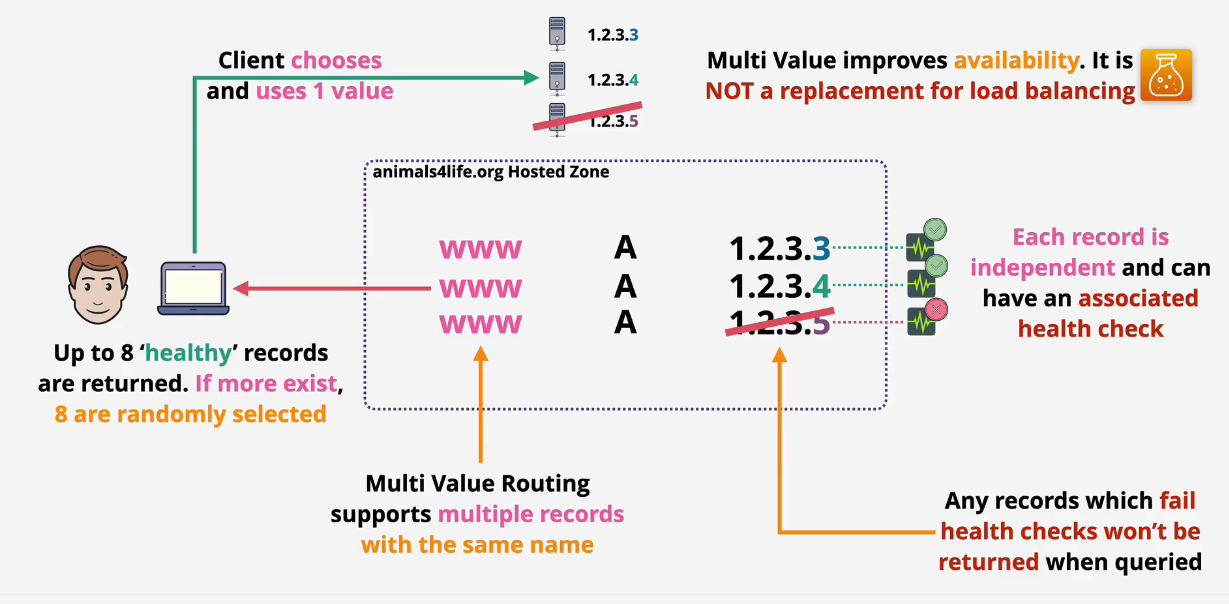
Multi Value Routing
A mix between simple and failover routing.
This is used when you want to assign multiple IP addresses to a record. This allows for higher availability but is not a replacement for load balancing. The reason why this isn't a replacement for load balancing is that the client can choose which server they connect to and if all users choose one IP, then they aren't load balanced at all.
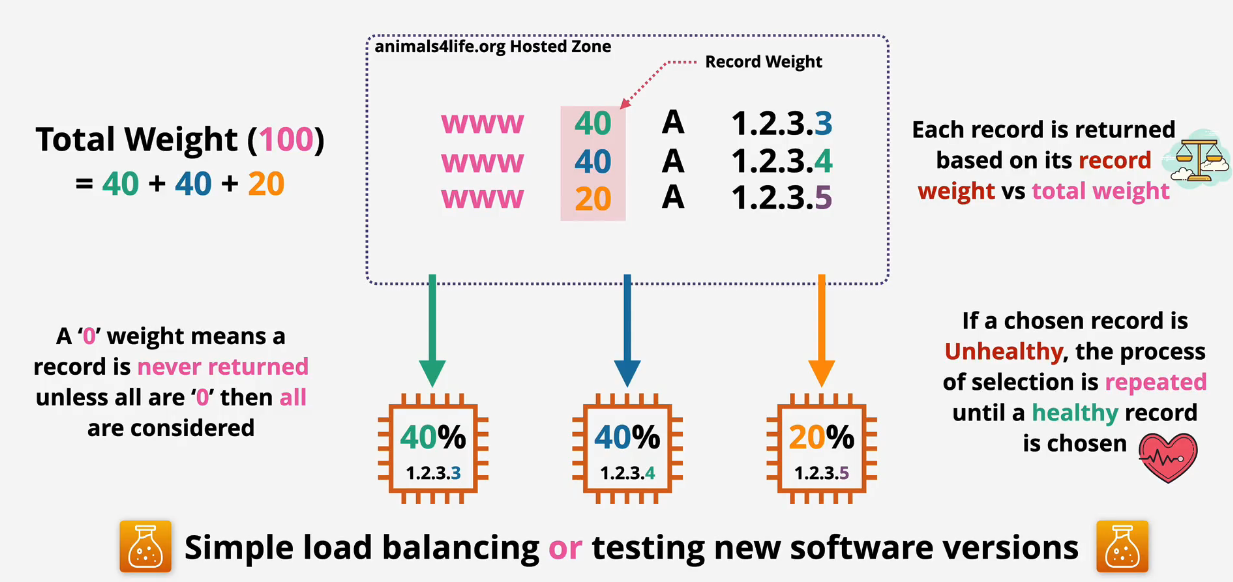
Weighted Routing
Used for simple load balancing or when you want to test new versions of your application.
- 1.2.3.4 - 40%
- 1.2.3.5 - 40%
- 1.2.3.6 - 20%
Routing that is set to 0 has no traffic sent to it.
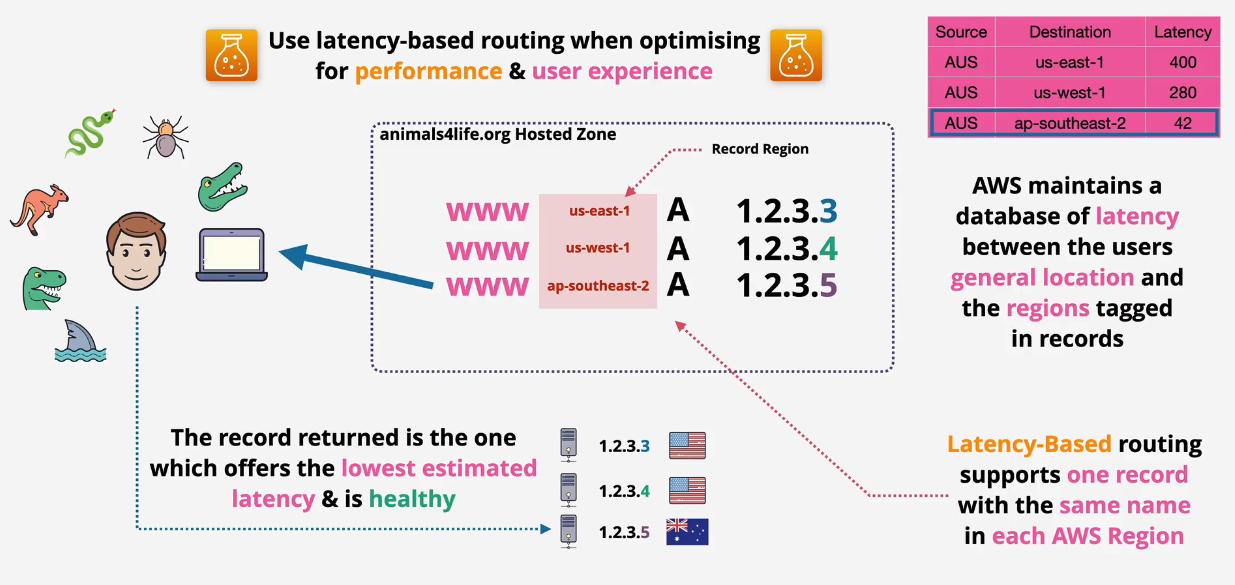
Latency Based Routing
Use Latency-based routing when optimizing for performance and user experience :)
AWS keeps a latency table from certain locations to other locations. For example, it uses an IP lookup to see where the source is coming from and then determines the latency to other destinations from that source.
The record that is returned to the user has the lowest latency and also needs to be the one with valid health checks.
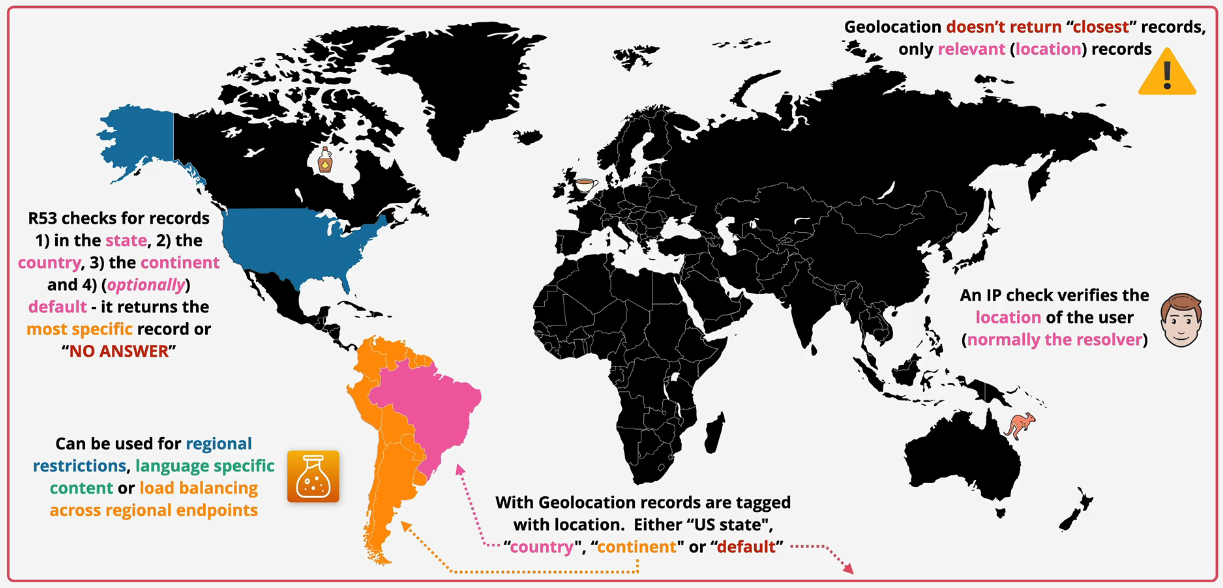
Geolocation Routing
This does not return the closest route. This restricts traffic based on location. An IP address lookup determines the source. This is first checked against the state. Then it is checked against the country, and then finally the continent for related matching records.
If nothing is matched, then it returns the default. If there is no default, then it returns a no answer.
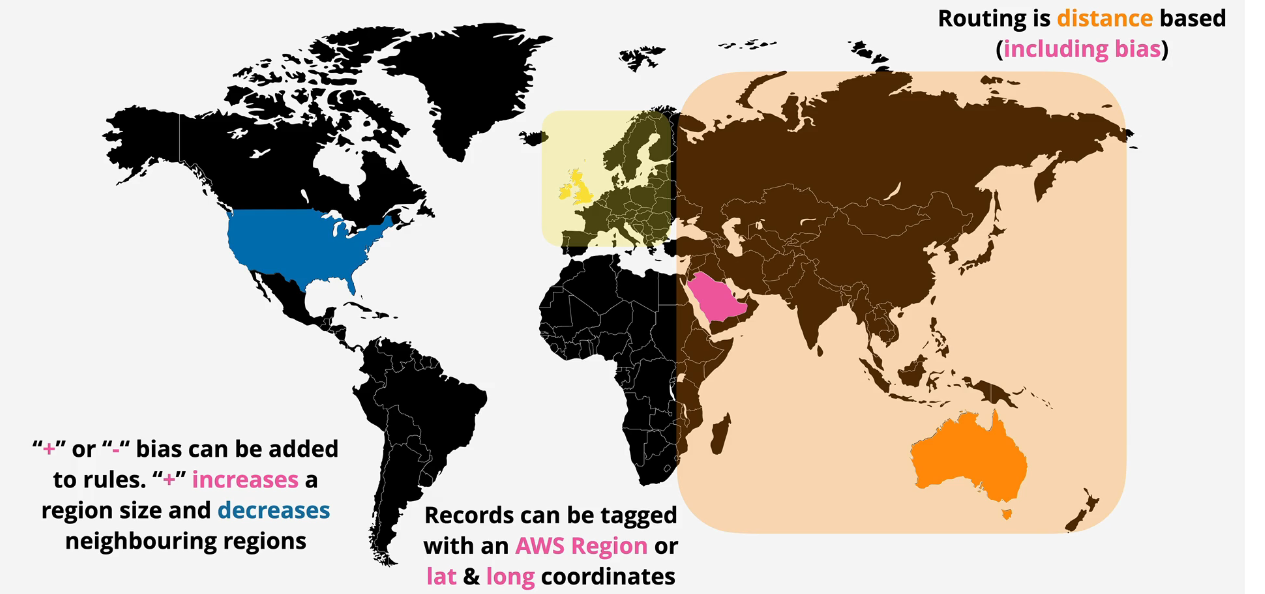
Geoproximity based Routing
This uses the shortest, closest record to the client's location. If the client is in Japan, it will return the closest record to Japan.
- You can add a bias to this to extend the area that you want to include. That way if you are closer to a place such as the UK, you can use that bias to send to a different location.
Route53 Interoperability
- Domain Hosting and Domain Registrar
- Interoperability means Domain Hosting or Domain Registrar
- When you buy a domain from AWS and have the zone hosted here, you use both.
- I do see domains registered by 3rd parties that then have their nameservers updated to the 4 that AWS gives when you host a zone in Route 53.
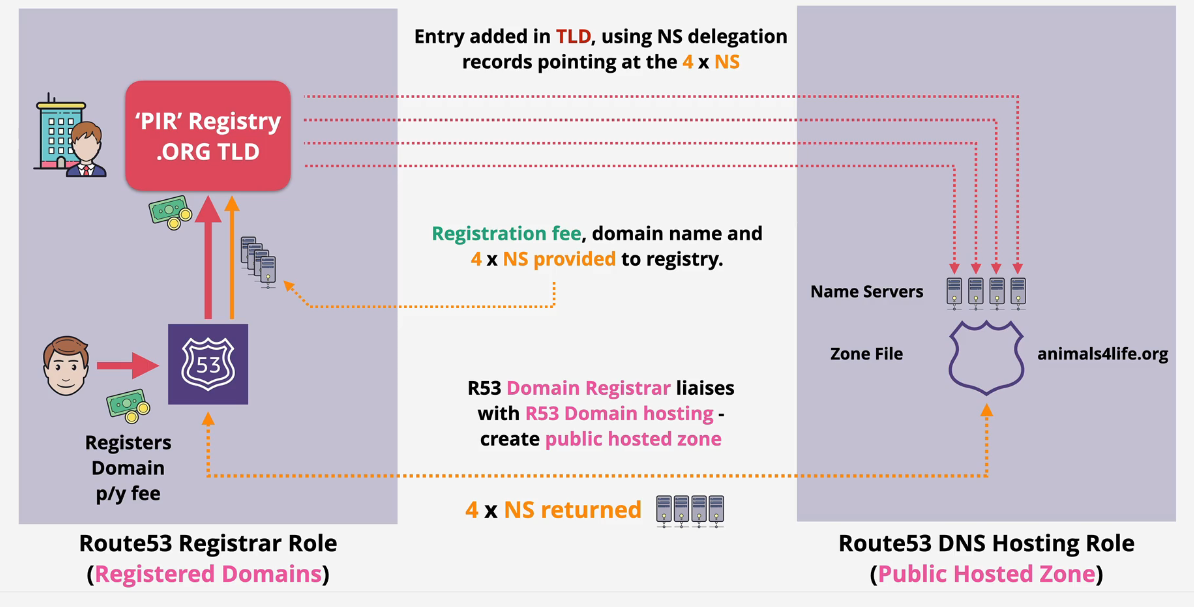
Both Roles
Registrar and DNS Hosting Zone
- You register the domain AND host the zone in AWS Route 53.
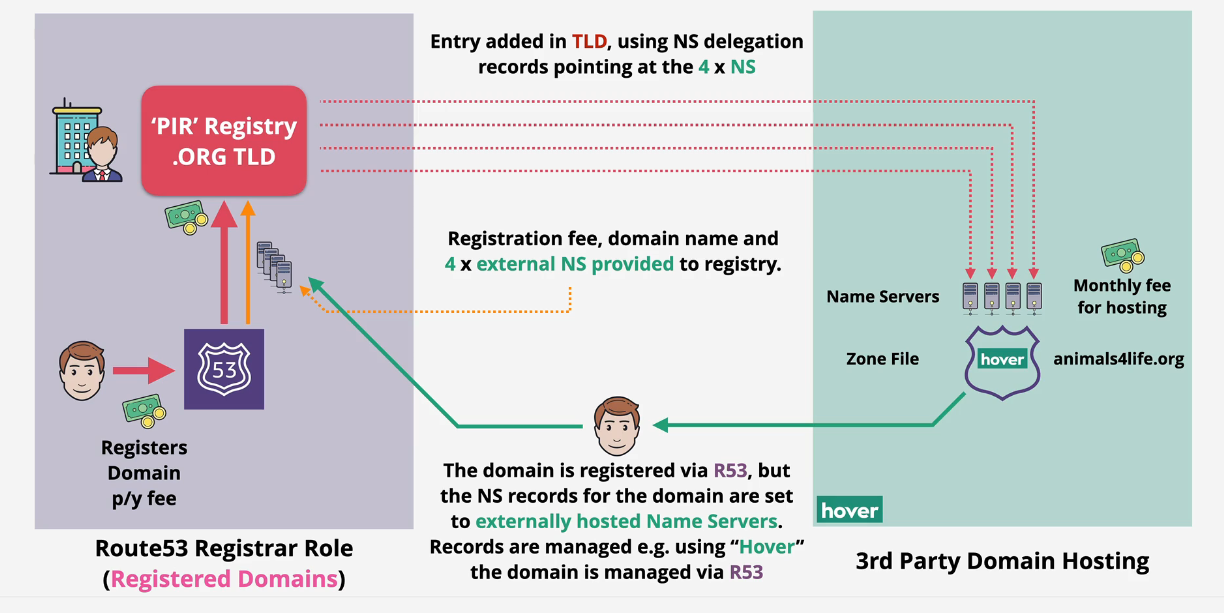
Registrar only
Buy your domain at AWS, host the DNS elsewhere
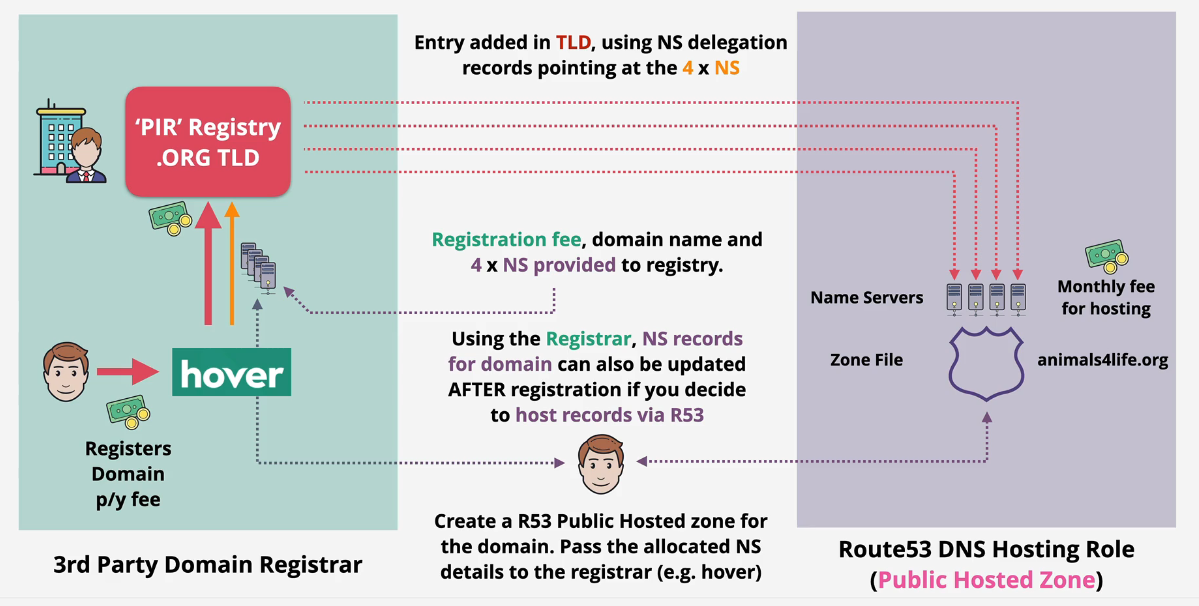
Hosting only
Buy your domain somewhere else, point to Route 53 Hosted Zone
DNSSEC with Route 53
DNSSEC strengthens authentication in DNS using digital signatures based on public key cryptography. With DNSSEC, it's not DNS queries and responses themselves that are cryptographically signed, but rather DNS data itself is signed by the owner of the data.
When you enable this, make sure you note the TTL of your DNS records. Create your Key signing Key (KSK) and it will create your Zone Signing Key - this will enable automatically
You then need to associate that to the domain under the DNSSEC status to establish the chain of trust: