[[TOC]]
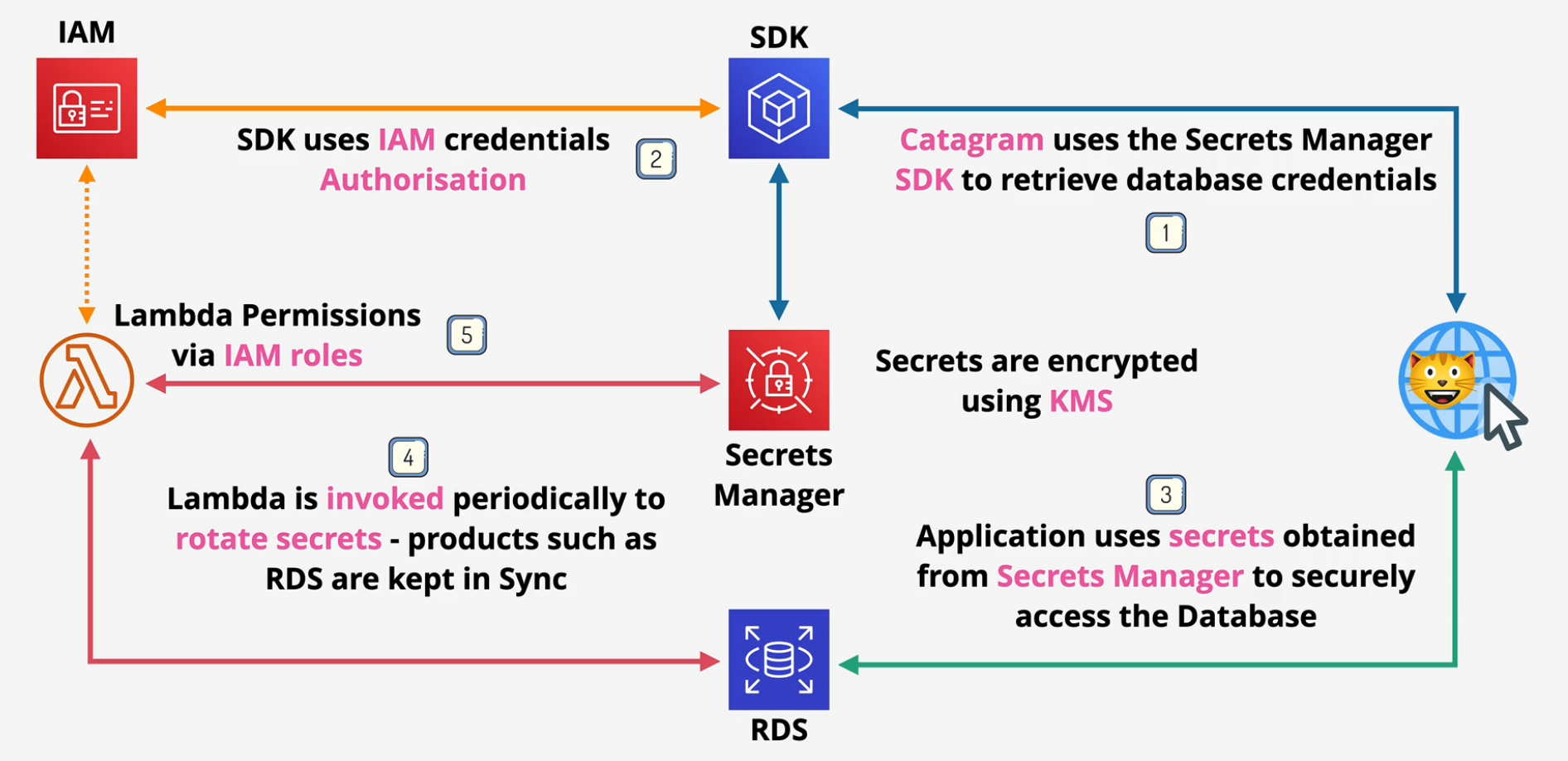
AWS Secrets Manager
This gets confused with the SSM Parameter store.
- designed for secrets (passwords, API keys)
- usable via Console, CLI, API, SDks
- Supports automatic rotation using Lambda
- Directly integrates with some AWS products (RDS)
- Use keyword analysis
- Secrets
- Rotation
- RDS - product integration.
Implementation
Uses KMS
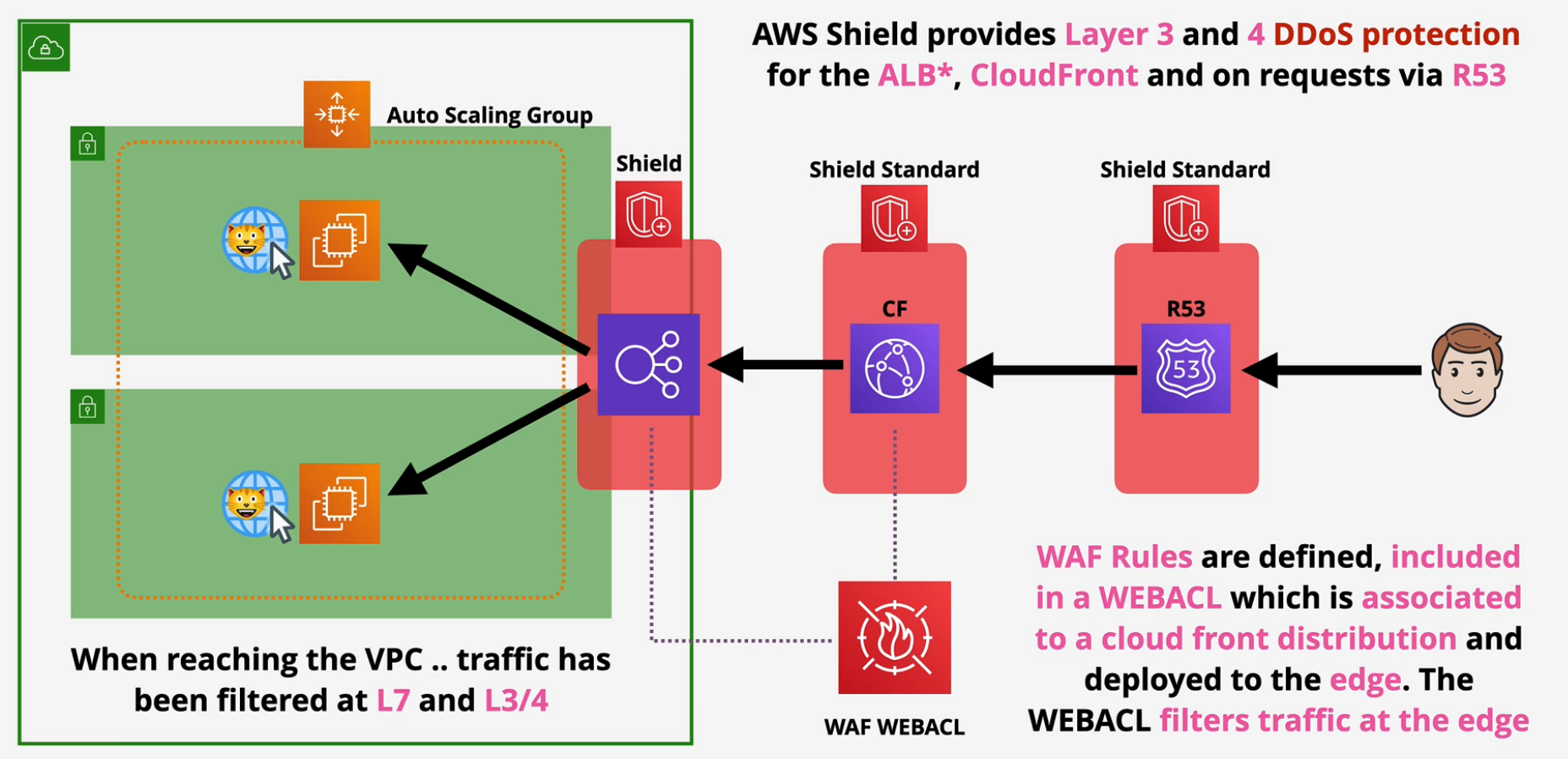
AWS Shield and Web Application Firewall (WAF)
Provides AWS Resources with DDoS protection.
Shield Standard - free with Route53 and CloudFront
- Protection against Layer 3 and Layer 4 DDoS Attacks
Shield Advanced - $3000/per month
- EC2, ELB, CloudFront, Global Accelerator and R53
- DDoS response team and financial insurance
WAF
Layer 7 Firewall - HTTP/s Firewall Protects against Layer 7 attacks/exploits SQL injections, Cross site scripting, geo blocks, rate awareness
- Web access control list (WEBACL) integrated with ALB, API gateway and CloudFront
- Rules are added to this WEBACL and evaluated when traffic arrives.
- Use Shield and WAF together.
Exam tips:
- Link DDoS with Shield Layer 3 and 4
- Link Layer 7, HTTP filtering with WAF
- Global Perimeter protection
CloudHSM
This is confused with KMS sometimes. KMS is shared but it's separated. HSM = Hardware Security Module AWS provisioned, but fully customer managed.
KMS can use CloudHSM as a custom key store - CloudHSM integration with KMS
HSM is not highly available - one AZ. You can create multiple HSMs that are kept in sync with each others in your VPC. AWS cannot access the partitions - fully customer
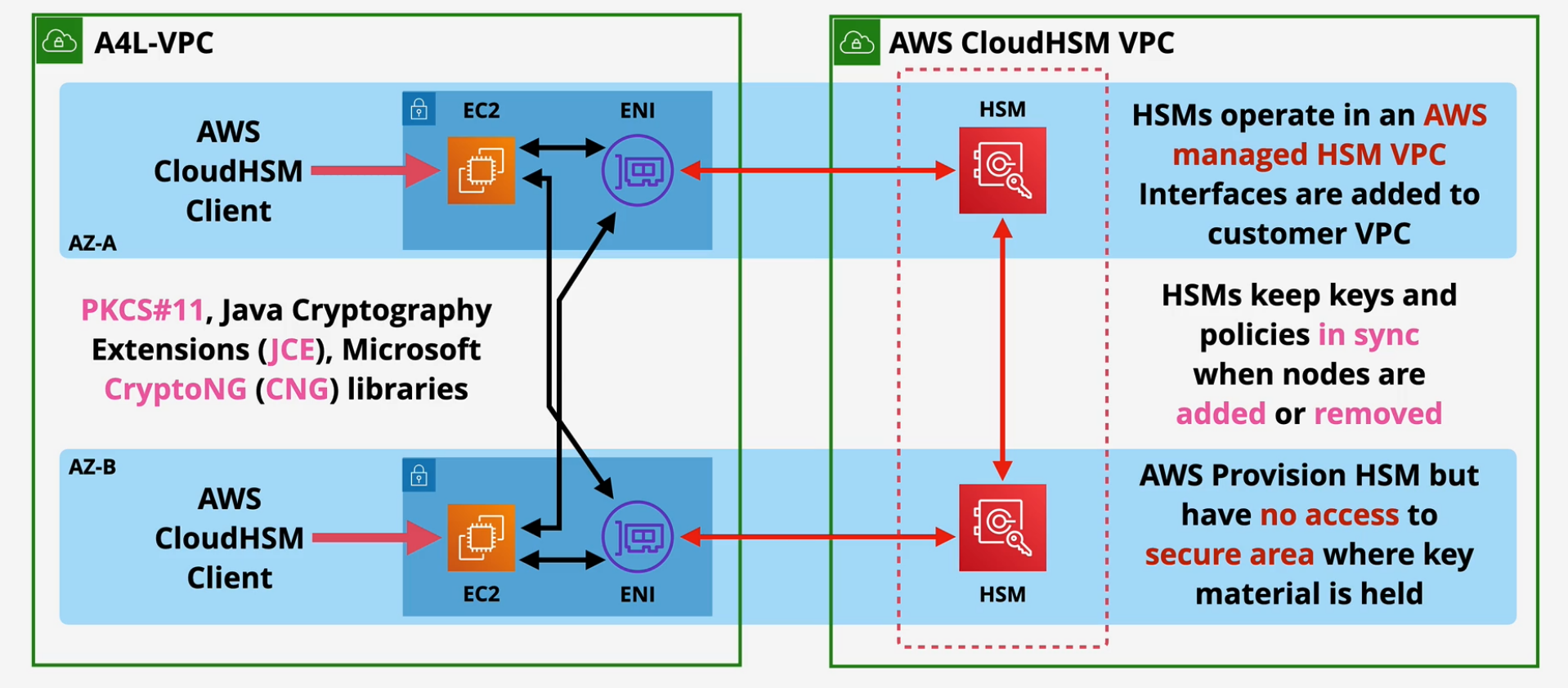
Exam Tips
- Cloud HSM = FIPS 140-2 Level 3 Compliant. KMS is more L2 with some L3.
- PKCS#11, JCE, CryptoNG (CNG) libraries
- no native AWS integrations
- offload SSL/TLS processing for Web Servers
- Enable Transparent Data Encryption (TDE) for Oracle Databases
- Protect the private keys for an issuing Certificate Authority (CA)
- Anything that requires AWS integration should not be HSM
- If you need to encrypt firm standard APIs, HSM
AWS Config
Records configuration changes over time on resources
- Auditing of changes, compliance with standards
- Does not prevent changes from happening - zero protection
- Regional service - supports cross region and account aggregation.
- Changes can generate SNS notifications and near real-time events via EventBridge and Lambda - you can build in some lambda for remediation.
Enable the recorder and set it to a config bucket. You can then set config rules to show resources as compliant or non compliant. Config can notify other services for notification or remediation (SNS, Eventbridge, Lambda)
Amazon Macie
Data security and data privacy service.
- Discover, monitor, and protect data stored in S3 buckets
- Automated discovery of PII, PHI or finance data.
- Policies such as S3BlockPublicAccessDisabled or S3BucketEncryptionDisabled
- Sensitive data such as S3Object/Credentials or S3Object/Personal
Two types of identifiers
- Managed Data identifiers - built in
- Custom Data Identifiers - proprietary - regex based
- Keywords
- Maximum match distance - how close to the regex
- Ignore words - words that Macie skips over.
Macie integrates with Security Hub and finding events to Eventbridge
Macie is Multi-Account via Organizations or by invitation.
Implementation
Set up S3 buckets Set up Macie Data Discovery Job with identifiers. Findings - Policy or Sensitive data findings Finding Event to EventBridge to Lambda.
AWS Inspector
Scans EC2 instances and the instance OS for vulnerabilities against best practice Can be configured to run every 15 minutes, hour, 8/12/24 hours. Security report on those instances can be produced
- Network assessment (agentless)
- Network and host assessment (agents)
- Checks reachability from end to end.
- CVE inspection package needs an agent
- CIS needs an agent.
- Security best packages for Amazon Inspector
Amazon GuardDuty
Continuous security monitoring service Analysis supported Data Sources plus AI/Machine learning plus threat intelligence feeds
- identifies unexpected and unauthorized activity.
- Can set up notifications or event-driven protection/remediation
- Supports Master and Member accounts
- send findings to Cloudwatch Events or EventBridge to either send SNS or Lambda