2. Entra ID
Essentials
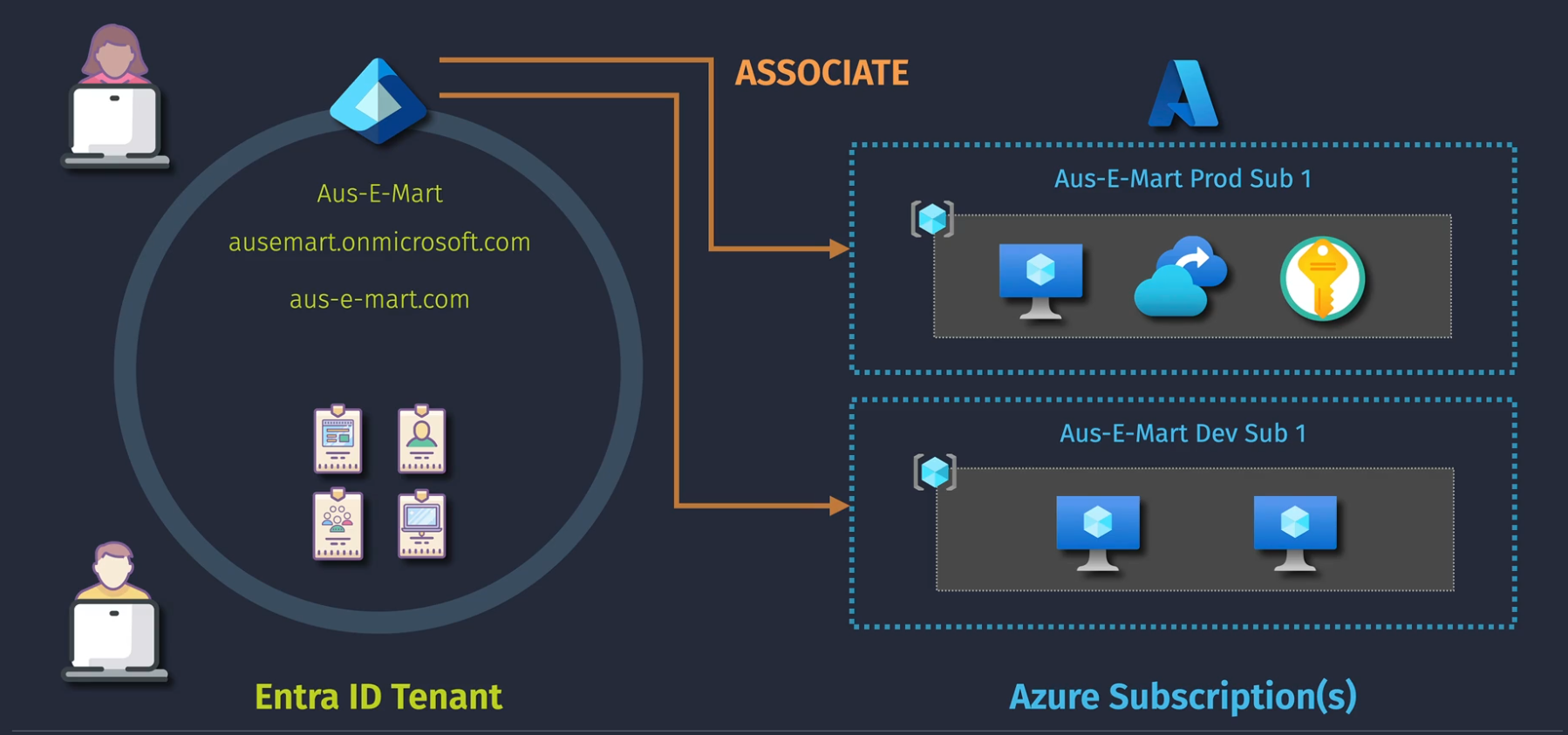
Subscriptions are tied to one and only one Entra ID Tenant
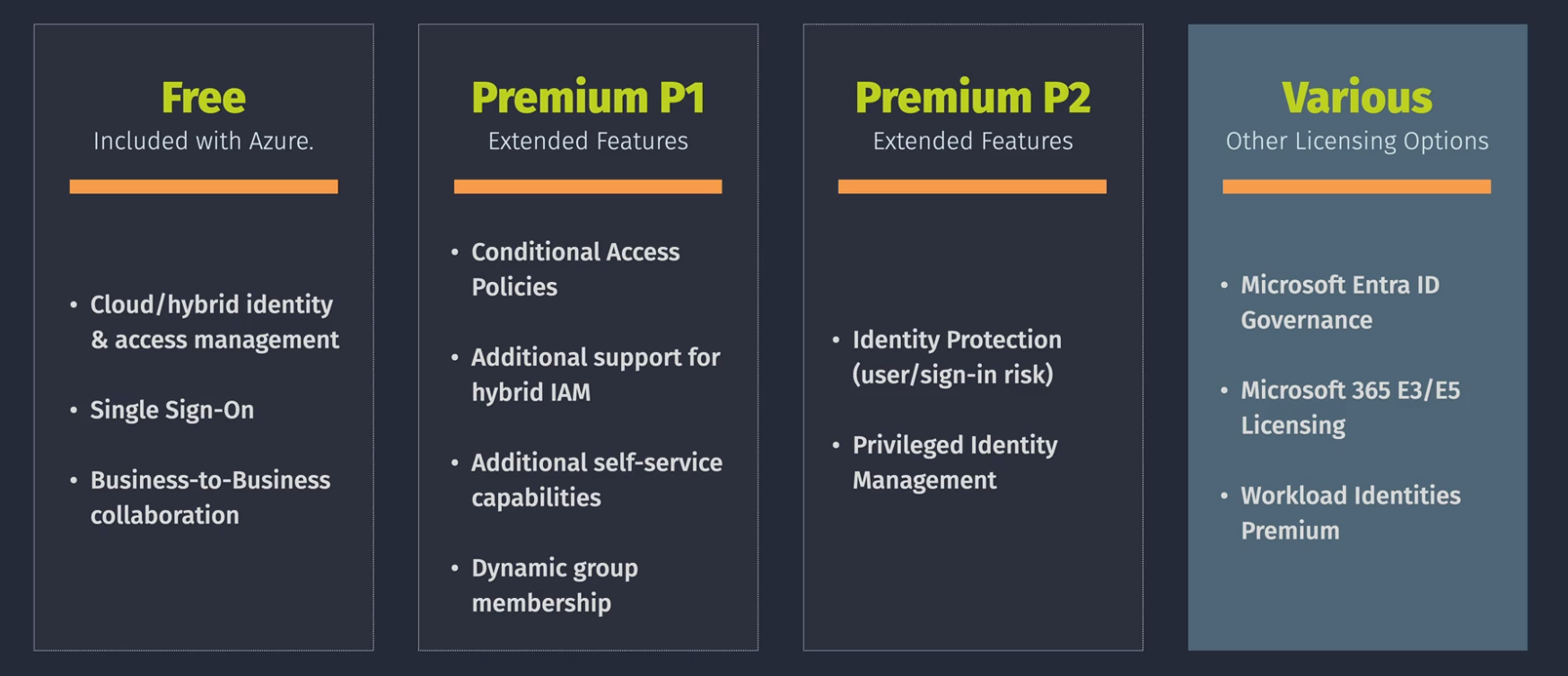
 Extended features:
Extended features:
Entra ID Licensing
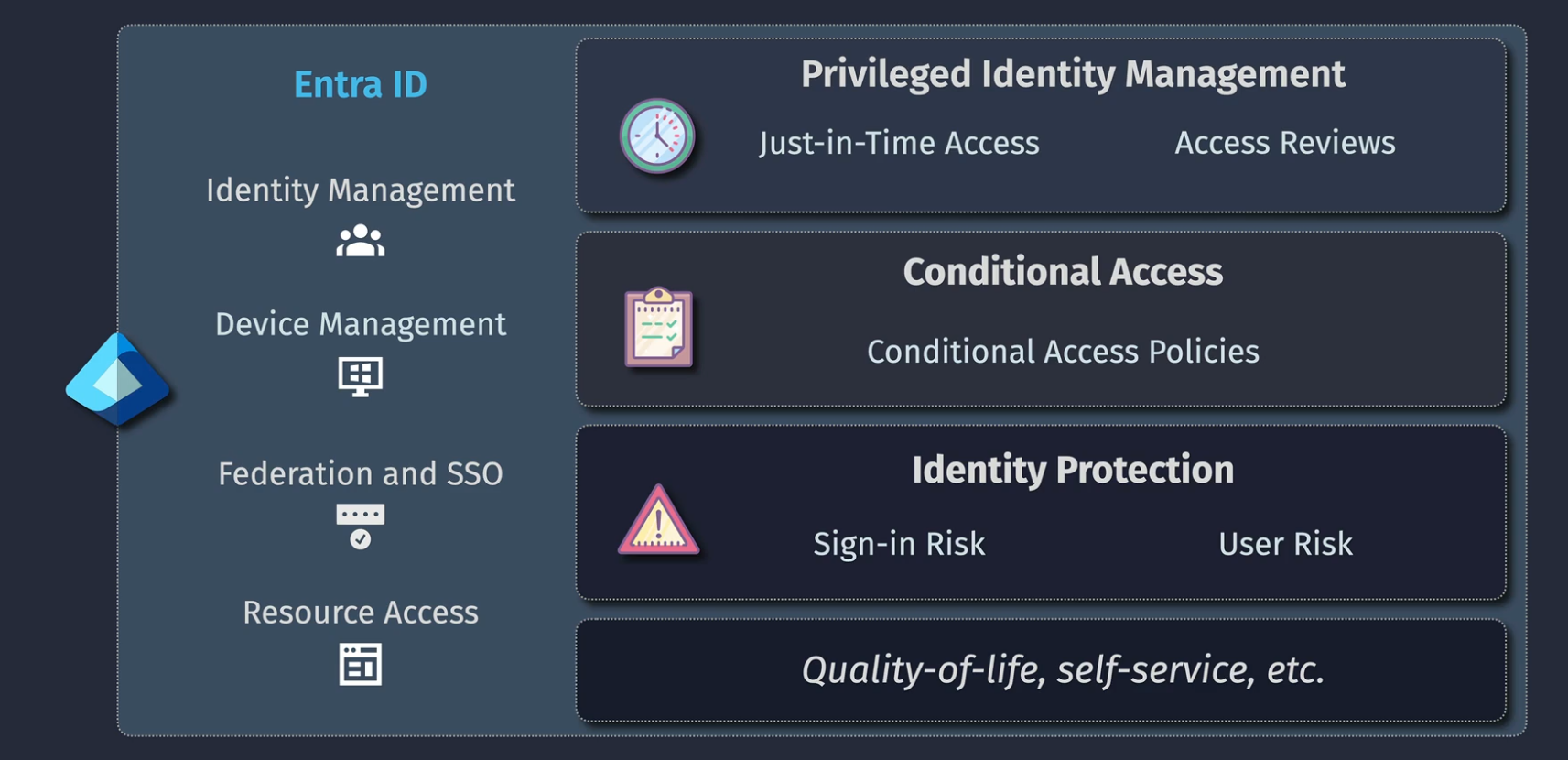
Managing Entra ID
3 ways:
- portal.azure.com
- entra.microsoft.com
- admin.microsoft.com
Free subscription
Sometimes you can get a dev account or a free subscription that will give you credit for a month or so to learn. You can turn on trials for a month or so.
Additional Tenants
You need a paid Entra ID tenant to create additional tenants.
Subscriptions
When you click on a subscription, you will see on the Overview page the directory that the subscription is associated with.
Non Prod:
Production:
Budgets
Domains
You start out with something like in the screenshots above (dupo24msn@onmicrosoft.com) and can use your own domain as shown below:
You will need to own your own domain and then enter in a txt record to prove that you own that domain name.
Entra ID User Identities
Users are a type of identity within Entra ID
If all you have are Users in Entra ID, you have cloud identities. Entra ID - User Identities Active Directory synched - sychronized identities Google, Facebook - guest identities
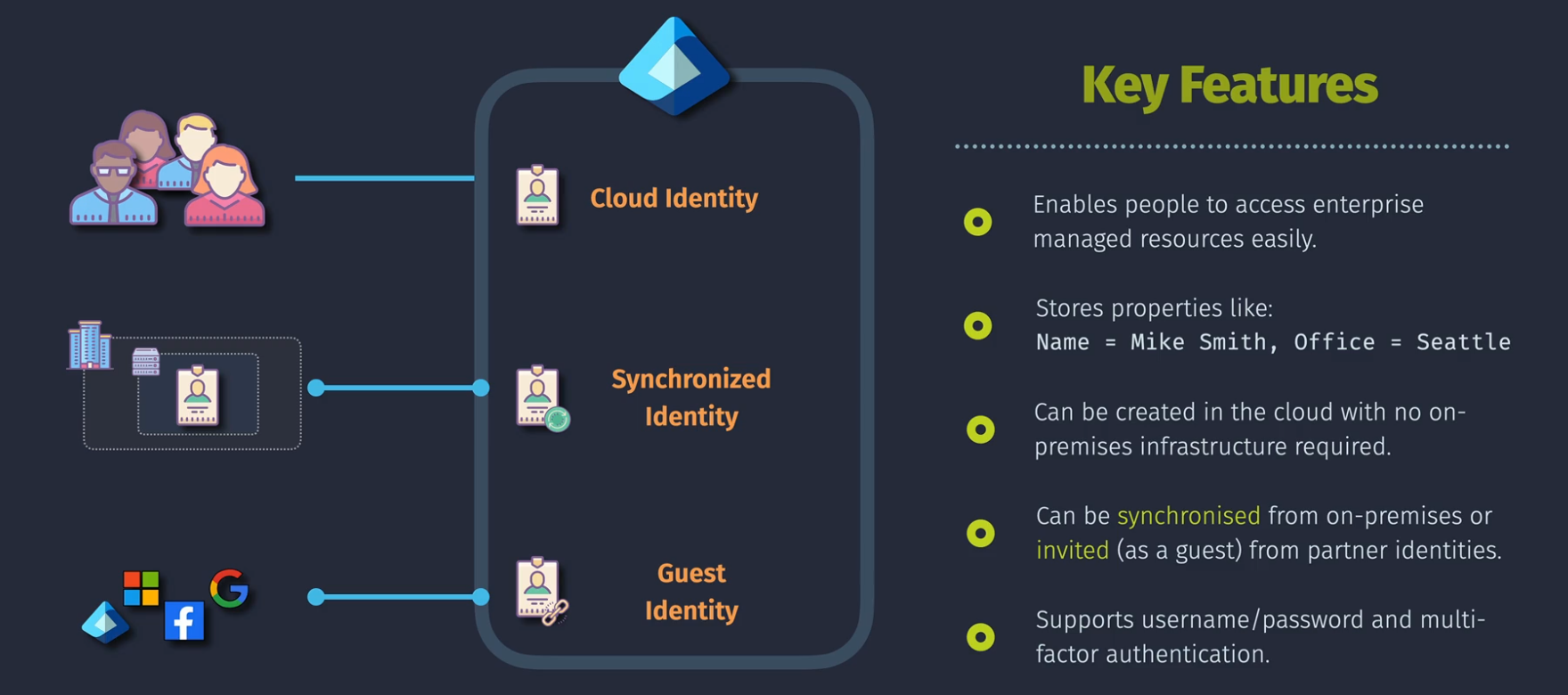
Deletion
Recycle bin type deletion - soft delete
Bulk Actions
- Create
- Invite
- Delete
You get a CSV template to fill out and can upload
Entra ID Application Identities
Human users aren't the only things that need access. Applications need access too. Applications are then authenticated and then after authentication, are authorized to access resources (SQL, VMs).
The application might need access to Entra ID or Users in our Entra ID might need to access the application as well.
The application can then authenticate via a secret or via a certificate.
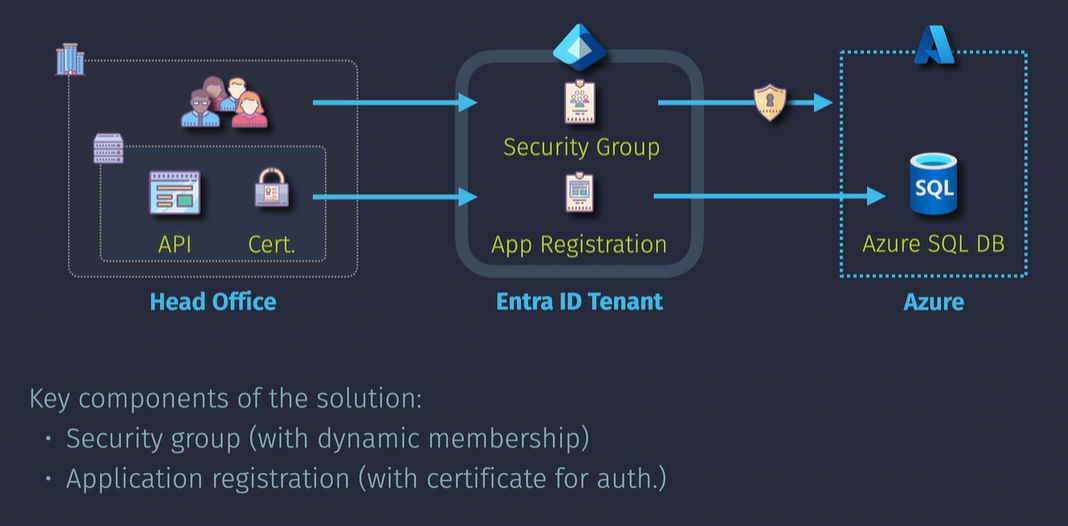
Demo: Register an Application in Entra ID
Create an app registration Create a secret and copy it. Under the authentication tab, there is an option for Supported Account Types, which allows this application to be uses across other Entra ID tenants or your own single Entra ID tenant.
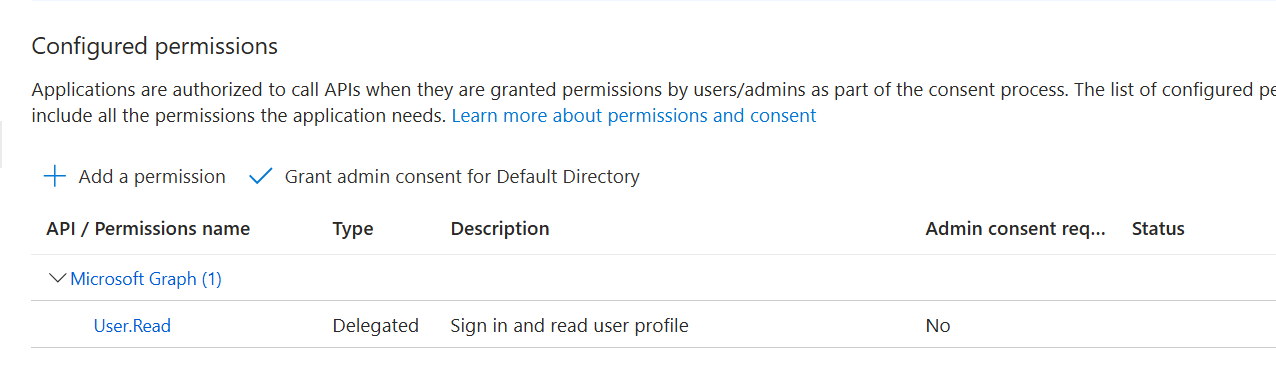
API Permissions
These allow the application to work with certain services and APIs:
Differences between app registration and Enterprise Application
Enterprise applications makes your app registration an entity that users can access. Who can access and how they can access it. Accessed through myapps.microsoft.com.
Managed Identities
What is a managed identity? If an application is hosted in Azure, you can use an appreg or app identity, but you'll need to provide a client id and secret or certificate.
IF the resource exists in Azure, use managed identities instead.
Microsoft can manage the credentials on resources in Azure with Entra ID with a managed identity.
- System assigned - single Azure resource - vm01 - once that vm is removed, the system assigned identity is removed.
- user assigned - multiple Azure resources - can be used on vm01, vm02, vm03, and when you remove vm01 and create vm04, the identity persists
Demo Configure a System Managed identity
Build those resources
You will be deploying a VM and a system assigned managed identity to manage that resource.
-
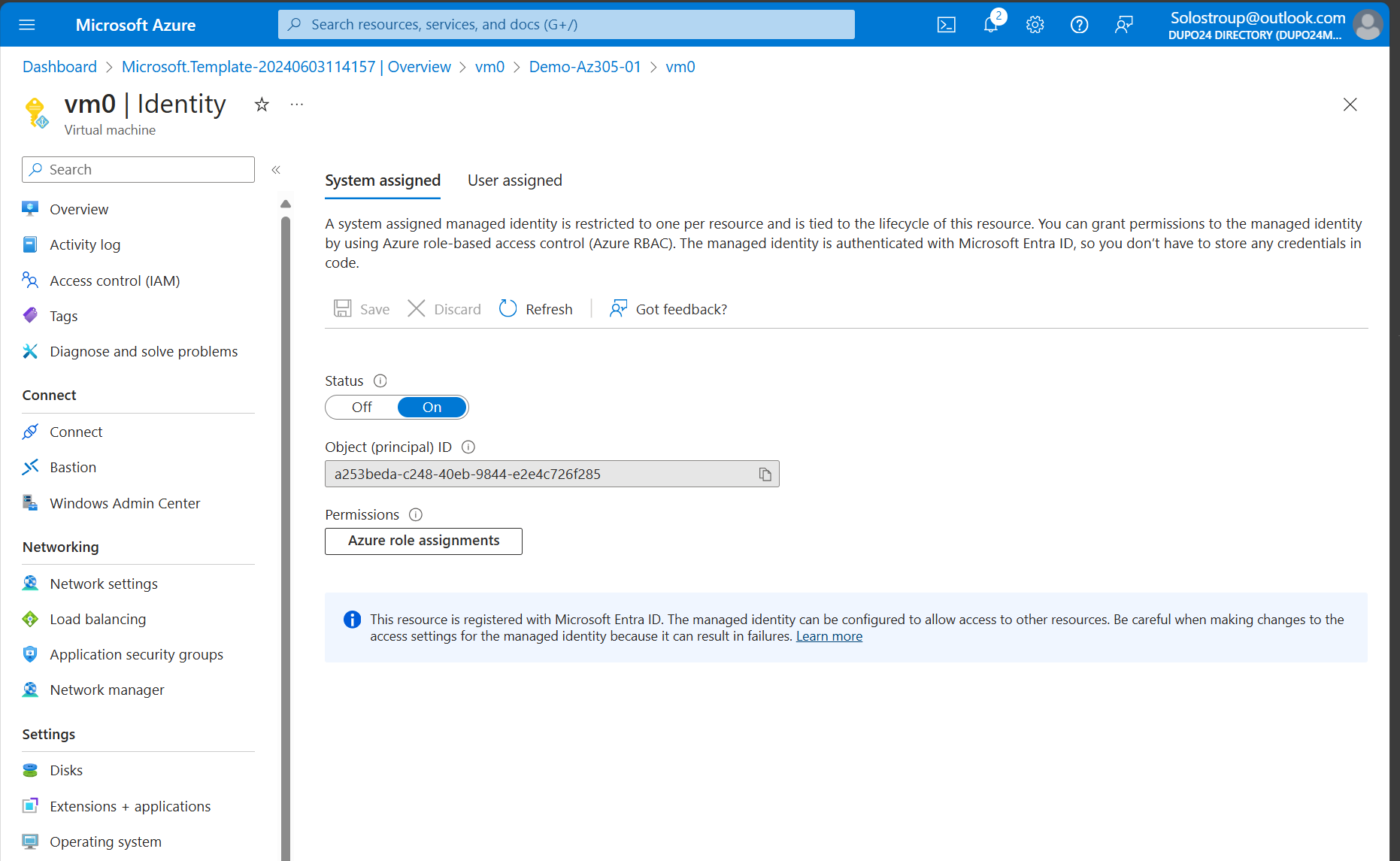
Browse to the machine
-
Go to Identity on the VM and toggle the system managed identity to ON.
-
Go to your app reg you created (Solos 305 App) and create a new secret
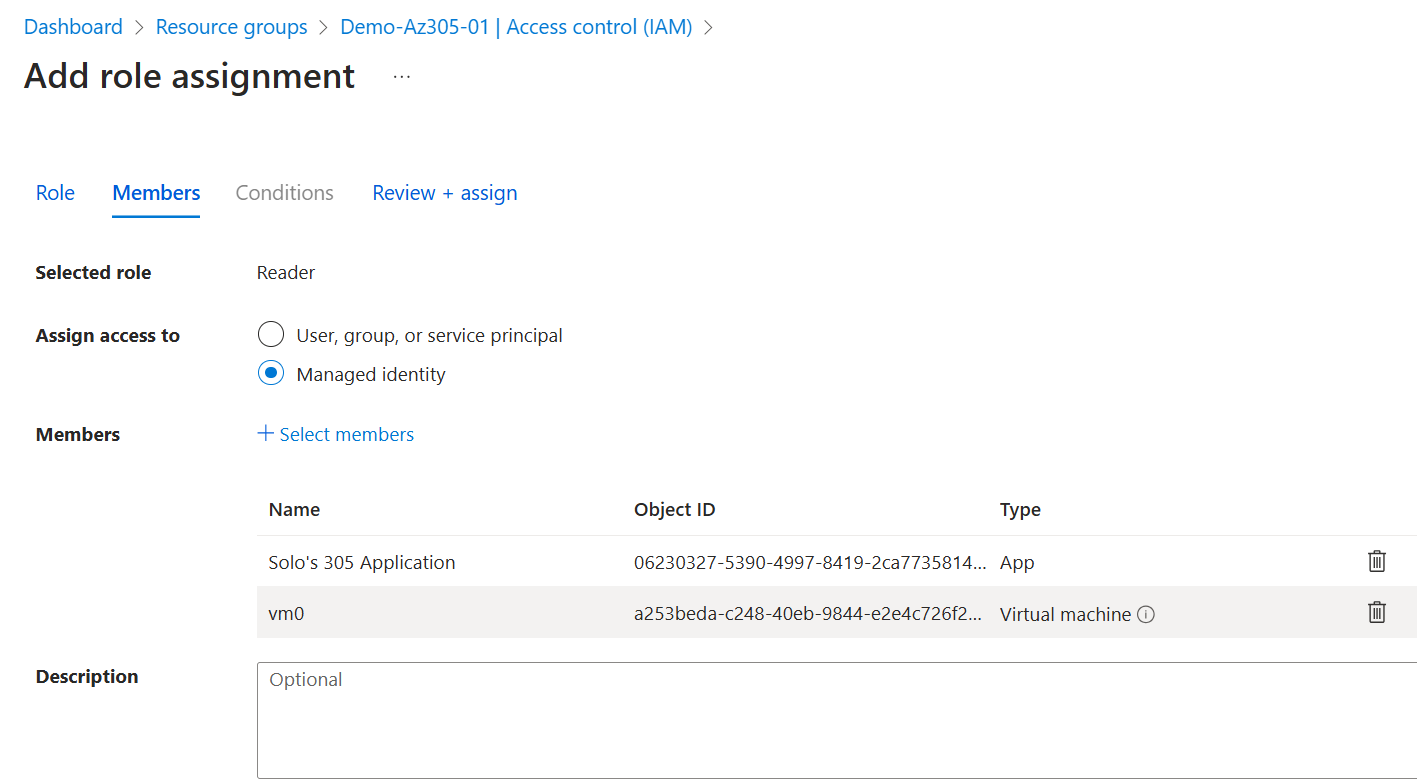
-
Add a reader role to the RG your resources were created in:
-
Log into the VM and open up powershell
-
run
az login --service-principal -u <clientid> -p <secret> -tenant <tenantid> -
This will allow you to log in using the app registration, but you're passing in a username and password
-
Run
az login --identityand notice that this works the same without the client id and secret via the managed identity. -
Delete the RG to clean up.
Demo: Create a managed identity
Build those resources, select two VMs instead of one
You will be deploying two VMs and a user assigned managed identity to manage those resources.
- Search for managed identity and create.
- Navigate to the machine, and add the managed identity.
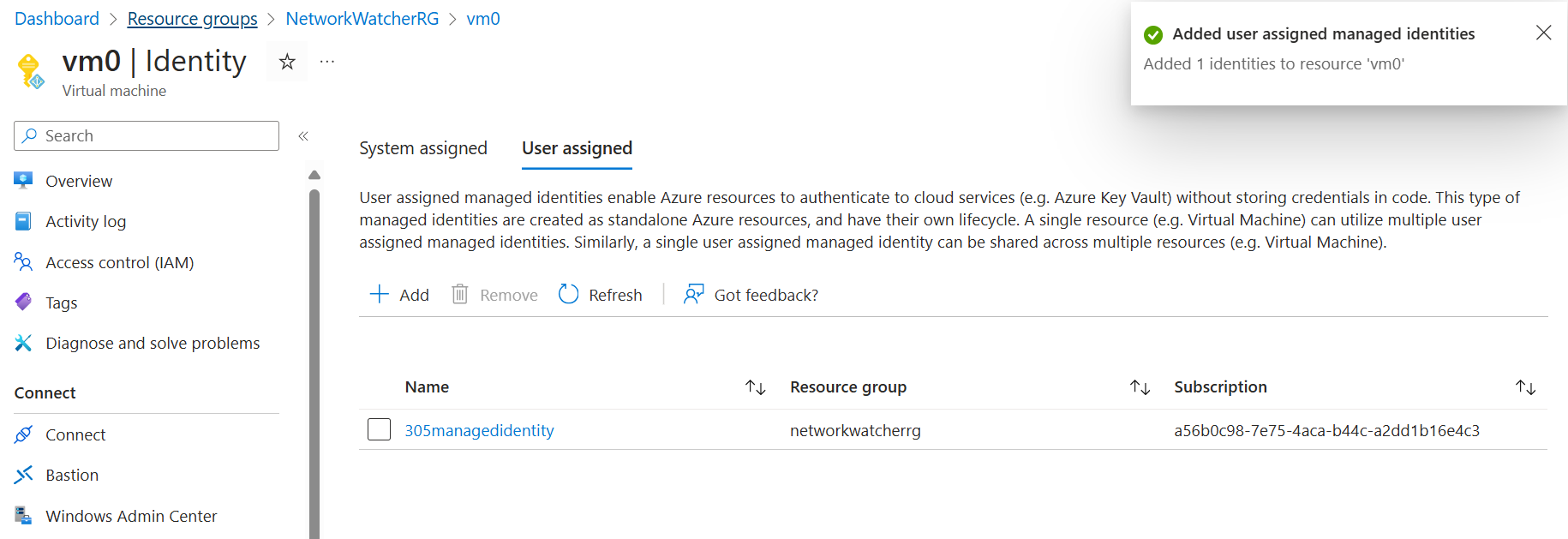
- You can then add this to the other machine - or as many machines as you need to.
- Deleting a machine doesn't delete the managed identity. You can then add the role assignment to this managed identity - like if you want that managed identity to access an entire subscription.
Entra ID Groups
-
Reduce administrative tasks - you can add groups with permissions rather than individual users.
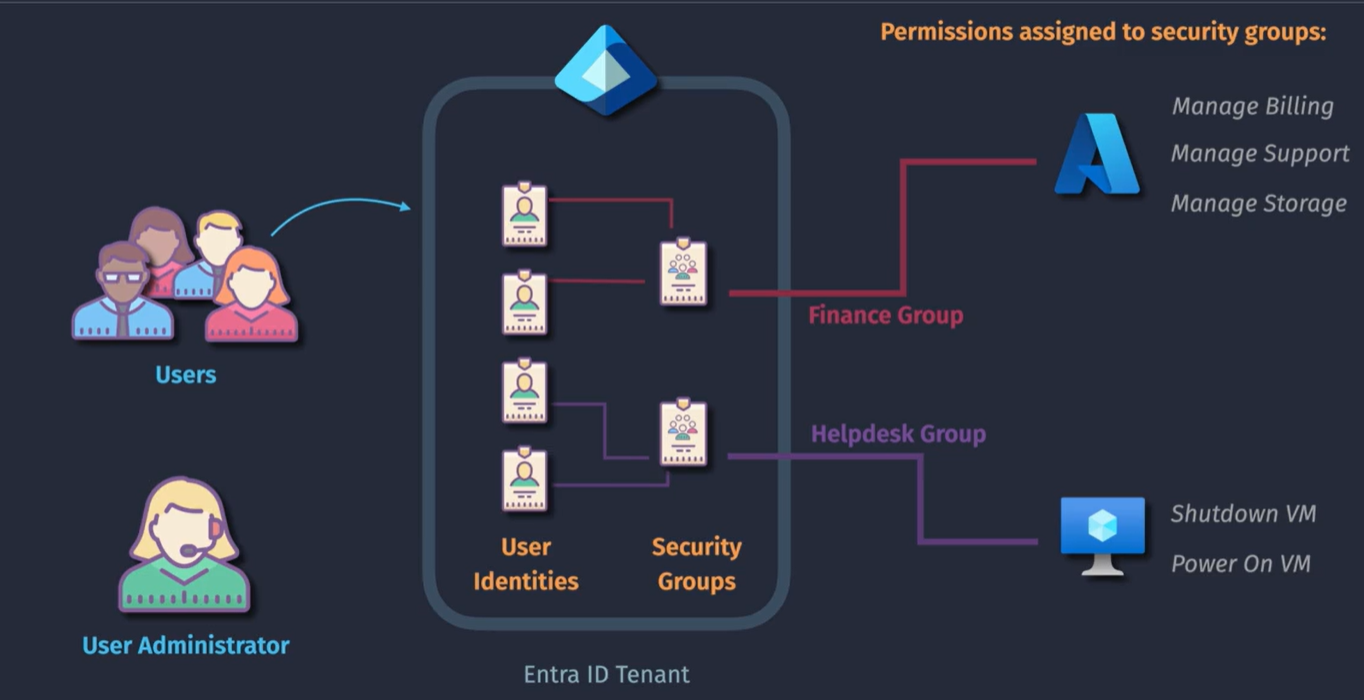
-
Self service capabilities - the leader of the team can be the owner and can manage their own membership to that group.
-
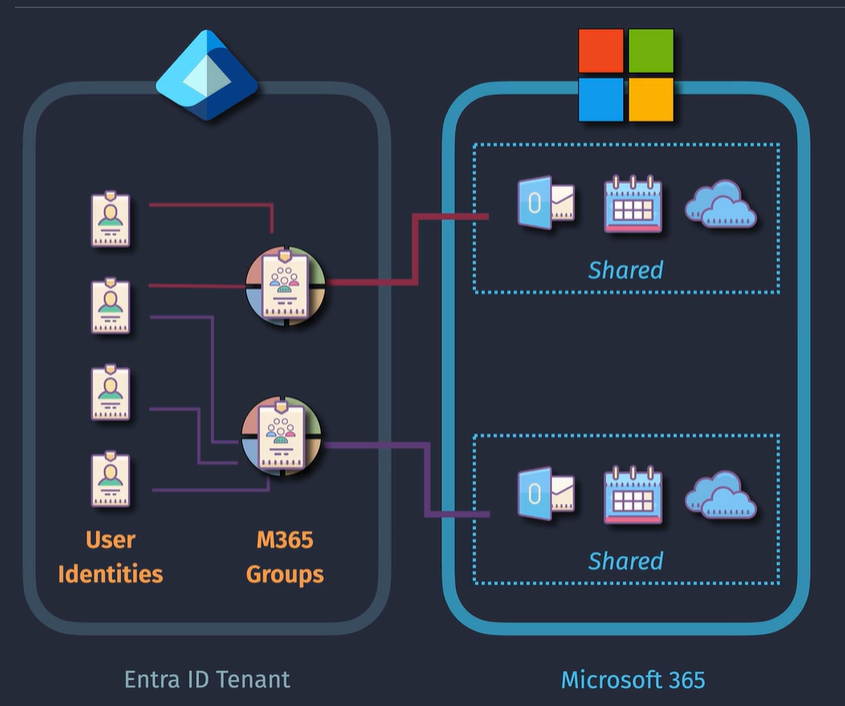
You can also use dynamic user groups to build groups based on common attributes such as location, etc.
-
additional features such as expiration, sensitivity labels
-
members can be assigned manually or by the Entra with dynamic groups
Demo: Creating a group
You can create a security group or a M365 group Add a group, add an owner, add members Check your expiration settings, set up an email, etc.
Demo: Entra ID Licensing
Can be provisioned in Azure or in the Office portal Licenses can fail because of missing attributes on the users such as location. Can assign licenses to users or groups. Reprocess in case license provisioning is failing.
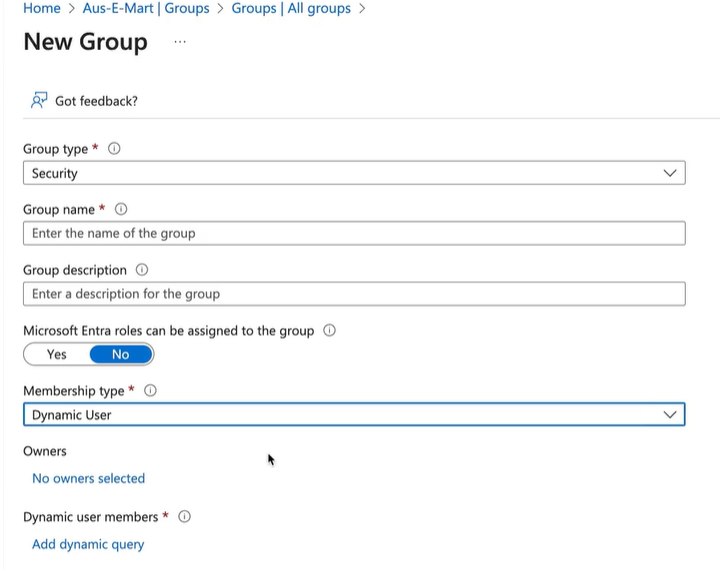
Entra ID Dynamic Groups
Requires P1 Licensing
A dynamic group can be created based on a membership rule. (user.department -eq "Marketing") for example
Can be for devices or users but not both
Cannot manually add a user to a group that is dynamic.
 Can validate users
This flattens out a group - can add multiple groups to avoid nesting issues.
Can validate users
This flattens out a group - can add multiple groups to avoid nesting issues.
Entra ID Administrative Units - AU's
The problem:
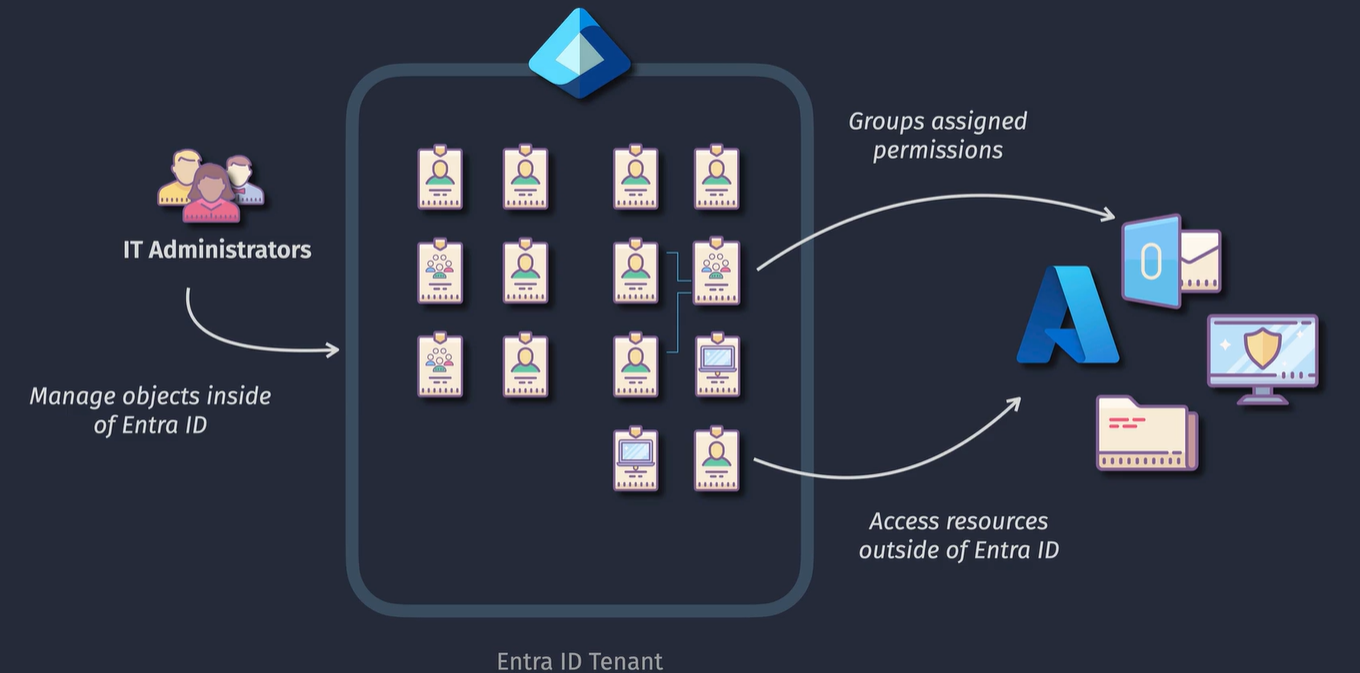
The solution:
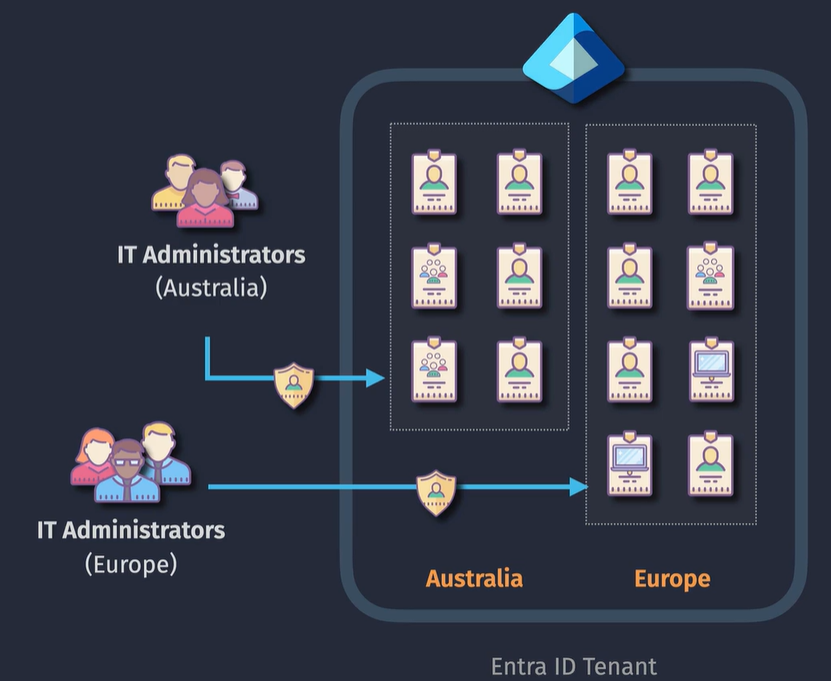
- Can include a mix of users, group or devices
- membership can be assigned or dynamic
- you can have objects exist in multiple AUs at the same time
- Permissions do not apply to the individual membors
- Cannot have nested AUs within other AUs
Restricted Management AUs
Denies administration to certain users or groups
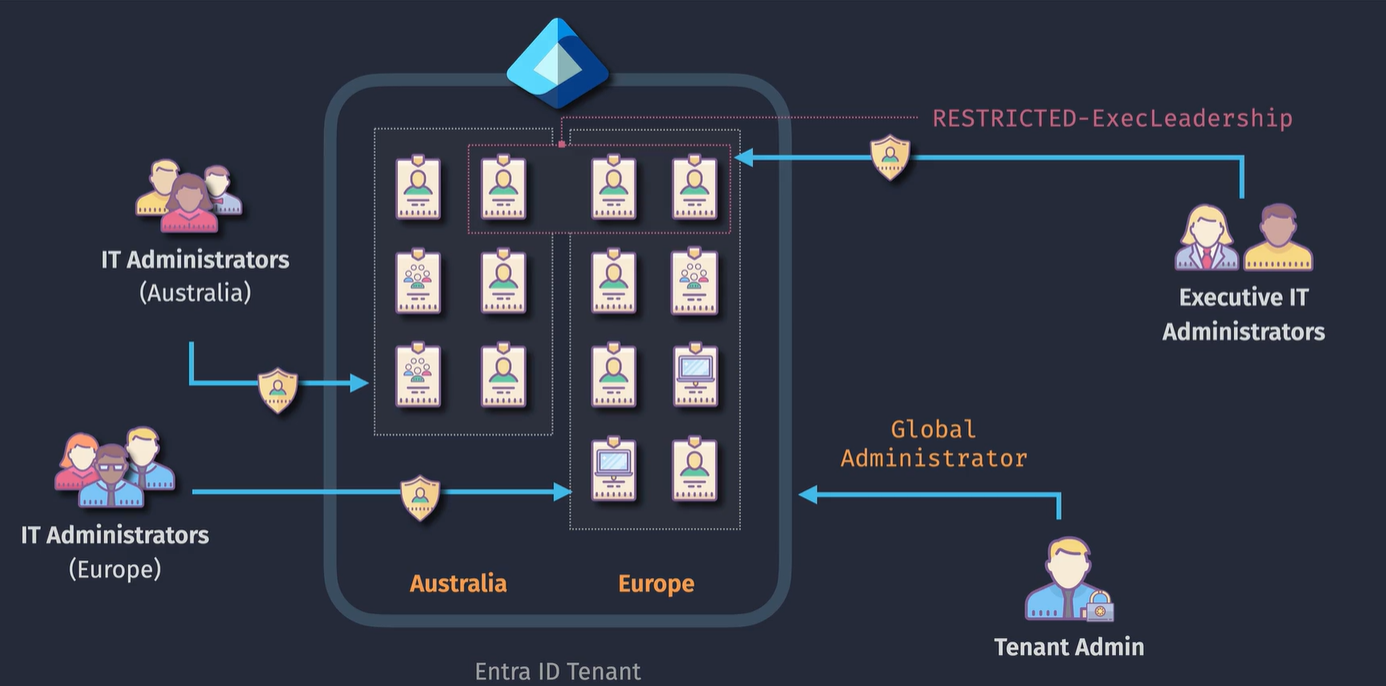
Demo: Administrative Units
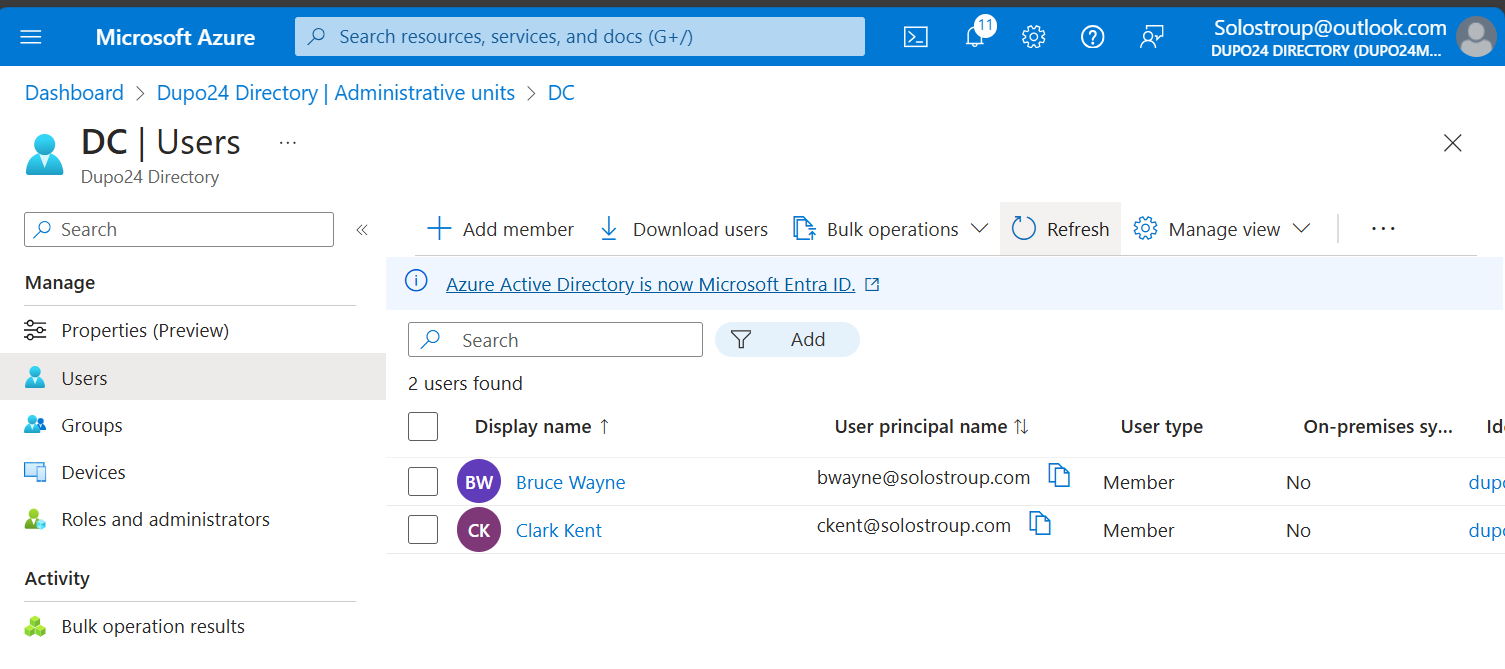
Case Study