[[TOC]]
VPC Flow Logs
- Only captures the capture metadata NOT THE CONTENTS - need a packet sniffer for that.
- Attached to a VPC - all ENIs on that VPC
- or the subnet
- or ENI's directly
- Flow logs are NOT realtime
- Log destinations include S3 or CloudWatch logs or Athena for querying.
Flow logs capture all metadata from the capture point downward.
Important:
- ICMP = 1
- TCP = 6
- UDP = 17
VPC Logs exclude access to the metadata services, DHCP, DNS and Windows License Server are not recorded.
Egress-only Internet Gateway
- IPv4 addresses are private or public
- NAT allows private IPs to access Public Networks without allowing externally initiated connections IN
- The problem is that all IPv6 IPs are Public
- IPv6 then allows all IPs IN and OUT.
- NAT doesn't work with IPv6.
You see the problem, right?
Egress-only is outbound only for IPv6.
Egress-only is the same as the Internet Gateway
- HA
- scales as required.
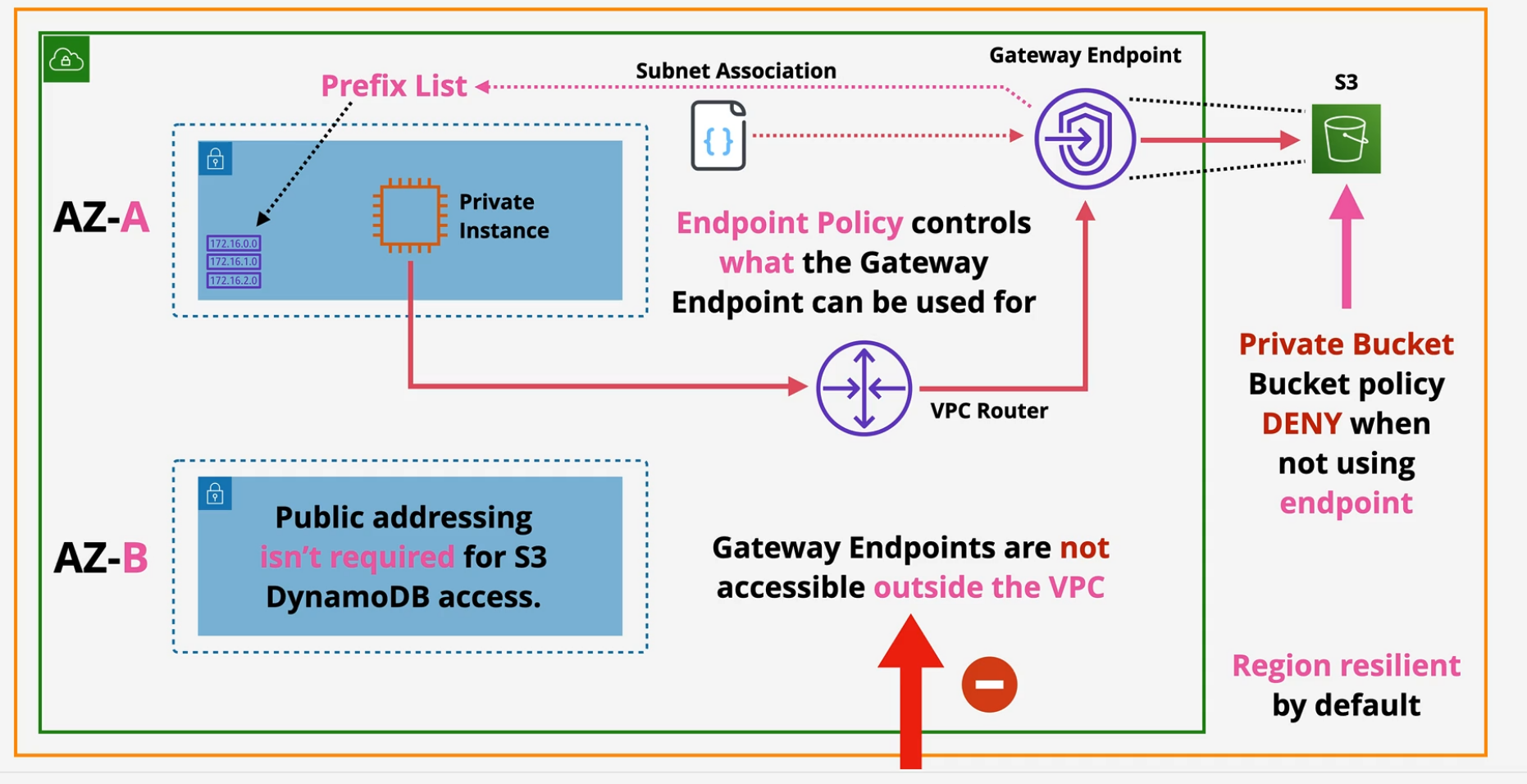
VPC Endpoints - Gateway
Gateway endpoints provide private access to S3 and DynamoDB
- created per service per region.
- prefix list is added to the route table -> gateway endpoint
- HA across all AZs in a region by default
- Endpoint policy is used to control what it can access
- Regional - cannot access cross region services - cannot access S3 buckets across different regions.
- These prevent Leaky Buckets - can be set to private only by allowing access only from a gateway endpoint.
- Gateway Endpoints are not accessible outside the VPC.
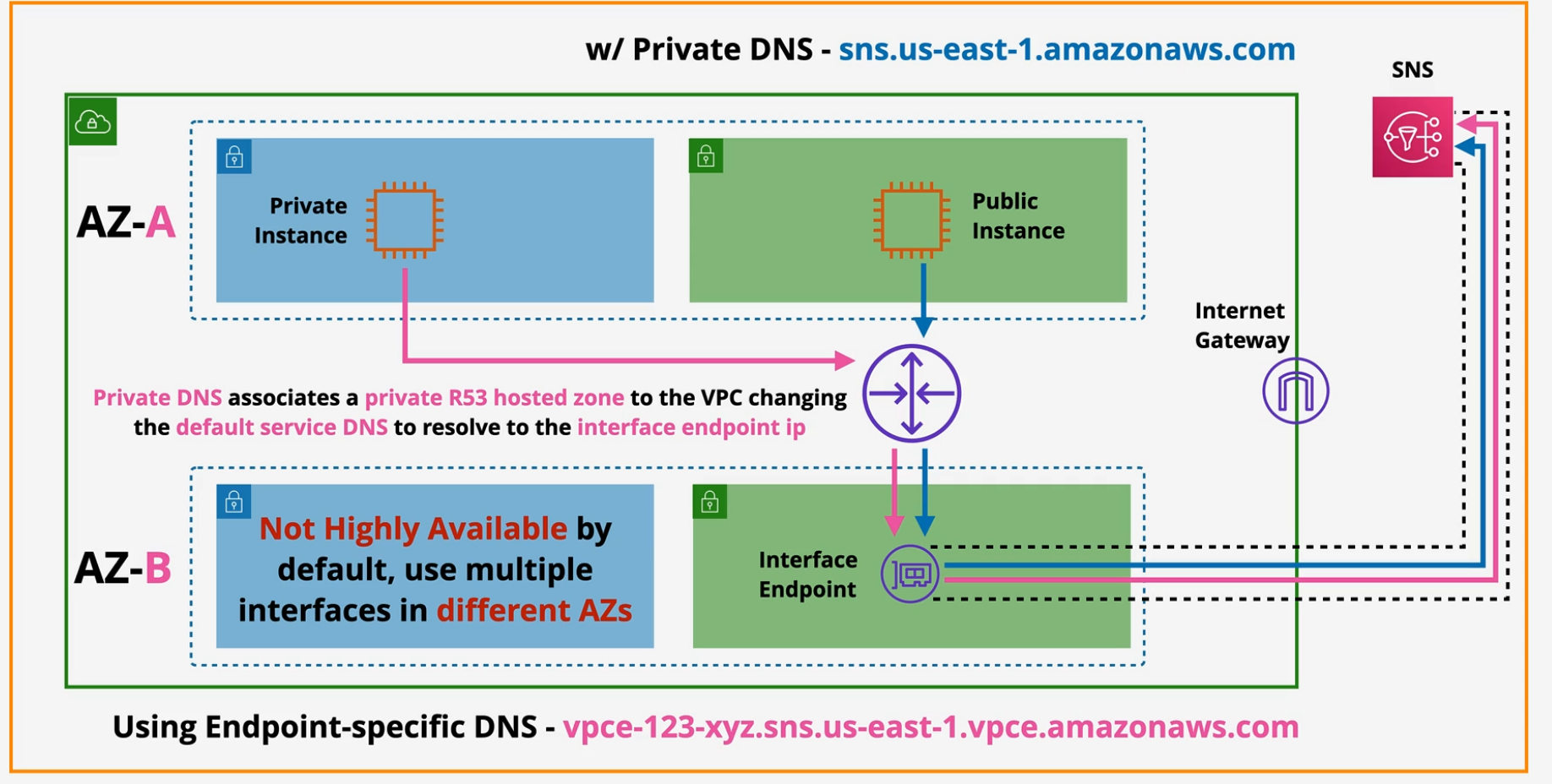
VPC Endpoints - Interface
Interface endpoints provide private access to AWS public services.
- historically used for anything NOT S3 and DynamoDB --- but S3 is now supported.
- these are added to specific subnets - an ENI - making these not HA
- to make these HA, add one endpoint to one subnet PER AZ used in the VPC.
- Network access can be controlled via Security Groups
- Endpoint Policies restrict what can be done with the endpoint over TCP and IPv4 only.
- these use PrivateLink
Interface endpoints use DNS, not route tables.
- endpoint provides a new service endpoint DNS address
- Endpoint Regional DNS
- Endpoint Zonal DNS
Applications can use these or use PrivateDNS that overrides the default DNS for these services.
Things to remember:
- Interface uses DNS and Private IP address
- Gateway uses routing
Demo - Accessing S3 using Gateway Endpoint
Demo
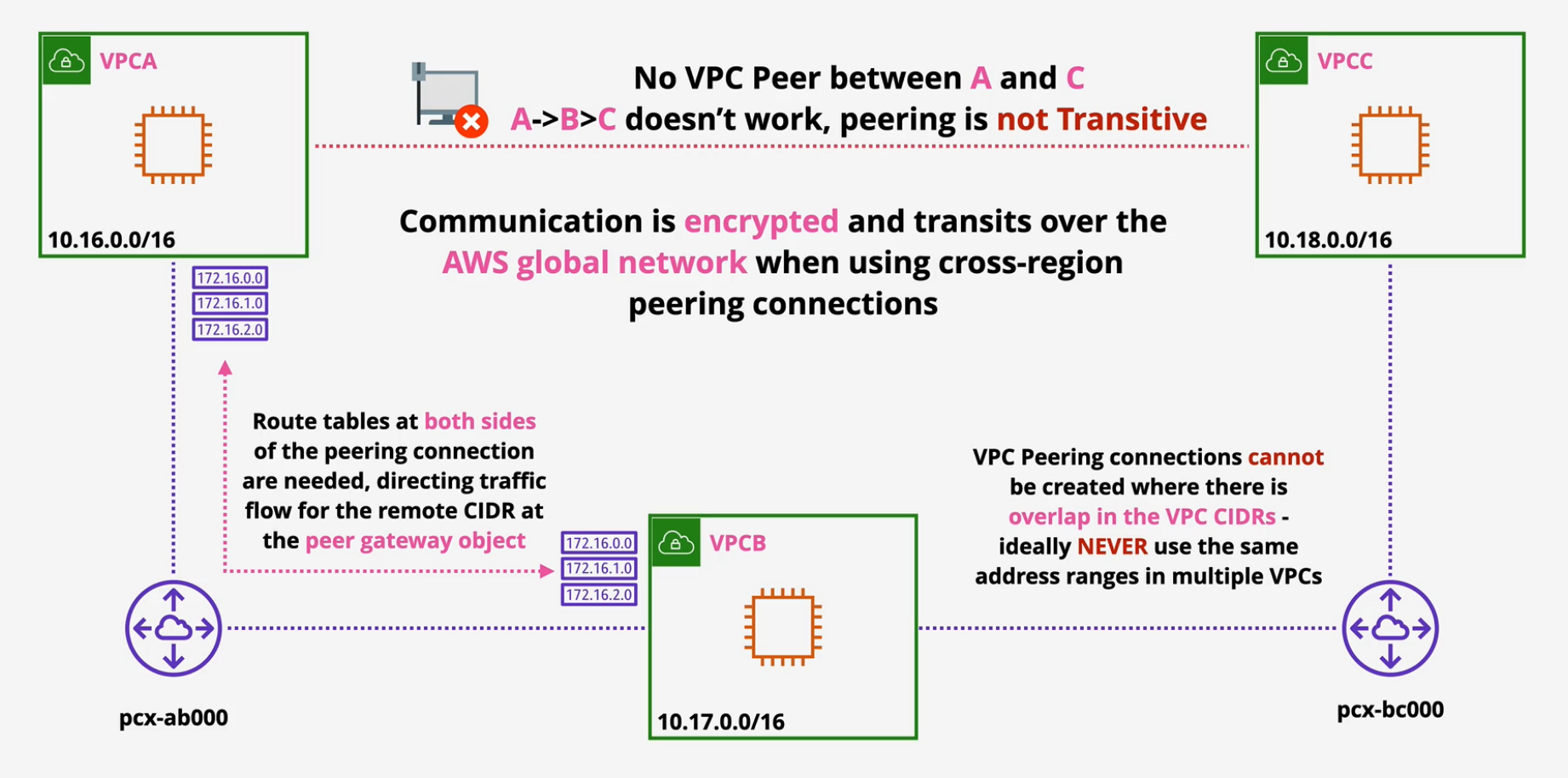
VPC Peering
Direct Encrypted network link between two VPCs
- works in same and cross region and same and cross-account.
- Public Hostnames resolve to private IPs.
- Same region SGs can reference peer SGs - different regions need to use IP ranges or addresses
VPC peering only connects two VPCs This is not transitive. A-B and B-C does not A-C - need a third pair or a transit gateway.
Route tables, SGs and NACLs are needed. Important - IPv4's CIDRs cannot overlap